[ad_1]

A new stealth malware dubbed “Beep” was discovered last week, which has many features to evade scanning and detection by security software.
The malware was discovered by analysts from Minerva after a slew of samples were uploaded to VirusTotal, an online file scanning and malicious content detection platform.
Although Beep is still in development and missing several key features, it currently allows hackers to download and remotely execute other payloads on compromised devices.
A new information thief in the making
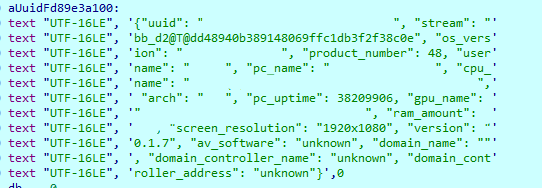
Beep is information-stealing malware that uses three separate components: a dropper, an injector, and the payload.
The dropper (“big.dll”) creates a new registry key with a value “AphroniaHaimavati” which contains a base64 encoded PowerShell script. This PowerShell script is launched every 13 minutes using a Windows Scheduled Task.
When the script is executed, it downloads the data and saves it to an injector named AphroniaHaimavati.dll, which is then launched.
The injector is the component that uses a range of anti-debugging and anti-vm techniques to inject the payload into a legitimate system process (“WWAHost.exe”) via process mining to evade detection from running antivirus tools on the host.
Finally, the main payload attempts to collect data from the compromised machine, encrypt it, and send it to C2. While scanning Minerva, the hard-coded C2 address was offline, but the malware attempted to connect even after 120 failed attempts.
Despite the limitations of the malware analysis, Minerva was still able to identify the following functions in the sample, which are triggered by C2 commands:
- pendulum – not yet implemented
- initialize – not yet implemented
- screenshot – appears to collect process list
- stain – not yet implemented
- destroy – not yet implemented
- shell code – executes additional shellcode
- dll – run a dll file
- exe – run an .exe file
- Additional – collects additional information
- knock_timeout – change C&C “keep-alive” intervals
Avoid detection
What sets the Beep malware apart is its use of multiple techniques throughout its execution flow to evade detection and analysis by security software and researchers.
These evasion techniques are summarized below:
- Dynamic Channel Deobfuscation – Hides important strings and copies hexadecimal bytes into memory. Beep deobfuscates them if necessary using the xor/sub/add/not assembly instructions.
- System language check – Beep will check the default system language and quit if Russian, Ukrainian, Belarusian, Tajik, Slovenian, Georgian, Kazakh and Uzbek (Cyrillic) are detected.
- Assembly implementation of IsDebuggerPresent API function – Checks if a user-mode debugger is debugging the current process.
- Anti-debugging of the NtGlobalFlag field – Determine if a debugger created the process.
- RDTSC instruction – Determine processor ticks since reset to determine if it is running in a virtual machine.
- Stack segment register – Detect if the program is traced.
- CPUID anti-vm – Get the brand string of the hypervisor and check if it contains part of the word “VMware”.
- VBOX anti-vm registry key – Verify the existence of registry keys related to the virtual machine.
- Beep API anti-sandbox function – Alternative to the “sleep API function”, it generates a beep on the speaker while delaying malware execution (alertable wait) to escape sandbox detection.
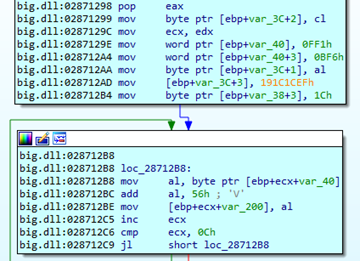
In addition to the above, the injector component also implements the following evasion techniques:
- Anti-debug INT 3 – Throw an exception that will force the debuggers to stop working.
- INT 2D anti-debugging – Throw an exception that will force the debuggers to stop working.
- Anti-debugging API CheckRemoteDebuggerPresent() – Determine if a debugger is attached to the current process.
- IsDebuggerPresent() API anti-debugging – Determine if a user-mode debugger is debugging the current process.
- Anti-debugging ProcessDebugPort – Determine the debugger port number for the process.
- Anti-debugging VirtualAlloc() / GetWriteWatch() – Track pages written to memory to detect debuggers and hooks.
- Anti-debugging OutputDebugString() – Debugger detection technique based on a return result.
- Anti-debugging QueryPerformanceCounter() and GetTickCount64() – Measure the delay between instructions and execution to determine if a debugger is running on the system.
Beep is an example of malware that has a strong focus on evasion, having implemented several anti-analysis mechanisms before finalizing the full feature set for data theft and command execution.
Although its operations in the wild remain limited at this time, Beep could be a threat worth watching.
[ad_2]
Source link
