[ad_1]

New details have emerged of Decoy Dog, a largely undetected sophisticated toolkit likely used for at least a year in cyber intelligence operations, relying on the Domain Name System (DNS) for command and control activity.
It’s unclear who’s behind the malware, but researchers from DNS-focused security vendor Infoblox believe four players are using and developing it for highly targeted operations.
The observed activity is limited to Russian space and Eastern Europe and appears to be related to Russia’s invasion of Ukraine.
The Decoy Dog activity continues
While Infoblox only scanned DecoyDog’s DNS and network traffic, since it’s based on Pupy, it likely has the ability to download malware payloads onto infected devices and execute commands sent by attackers.
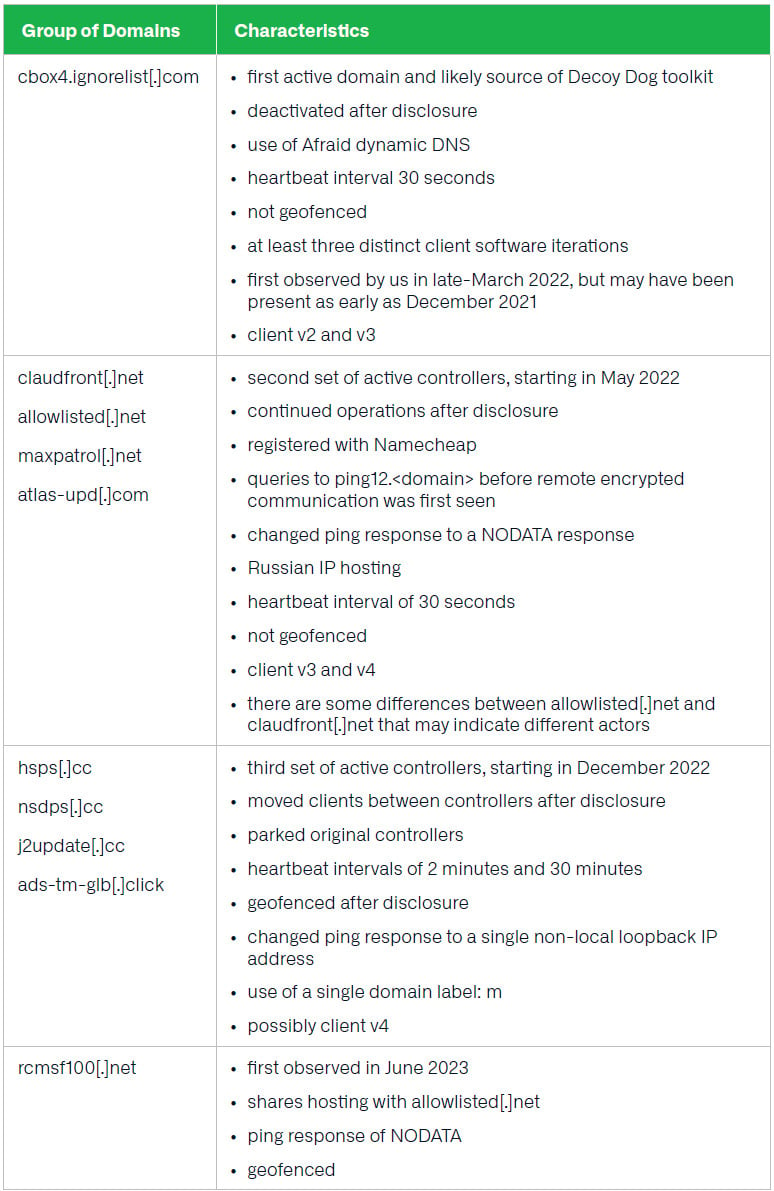
Decoy Dog was discovered in early April after Infoblox specialists discovered abnormal DNS tagging activity half a dozen domains that acted as command-and-control (C2) servers for the malware:
- cbox4[.]ignore list[.]com
- claudfront[.]net
- hsdps[.]CC
- ads-tm-glb[.]Click on
- atlas-upd[.]com
- whitelisted[.]net
At the time, the researchers said they “found identical DNS query patterns from corporate networks, which could not be linked to consumer devices” and “confirmed that the queries originated from network devices in a very limited number of customer networks.”
Whoever exploits the toolkit did not go out of business after Infoblox announced its discovery and published a technical analysis showing that Decoy Dog was heavily based on the open source post-exploitation remote access Trojan Pupy (RAT).
New Infoblox Search published today reveals that “Decoy Dog is a major Pupy update that uses commands and configurations that are not in the public repository”.
Among the differences observed are:
- Decoy Dog uses Python 3.8 while Pupy was written in Python 2.7. Decoy Dog requires Python 3.8
- many improvements including Windows compatibility and better memory operations
- Decoy Dog greatly expands the communication vocabulary in Pupy by adding several communication modules
- Decoy Dog responds to replays of previous DNS queries where Pupy does not.
- unlike Pupy, Decoy Dog responds to generic DNS queries, which doubles the number of resolutions seen in passive DNS.
- Decoy Dog responds to DNS queries that do not match the structure of valid communication with a client.
- Decoy Dog adds the ability to execute arbitrary Java code by injecting it into a JVM thread and adds methods to maintain persistence on a victim device.
Infoblox initially singled out three Decoy Dog operators, which reacted differently after the company disclosed in April. A fourth was discovered after researchers completed the current Infoblox report.
cbox4 activity[.]ignore list[.]com has stopped, while hsdps[.]cc and ads-tmglb[.]click customers transferred to new domains.
However Infoblox did not see any operational change with claudfront[.]net and whitelisted[.]net. The former significantly increased its business in February this year by transferring clients to newly registered controllers.
Renée Burton, threat intelligence manager at Infoblox, told BleepingComputer that hsdps operators[.]cc and ads-tm-glb[.]click domains were able to “hot swap” clients to another controller, meaning the change was made in memory.
The current number of Decoy Dog nameservers, controllers, and domains is now closer to two dozen, Burton told us. A list of several domains used by the toolkit is available below.
source: Infoblox
Highly targeted malware with a short list of victims
Based on analysis of passive DNS traffic, it is difficult to determine an accurate number of Data Dog clients, which would indicate affected devices, but the highest number of active concurrent connections Infoblox observed on a controller was less than 50 and the lowest was four.
Burton estimates the current number of compromised devices to be less than a few hundred, indicating a very small set of targets, typical of an intelligence operation.
Some of the changes made by a Decoy Dog operator after the Infoblox disclosure was to add a geofencing mechanism that restricts controller domain responses to DNS queries from IP addresses in specific regions.
“We discovered this behavior in June 2023 and found that some of the servers only responded when we routed DNS queries through Russian IP addresses, while others responded to any well-formed query from any location” – Infoblox
While this may imply that the victims are in Russia, the actor could also have chosen to route the trafficking of victims through the region as a decoy or limit the queries to relevant queries.
Burton leans towards the first guess, explaining that Decoy Dog behaves like Pupy and uses the default recursive resolver to connect to DNS. Because changing this system in modern networks is “quite difficult”, says the researcher, it is likely that “these controllers have victims in Russia or adjacent countries (which could also route data through Russia)”.
TTPs point to multiple actors
Infoblox distinguishes the four actors operating Decoy Dog based on the tactics, techniques, and procedures (TTPs) observed. However, it seems they all respond to queries that match the correct format for Decoy Dog or Pupy.
Burton noted that this is bizarre behavior that could be intentional, but even with her vast background as a cryptographer, intelligence person, and data scientist, she can’t attribute it to a specific reason.
If the theory of multiple players handling Decoy Dog is true, there may be two development groups that enhanced the toolkit with new features.
According to Burton, one of the four groups has the the most advanced Decoy Dog version seen in public repositories, whose clients connect to the claudfront controller[.]net.
One controller in this group, Burton told BleepingComputer, is maxpatrol.[.]net but no connection was seen for it. This may suggest a lookalike of the vulnerability and compliance management system of Positive Technologies, a Russian cybersecurity company that has been sanctioned by the United States in 2021 for trafficking in hacking tools and exploits used by state-sponsored hacking groups.
Infoblox notes that new versions of the toolkit come with a Domain Generation Algorithm (DGA) that acts as a fallback module to allow compromised machines to use a third-party DNS server if the malware cannot communicate with its C2 server for an extended period.
Many persistence mechanisms are available from version 3 of the Decoy Dog client, indicating an intelligence operation rather than a financial operation or a red team.
Decoy Dog’s litter remains a mystery
For now, the Decoy Dog operations remain a mystery in regards to their purpose and their masters. Infoblox did its part by discovering the toolkit using DNS data from its systems and bringing it to the attention of the infosec community.
However, further research is needed to determine the targets, initial method of compromise (e.g., supply chain, known vulnerability, day zero in targeted devices), and how actors move through the network.
Although Infoblox has received support from the infosec community (major intelligence providers, government agencies, threat research groups, and financial organizations), detections of the malware or its full scope have not been publicly disclosed.
Infoblox recommends that defenders consider the IP addresses in Decoy Dog and Pupy to represent encrypted data, not real addresses used for communication.
They should also focus on DNS queries and responses, as they can help track malware activity. A caveat is that the volume of communication is low and a large log history is needed to track communication.
The company has also created a YARA rule that can detect Decoy Dog samples observed by researchers since July and distinguish the toolkit from the public version of Pupy.
[ad_2]
Source link
