[ad_1]

Security researchers warn that tens of thousands of photovoltaic (PV) monitoring and diagnostic systems are accessible on the public web, making them potential targets for hackers.
These systems are used for remote performance monitoring, troubleshooting, system optimization and other functions enabling remote management of renewable energy generating units.
Exposed Sensitive Information
Cyble Threat Analysts scoured the web for PV services exposed to the Internet and found 134,634 products from various vendors, including Solar-Log, Danfoss Solar Web Server, SolarView Contec, SMA Sunny Webbox, SMA Cluster Controller, SMA Power Reducer Box, Kaco New Energy & Web, Fronis Datamanager, Saj Solar Inverter and ABB Solar Inverter Web GUI.
It is important to note that exposed assets are not necessarily vulnerable or misconfigured in a way that attackers can interact with them.
However, Cyble’s research shows that unauthenticated visitors can glean information, including parameters, that could be used to mount an attack.
The report also points out that vulnerabilities have been found and reported for the above products and there is proof-of-concept (PoC) exploit code available for several of them, increasing the likelihood of attacks against systems running an older firmware version.
Even when PV control systems are properly secured, Cyble points to the risk of information-stealing malware that can collect credentials for these tools.
active operation
Exploitation of photovoltaic system vulnerabilities that Cyble has found exposed online has happened recently, with hackers scanning the web for vulnerable devices to add to botnets.
For example, CVE-2022-29303, an unauthenticated remote command injection vulnerability affecting Contec SolarView system was used by a relatively new Variant Mirai looking for new systems to increase its Distributed Denial of Service (DDoS) power.
Cyble’s scans found 7,309 SolarView devices exposed to the internet worldwide, while another report from VulnCheck today discovered 425 instances of Contec’s SolarView that are running a vulnerable firmware version.
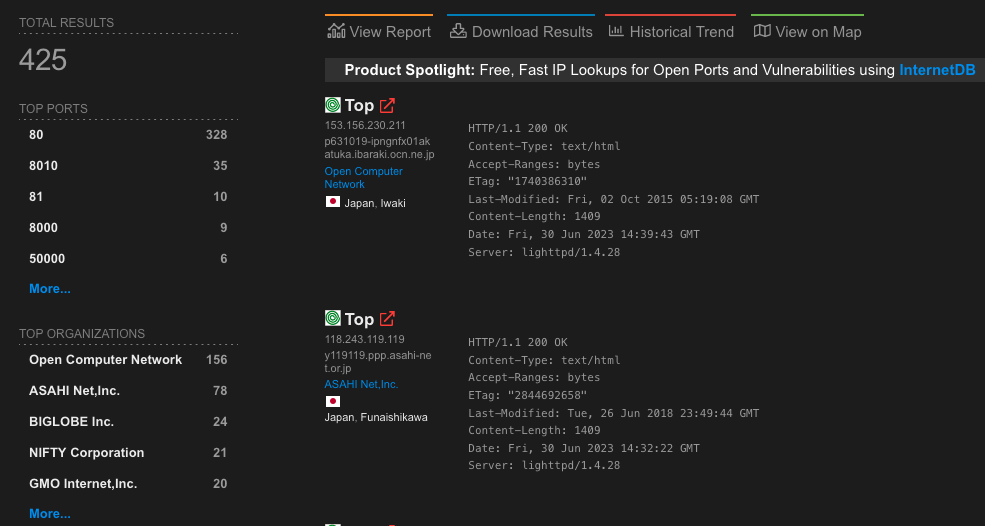
VulnCheck’s report also highlights another recently discovered unauthenticated remote code execution bug affecting the same product, tracked as CVE-2023-23333, for which multiple exploits exist in the public space.
Systems of this type often face a degree of neglect in terms of maintenance and upgrades, which gives attackers good chance of success when they exploit fairly recent vulnerabilities.
If PV system administrators need to expose the interfaces for remote management, they should at least use strong, unique credentials, enable multi-factor authentication when available, and keep their systems up to date. Separating equipment from its own network also counts as a good defense.
[ad_2]
Source link
