[ad_1]

A new Mirai botnet variant tracked as “V3G4” targets 13 vulnerabilities in Linux servers and IoT devices for use in DDoS (distributed denial of service) attacks.
The malware spreads by brute-forcing weak or default telnet/SSH credentials and exploiting hard-coded flaws to perform remote code execution on target devices. Once a device is hacked, the malware infects the device and recruits it into its swarm of botnets.
The particular malware was spotted in three separate campaigns by researchers at Palo Alto Networks (Unit 42), which said it monitored malicious activity between July 2022 and December 2022.
Unit 42 believes all three waves of attacks come from the same threat actor because the hardcoded C2 domains contain the same string, the shell script downloads are similar, and the botnet clients used in all attacks exhibit identical functions.
V3G4 attacks begin with the exploitation of one of the following 13 vulnerabilities:
- CVE-2012-4869: Running FreePBX Elastix remote command
- Executing Gitorious Remote Commands
- CVE-2014-9727: Executing the remote control of the FRITZ!Box Webcam
- Running the Mitel AWC remote command
- CVE-2017-5173: Remote execution of commands from Geutebruck IP cameras
- CVE-2019-15107: Injection of Webmin commands
- Arbitrary Execution of Spree Commerce Orders
- Running the FLIR thermal camera remote command
- CVE-2020-8515: Running DrayTek Vigor remote command
- CVE-2020-15415: Running DrayTek Vigor remote command
- CVE-2022-36267: Running Airspan AirSpot remote command
- CVE-2022-26134: Executing Atlassian Confluence remote commands
- CVE-2022-4257: C-Data web management system command injection
.png)
After compromising the target device, a Mirai-based payload is dropped onto the system and attempts to connect to the hardcoded C2 address.
The botnet also attempts to terminate a set of processes from a hard-coded list, which includes other competing botnet malware families.
One feature that differentiates V3G4 from most Mirai variants is that it uses four different XOR encryption keys instead of just one, which makes it more difficult to reverse engineer the malware code and decode its functions.
When spreading to other devices, the botnet uses a telnet/SSH forcer that attempts to log in using default or weak credentials. Unit 42 noticed that earlier malware variants used both telnet/SSH brute forcing and exploiting vulnerabilities to spread, while later samples did not use the scanner.
Finally, compromised devices receive DDoS commands directly from the C2, including TCP, UDP, SYN, and HTTP flood methods.
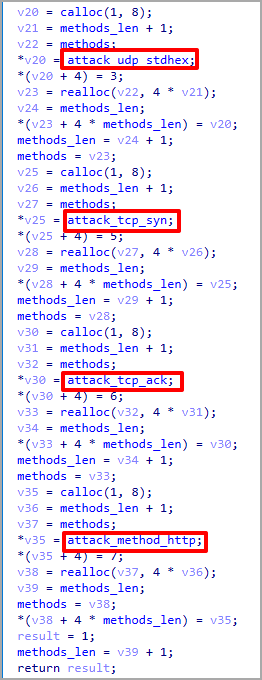
V3G4 likely sells DDoS services to customers who want to disrupt the service of specific websites or online services.
However, this variant has not been tied to any particular service yet.
As always, the best way to protect your devices from Mirai-like infections is to change the default password and install the latest security updates.
[ad_2]
Source link
