[ad_1]

Attackers are now using encrypted RPMSG attachments sent through compromised Microsoft 365 accounts to steal Microsoft credentials in targeted phishing attacks designed to evade detection by email security gateways.
RPMSG files (also known as Restricted Permission Message files) are encrypted attachments created using Microsoft Rights Management Services (RMS) and provide an additional layer of protection to sensitive information by restricting access to authorized recipients.
Recipients who wish to read them must authenticate using their Microsoft account or obtain a one-time password to decrypt the content.
Like Trustwave recently discoveredRPMSG’s authentication requirements are now being exploited to trick targets into handing over their Microsoft credentials using fake login forms.
“It starts with an email from a compromised Microsoft 365 account, in this case from Talus Pay, a payment processing company,” trustwave said.
“The recipients were users of the recipient company’s billing department. The message displays a Microsoft encrypted message.”
The threat actors’ emails ask targets to click a “Read message” button to decrypt and open the protected message, redirecting them to an Office 365 webpage with a request to sign in to their Microsoft account.
After authenticating using this legitimate Microsoft service, recipients can finally see the attackers’ phishing email that will send them to a fake SharePoint document hosted on Adobe’s InDesign service after clicking a “Click here to continue”.
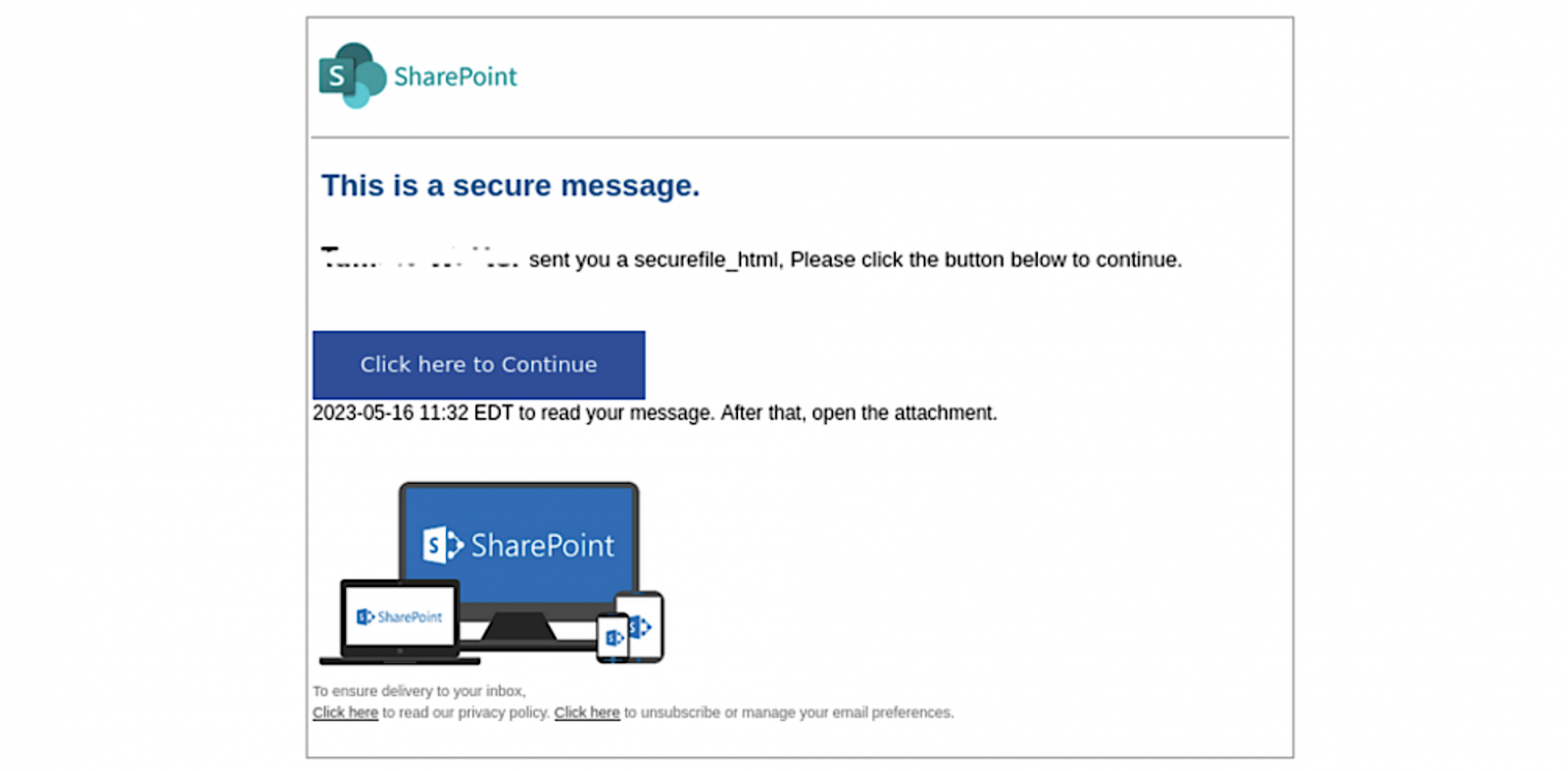
From there, clicking “Click here to view document” leads to the final destination which displays an empty page and a “Loading…Waiting” message in the title bar which acts as a decoy to allow a script malicious to collect various system information.
Data collected includes visitor ID, login token and hash, video card rendering information, system language, device memory, hardware concurrency, installed browser plug-ins , browser window details and operating system architecture.
Once the script is done collecting data from the targets, the page will display a cloned Microsoft 365 login form which will send the entered usernames and passwords to servers controlled by the attacker.
Detecting and countering these phishing attacks can be quite difficult due to their low volume and targeted nature, as observed by Trustwave researchers.
Additionally, attackers’ use of trusted cloud services such as Microsoft and Adobe to send phishing emails and host content adds an additional layer of complexity and reliability.
Encrypted RPMSG attachments also conceal phishing messages from email scanning gateways, since the only hyperlink in the initial phishing email directs potential victims to a legitimate Microsoft service.
“Educate your users about the nature of the threat, and don’t attempt to decrypt or unlock unexpected messages from outside sources,” Trustwave advises companies looking to mitigate the risks posed by this type of phishing attack.
“To prevent Microsoft 365 accounts from being compromised, enable multi-factor authentication (MFA).”
[ad_2]
Source link
