[ad_1]

Mandiant security researchers have discovered new malware called CosmicEnergy designed to disrupt industrial systems and linked to Russian cybersecurity company Rostelecom-Solar (formerly Solar Security).
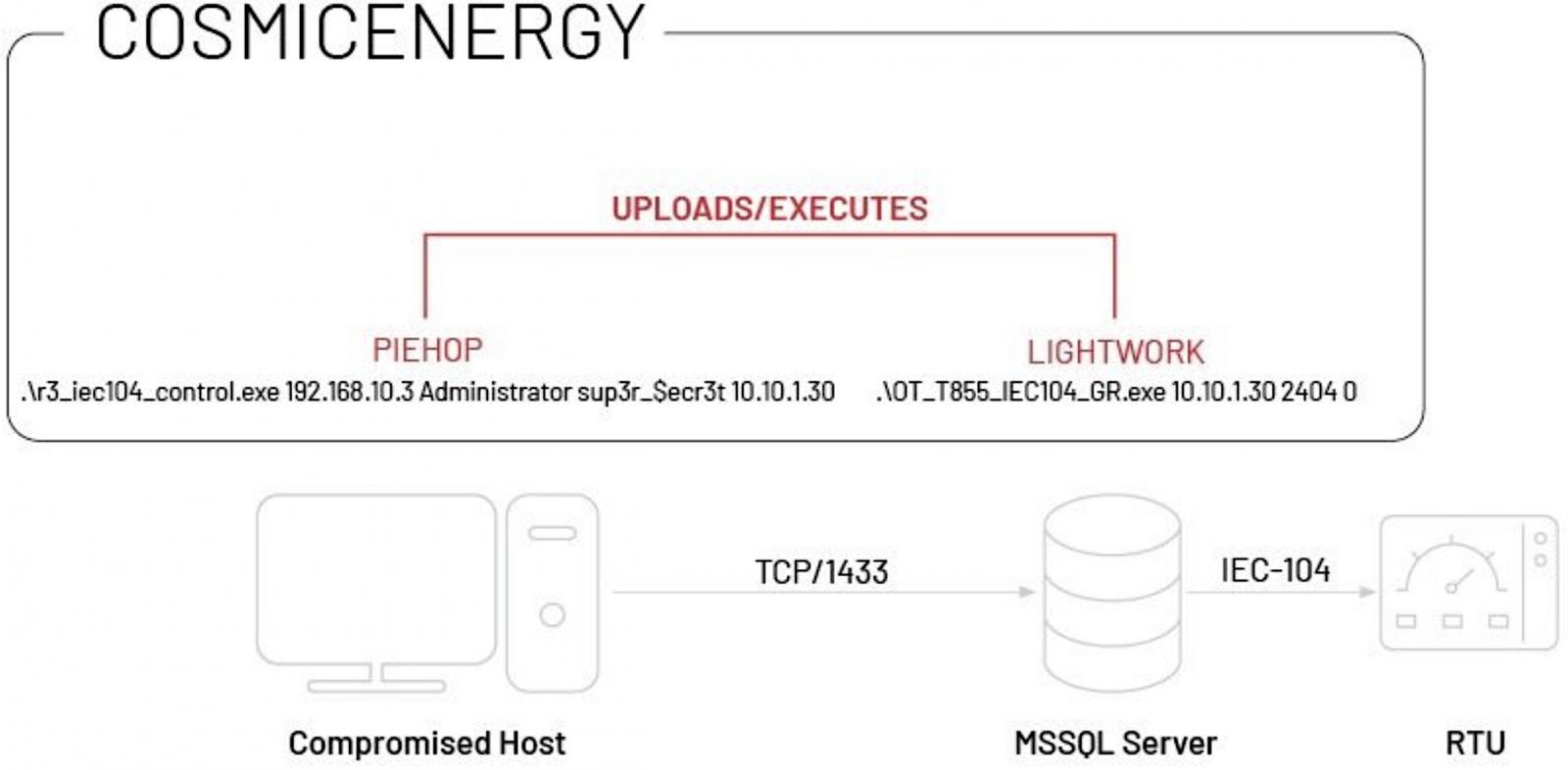
The malware specifically targets IEC-104 compliant remote terminal units (RTUs) commonly used in power transmission and distribution operations in Europe, the Middle East and Asia.
CosmicEnergy was discovered after a sample was uploaded to malware analysis platform VirusTotal in December 2021 by someone with a Russian IP address.
Analysis of the leaked malware sample revealed several noteworthy aspects regarding CosmicEnergy and its features.
First, the malware shares similarities with previous OT malware like Industroyer and Industroyer.V2, both of which were used in attacks targeting Ukrainian energy providers in December 2016 And April 2022.
Moreover, it is Python-based and uses open-source libraries for OT protocol implementation, just like other malware strains targeting industrial control systems including iron gate, TritonAnd uncontrollable.
Like Industroyer, CosmicEnergy likely accesses the target’s OT systems through compromised MSSQL servers using the Piehop disruption tool.
Once inside the victims’ network, attackers can control RTUs remotely by issuing IEC-104 “ON” or “OFF” commands via the Lightwork malicious tool.
Mandiant believes this newly discovered malware may have been developed as a red team tool designed to simulate disruption drills by Russian cybersecurity firm Rostelecom-Solar.
Based on public information showing that Rostelecom-Solar received funding from the Russian government for cybersecurity training and simulating power outages, Mandiant suspects that CosmicEnergy could also be used by Russian threat actors in disruptive cyberattacks targeting critical infrastructure as other team tools red.
“During our analysis of COSMICENERGY, we identified a comment in the code indicating that the sample uses a module associated with a project named ‘Solar Polygon’. We searched for the unique string and identified a single match to a cyber range (aka polygon) developed by Rostelecom-Solar”, Mandiant said.
“Although we have not identified sufficient evidence to determine the origin or purpose of COSMICENERGY, we believe that the malware may have been developed by Rostelecom-Solar or an associated party to recreate attack scenarios assets against energy grid assets,” Mandiant said. said.
“Given that threat actors use red team tools and public exploit frameworks for targeted threat activity in the wild, we believe that COSMICENERGY poses a plausible threat to affected power grid assets.”
As Microsoft reported in April 2022, after Russia invaded Ukraine, Russian hacking groups deployed numerous malware families (some of them never seen before) in destructive attacks against Ukrainian targets, including critical infrastructure.
The list includes but is not limited to WhisperGate/WhisperKill, FoxBlade (a.k.a Hermetic), SonicVote (aka HermeticRansom), CaddyWindscreen wiperDesertBlade, Industry2Lasainraw (aka IsaacWiper), and FiberLake (aka DoubleZero).
Sandworm Russian Military Hackers used Industroyer2 malware to target the ICS network of a major Ukrainian energy supplier, but failed to shut down its high-voltage electrical substations and disrupt energy delivery across the country.
[ad_2]
Source link
