[ad_1]

A joint cybersecurity advisory from the German Federal Office for the Protection of the Constitution (BfV) and the National Intelligence Service of the Republic of Korea (NIS) warns against Kimsuky’s use of Chrome extensions to steal target’s Gmail emails.
Kimsuky (aka Thallium, Velvet Chollima) is a North Korean threat group that uses spear phishing to conduct cyber espionage against diplomats, journalists, government agencies, university professors and politicians. Initially focused on targets in South Korea, threat actors have expanded their operations over time to target entities in the United States and Europe.
THE joint security council was published to warn of two attack methods used by the hacking group – a malicious Chrome extension and Android apps.
While the current campaign targets people in South Korea, the techniques used by Kimsuky can be applied globally, so raising awareness is essential.
Steal Gmail emails
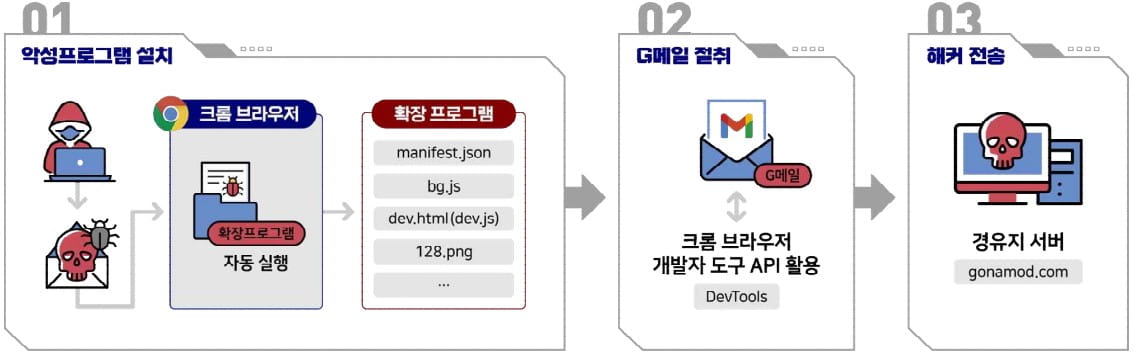
The attack begins with a spear-phishing email urging the victim to install a malicious Chrome extension, which will also install in Chromium-based browsers, such as Microsoft Edge or Brave.
The extension is named “AF” and is only visible in the list of extensions if the user enters “(chrome|edge|brave)://extensions” in the browser’s address bar.
Once the victim visits Gmail through the infected browser, the extension automatically activates to intercept and steal the victim’s email content.
The extension abuses the Devtools API (Developer Tools API) on the browser to send the stolen data to the attacker’s relay server, stealthily stealing their emails without breaking or circumventing account security protections.
This isn’t the first time Kimsuky has used malicious Chrome extensions to steal emails from hacked systems.
In July 2022, Volexity reported about a similar campaign using an extension named “SHARPEXT”. In December 2018, Netscout reported that Kimsuky was following the same tactic against college targets.
This time, the hashes of the malicious files used by Kimsuky in its latest attacks are:
- 012D5FFE697E33D81B9E7447F4AA338B (manifest.json)
- 582A033DA897C967FAADE386AC30F604 (bg.js)
- 51527624E7921A8157F820EB0CA78E29 (dev.js)
Android Malware
The Android malware used by Kimsuky is called “FastViewer”, “Fastfire” or “Fastspy DEX”, and it has been known since October 2022when seen posing as a security plugin or document viewer.
However, the Korean cybersecurity company AhnLab, reports that threat actors updated FastViewer in December 2022, so they continued to use the malware after its hashes were made public.
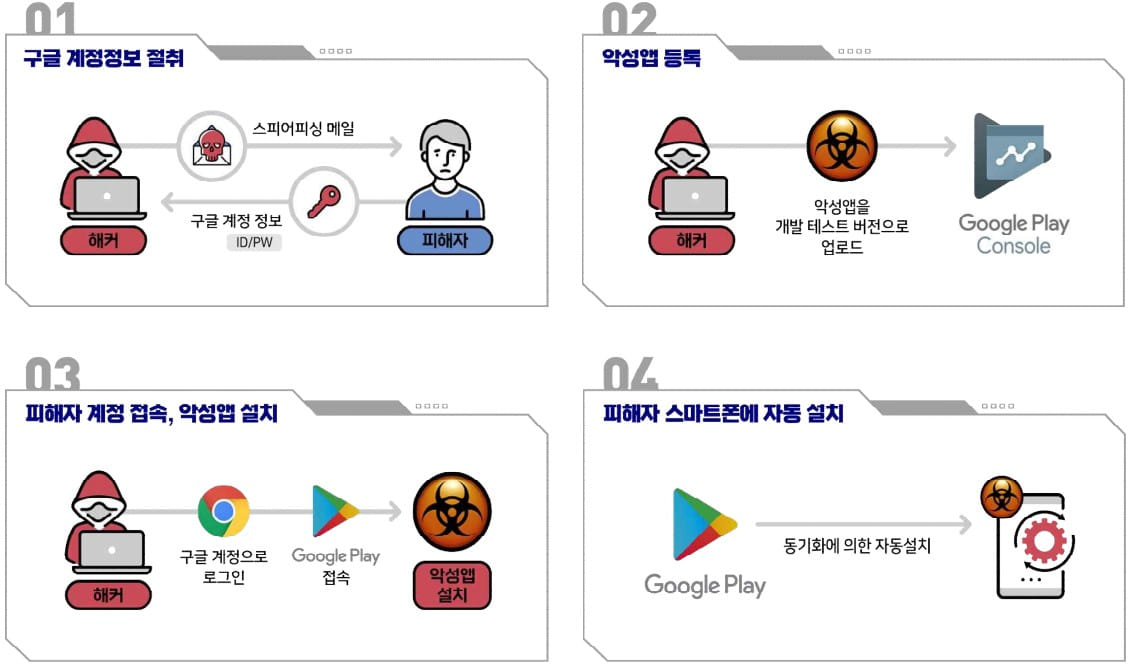
The attack unfolds when Kimsuky logs into the victim’s Google account, which she previously stole through phishing emails or other means.
Next, hackers abuse Google Play’s web-to-phone sync feature, which allows users to install apps on their linked devices from their computer (Play Store website) to install the malware.
The malicious application that the attackers ask Google Play to install on the victim’s device is submitted to the Google Play Console developers’ site for “internal testing only”, and the victim’s device is believed to be added as test target.
This technique wouldn’t work for large-scale infections, but it’s exceptional and quite stealthy when it comes to close-targeting operations like those carried out by Kimsuky.
The Android malware is a RAT (Remote Access Trojan) tool allowing hackers to drop, create, delete or steal files, obtain contact lists, make calls, monitor or send text messages, activate the camera, perform keylogging and display the desktop.
As Kimsuky continues to evolve its tactics and develop more sophisticated methods to compromise Gmail accounts, individuals and organizations should remain vigilant and implement robust security measures.
This includes keeping software up-to-date, being wary of unexpected emails or links, and regularly monitoring accounts for suspicious activity.
[ad_2]
Source link
