[ad_1]

A trojan version of the legitimate ChatGPT Chrome extension is gaining popularity on the Chrome Web Store, racking up over 9,000 downloads while stealing Facebook accounts.
The extension is a copy of the legit popular add-on for Chrome named “ChatGPT for Googlewhich offers ChatGPT integration on search results. However, this malicious version includes additional code that attempts to steal Facebook session cookies.
The extension’s publisher uploaded it to the Chrome Web Store on February 14, 2023, but only started promoting it from March 14, 2023 using Google search ads. Since then, it has averaged a thousand installs per day.
The researcher who discovered it, Nati Tal of Guardio Labs, reports that the extension communicates with the same infrastructure used earlier this month by a similar Chrome add-on which amassed 4,000 installs before Google removed it from the Chrome Web Store.
Therefore, this new variant is considered part of the same campaign, which the operators kept as a backup on the Chrome Web Store when the first extension was reported and removed.
Targeting Facebook accounts
The malicious extension is promoted via advertisements in Google search results, which are highlighted when searching for “Chat GPT 4”.
Clicking on sponsored search results takes users to a fake “ChatGPT for Google” landing page, and from there to the extension’s page on the official Chrome Add-ons store.
Once the victim installs the extension, they get the promised functionality (ChatGPT integration on search results) since the legitimate extension code is still there. However, the malicious add-on also attempts to steal session cookies for Facebook accounts.
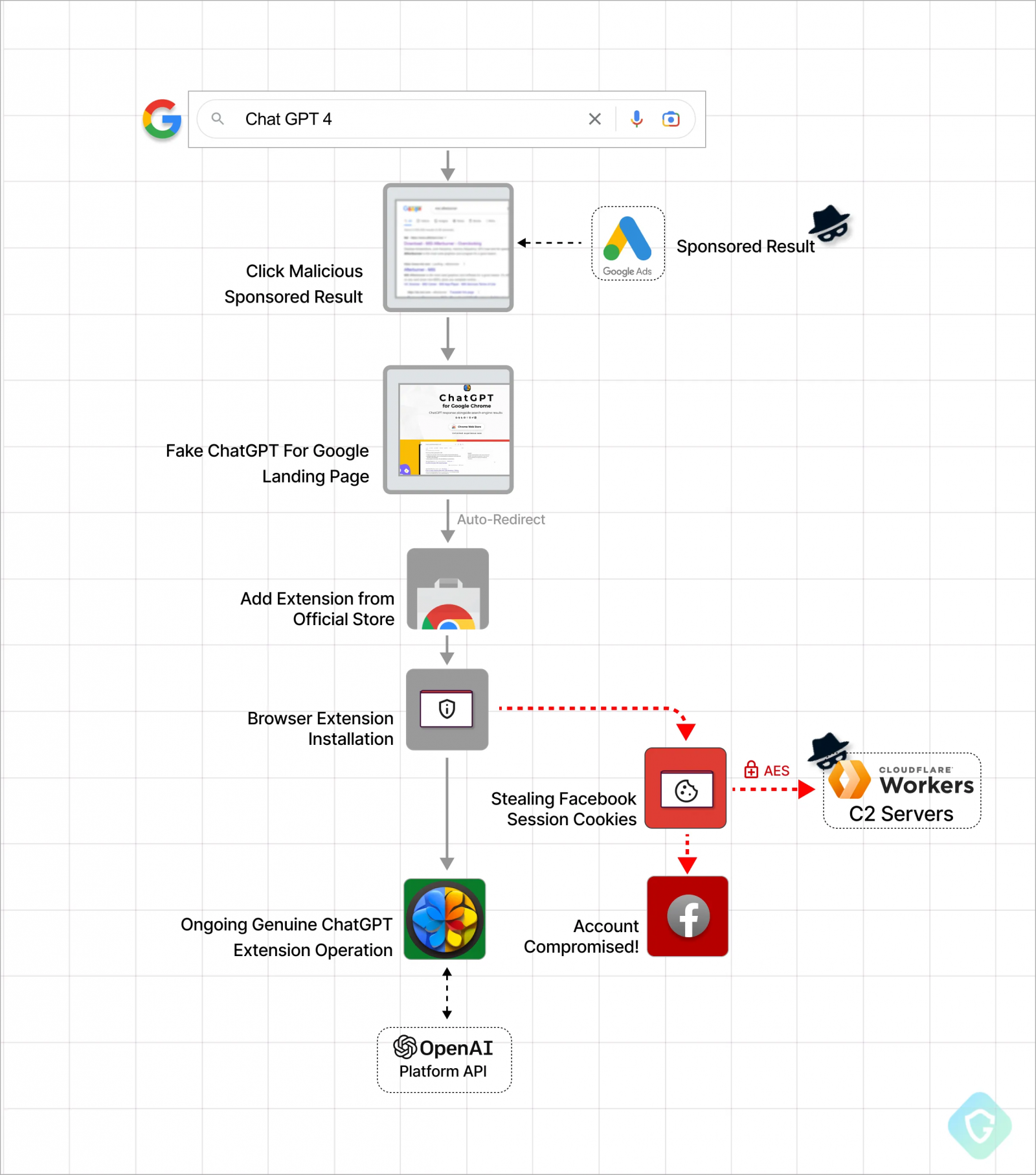
While installing the extension, malicious code uses the OnInstalled handler function to steal Facebook session cookies.
These stolen cookies allow threat actors to log into a Facebook account as a user and have full access to their profiles, including all commercial advertising features.
The malware abuses the Chrome extension API to acquire a list of Facebook-related cookies and encrypts them using an AES key. It then exfiltrates the stolen data via a GET request to the attacker’s server.
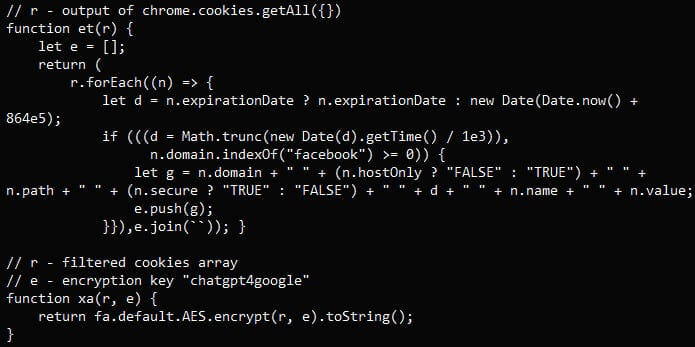
“The list of cookies is encrypted with AES and attached to the X-Cached-Key HTTP header value,” explains the Guardio Labs Report.
“This technique is used here to try to get cookies out without any DPI (Deep Packet Inspection) mechanism triggering alerts on packet payload.”
Threat actors then decrypt the stolen cookies to hijack their victims’ Facebook sessions for malicious advertising campaigns or to promote prohibited material like ISIS propaganda.
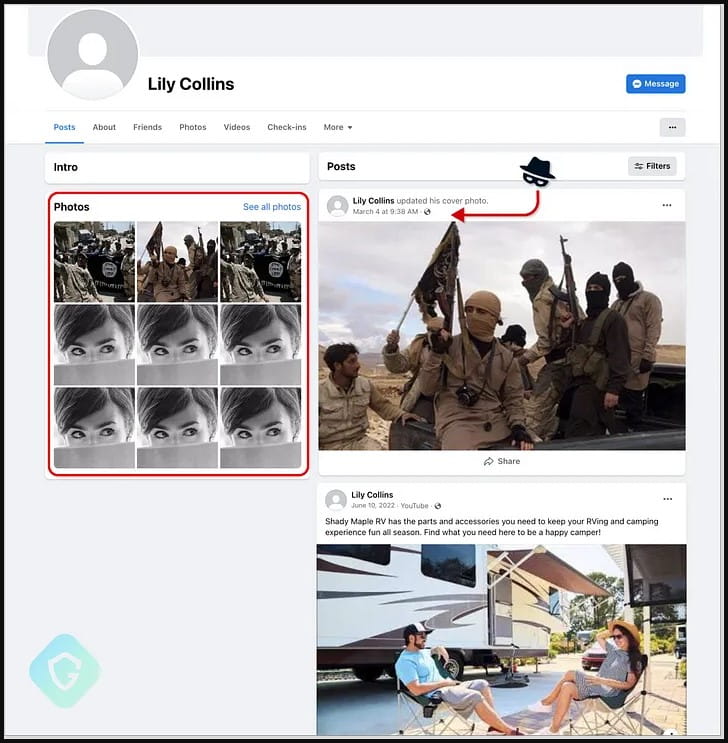
The malware automatically changes login information on hacked accounts to prevent victims from regaining control of their Facebook accounts. It also replaces the profile name and picture with a fake character named “Lilly Collins”.
At present, the malicious Google Chrome extension is still present in the Google Chrome Web Store.
However, the security researcher reported the malicious extension to the Chrome Web Store team, which will likely be removed soon.
Unfortunately, based on the track record, the threat actors likely have a “C” plan via another “parked” extension that could facilitate the next wave of infection.
BleepingComputer contacted Google with further questions about the extension, but a response was not immediately available.
[ad_2]
Source link
