[ad_1]

A new malware called “ProxyShellMiner” exploits vulnerabilities in Microsoft Exchange ProxyShell to deploy cryptocurrency miners in a Windows domain to generate profit for attackers.
ProxyShell is the name of three Exchange vulnerabilities discovered and patched by Microsoft in 2021. When chained together, the vulnerabilities allow unauthenticated remote code execution, allowing attackers to take full control of the Exchange server and pivot to other parts of the organization’s network.
In attacks seen by Morphisec, threat actors exploit ProxyShell flaws tracked as CVE-2021-34473 and CVE-2021-34523 to gain initial access to the organization’s network.
Next, threat actors drop a .NET malware payload into the domain controller’s NETLOGON folder to ensure that all network devices are running the malware.
For the malware to activate, it requires a command line parameter which also serves as a password for the XMRig miner component.
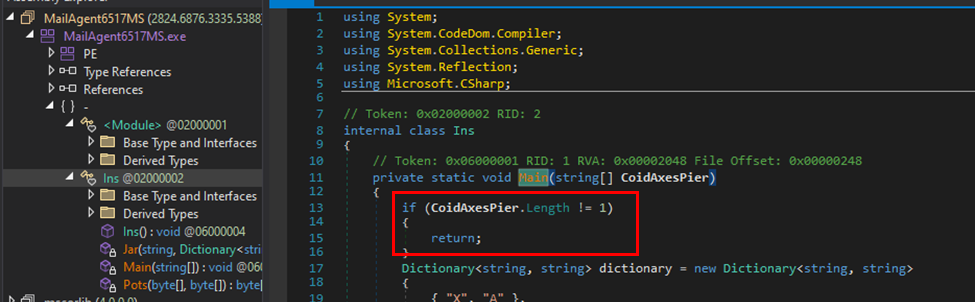
“ProxyShellMiner uses a built-in dictionary, an XOR decryption algorithm, and an XOR key downloaded from a remote server,” describes the Morphisec report.
“Then it uses a C# CSC.exe compiler with ‘InMemory’ compilation settings to run the next built-in code modules.”
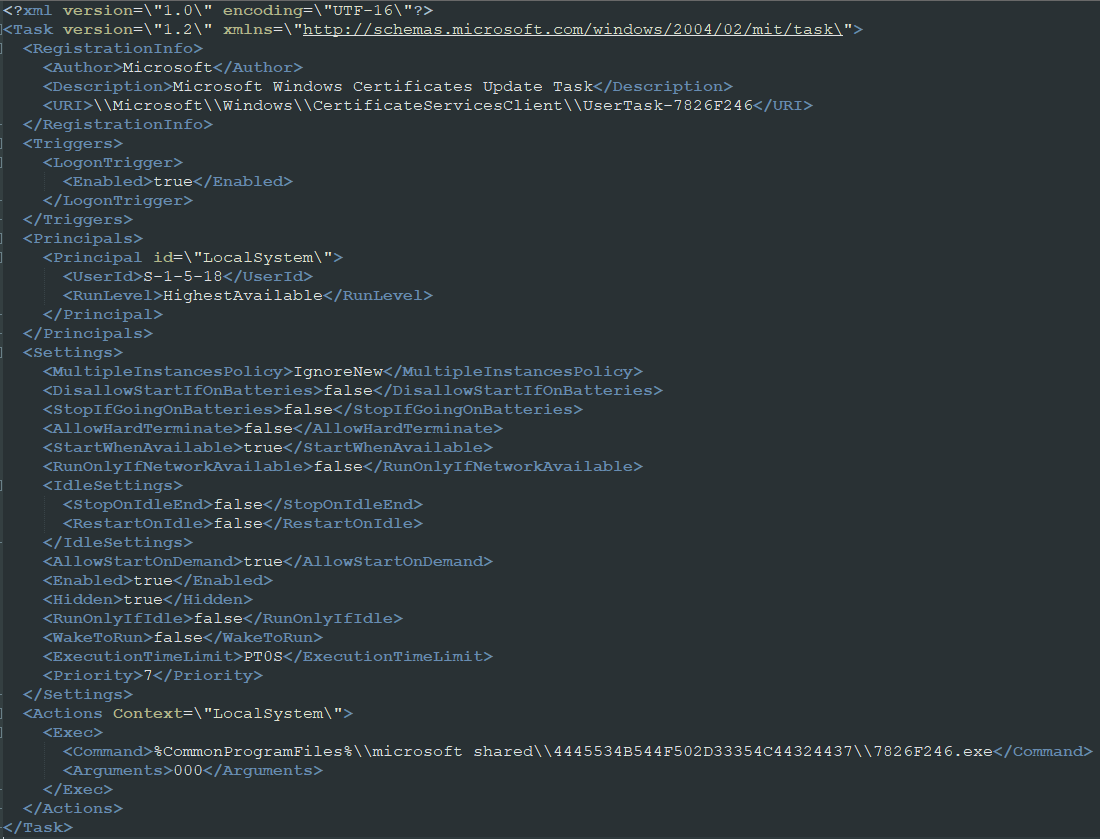
In the next phase, the malware downloads a file named “DC_DLL” and performs .NET reflection to extract the Task Scheduler arguments, XML, and XMRig key. The DLL file is used for additional file decryption.
A second downloader establishes persistence on the infected system by creating a scheduled task that is configured to run when the user logs in. Finally, the second loader is downloaded from a remote resource, along with four other files.
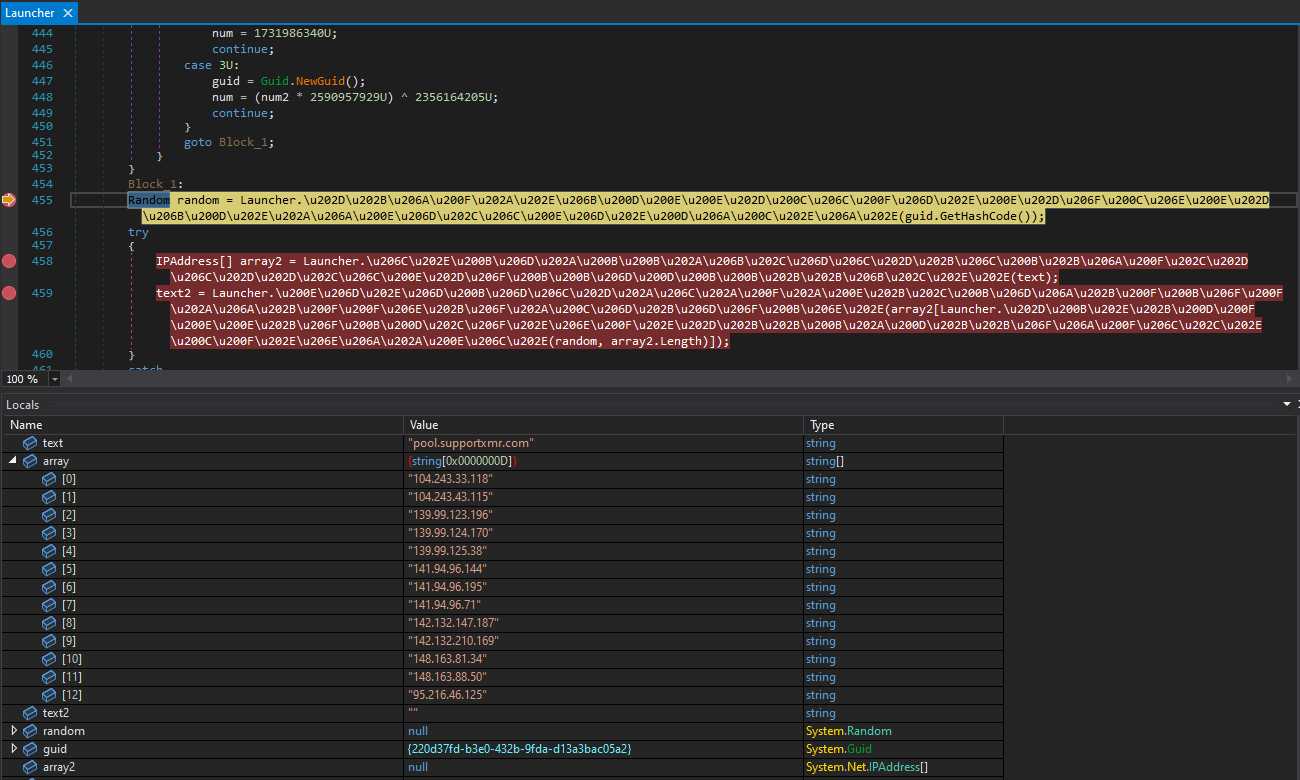
This file decides which browser among those installed on the compromised system will be used to inject the miner into its memory space, using a technique known as “process hollowing”. After that, it selects a random mining pool from a hard-coded list, and mining activity begins.
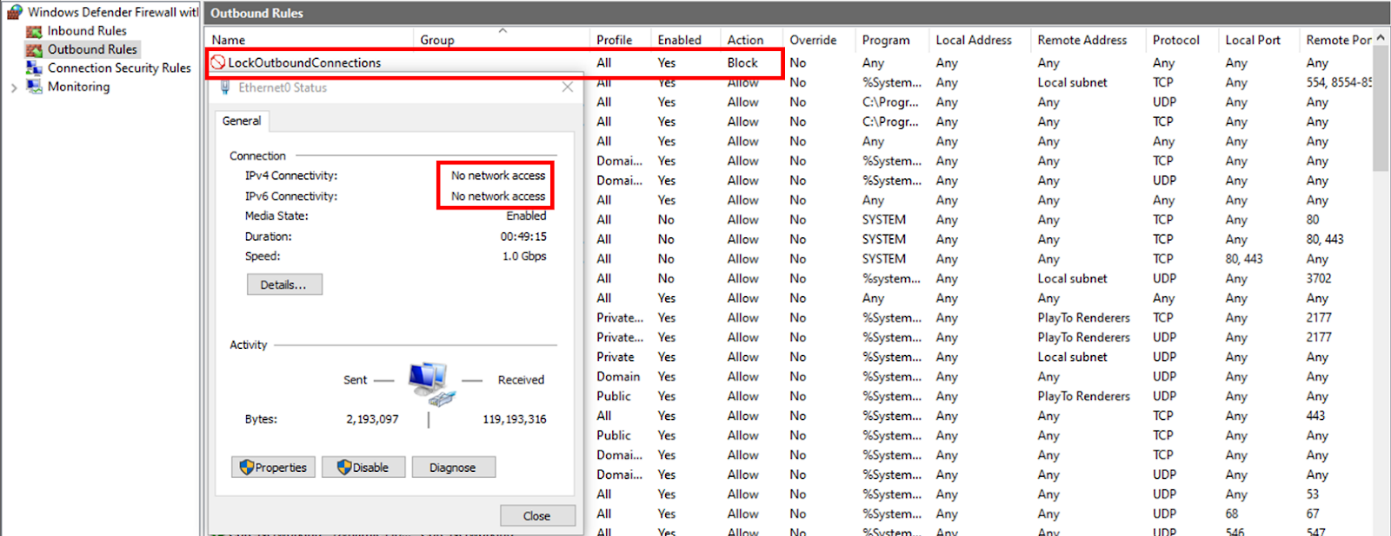
The last step in the attack chain is to create a firewall rule that blocks all outgoing traffic, which applies to all Windows firewall profiles.
The goal is to reduce the likelihood of defenders detecting markers of infection or receiving alerts about a potential compromise of the hacked system.
To evade security tools that monitor the running behavior of processes, the malware waits at least 30 seconds after browser emptiness before creating the firewall rule. It is possible that the miner continues to communicate with his mining pool through a backdoor that is not monitored by security tools.
Morphisec warns that the impact of the malware goes beyond service outages, degraded server performance and overheated computers.
Once attackers gain a foothold in the network, they can do everything from backdoor deployment to code execution.
To address the risk of ProxyShellMiner infections, Morphisec advises all administrators to apply available security updates and employ comprehensive, multi-faceted threat detection and defense strategies.
[ad_2]
Source link
