[ad_1]

New Mac malware dubbed “Realst” is being used in a massive campaign targeting Apple computers, with some of its latest variants including support for macOS 14 Sonoma, which is still in development.
The malware, first discovered by a security researcher iamdeadlyzis distributed to Windows and macOS users in the form of fake blockchain games using names such as Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend.
These games are promoted on social media, with threat actors using direct messages to share access codes needed to download the fake game client from associated websites.
Passcodes allow threat actors to control who they want to target and avoid security researchers who want to reveal malicious behavior.
In reality, game installers infect devices with information-stealing malware, such as RedLine Stealer on Windows and Realst on macOS. This malware will steal data from victim’s web browsers and cryptocurrency wallet apps and send it back to threat actors.
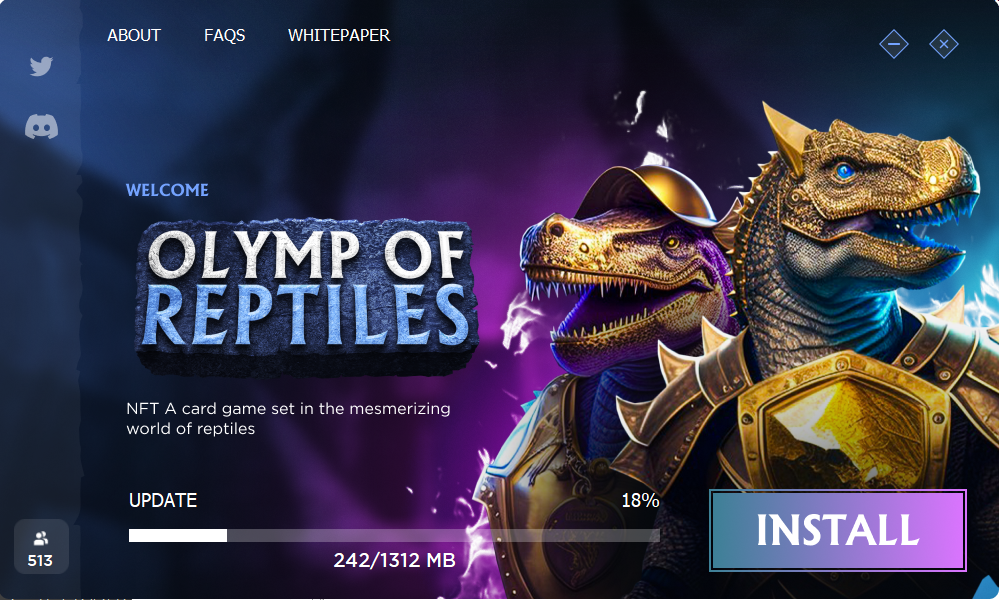
Source: iamdeadlyz.gitbook.io
SentinelOne analyzed 59 Mach-O samples of the Realst malware found by iamdeadlyz, focusing on its macOS versions, and found several distinct differences.
This allowed researchers to identify 16 variants of the macOS malware, a sign of active and rapid development.
Realst Mac Malware
When downloading the fake game from the threat author’s site, they will be offered Windows or macOS malware, depending on their operating system.
Windows malware is usually RedLine Stealer, but sometimes other malware like Raccoon Stealer and AsyncRAT.
For Mac users, the sites will distribute Realst information-stealing malware, which targets Mac devices as PKG installers or DMG disk files containing the malicious Mach-O files, but not real games or other decoy software.
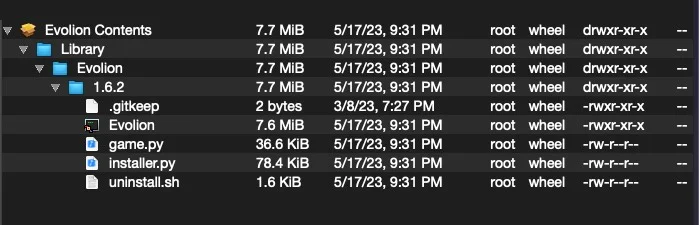
The “game.py” file is a cross-platform Firefox infostealer and “installer.py” is “chainbreaker”, an open source macOS keychain database password, key and certificate extractor.
SentinelOne has discovered that some samples are encoded using valid (now revoked) Apple Developer IDs, or ad-hoc signatures, to circumvent detection by security tools.
Variants
The 16 distinct Realst variants analyzed by SentinelOne are quite similar in form and function, although they use different sets of API calls.
In all cases, the malware targets Firefox, Chrome, Opera, Brave, Vivaldi and the Telegram app, but none of the analyzed Realst samples targets Safari.
“Most variants attempt to grab the user’s password via osascript and AppleScript spoofing and perform rudimentary verification that the host device is not a virtual machine via sysctl -n hw.model,” SentinelOne explains. in the report.
“The collected data is deposited in a folder simply named “data” [which] may appear in several places depending on the malware version: in the user’s home folder, in the malware’s working directory, or in a folder named after the parent game.”
The 16 distinct variants are categorized into four main families based on their traits, namely A, B, C, and D.
Family A, which has the most samples in circulation, uses “AppleScript spoofing” to trick the victim into entering their administrator password in a dialog box.
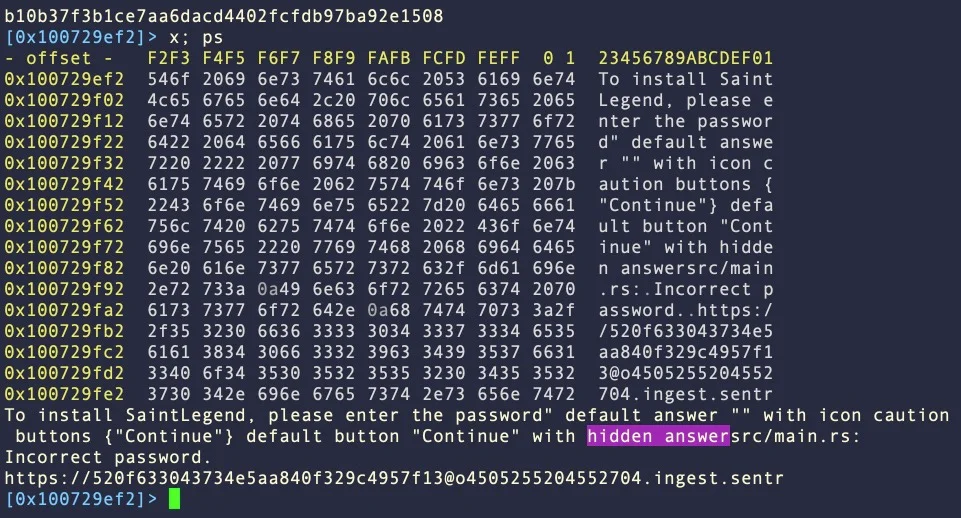
Family B is similar to A and also uses password spoofing, but breaks relevant strings into smaller units to avoid simple static detection.
The C family also has a reference to chainbreaker in the binary itself, which allows it to pull data from the system’s keychain database.
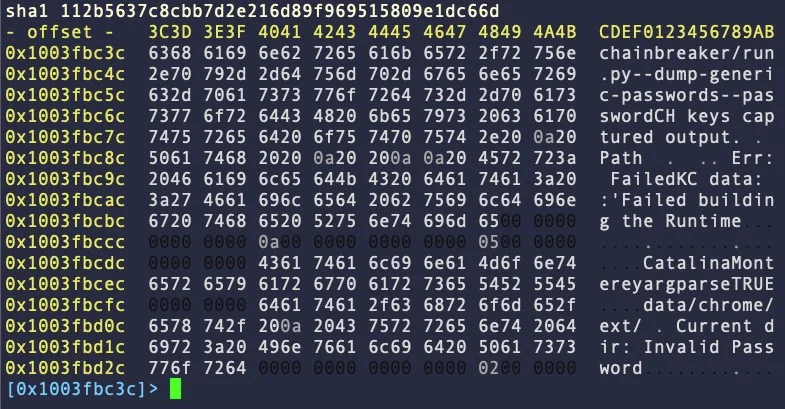
Finally, Family D uses the terminal window to prompt the victim to enter their password, which is used to dump saved credentials stored in the keychain.
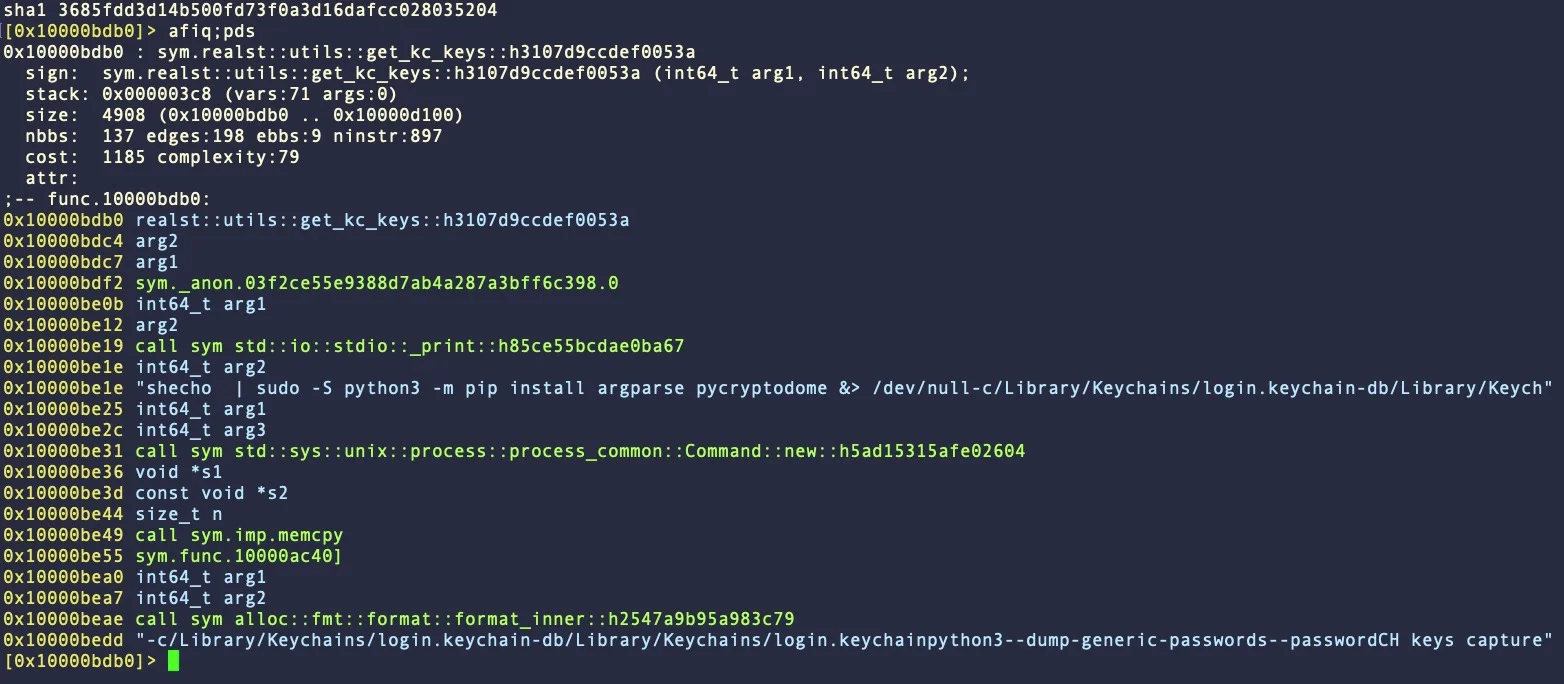
In some cases, the D-family exploits the acquired password to gain administrator privileges on the system and install the “pycryptodome” Python cryptography library, which is also used to dump keychain credentials.
About 30% of samples from families A, B, and D contain strings that target the upcoming macOS 14 Sonoma.
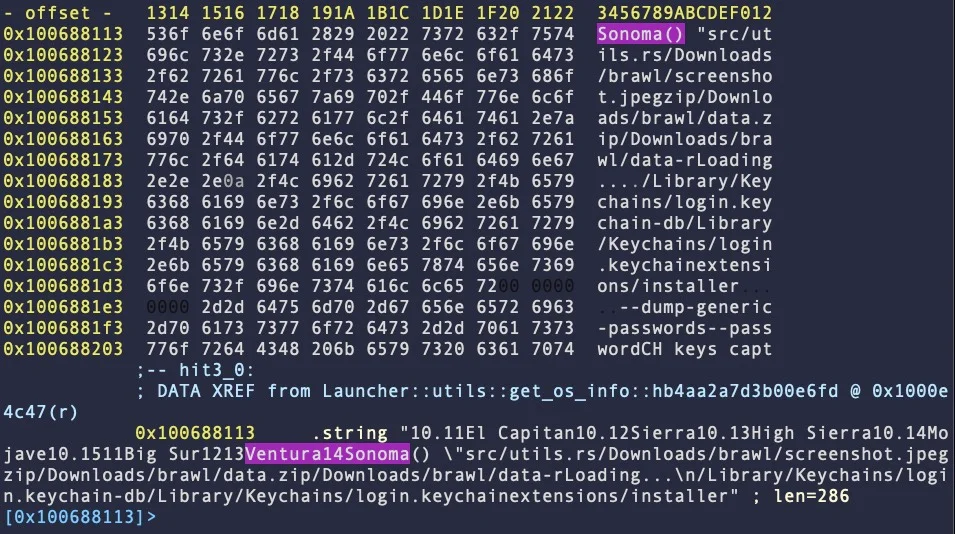
The presence of these strings shows that malware writers are already preparing for the next version of Apple’s desktop operating system, guaranteeing that Realst will be compatible and work as expected.
MacOS users are advised to be careful with blockchain games, as those who distribute Realst use Discord channels and “verified” Twitter accounts to create a false image of legitimacy.
Additionally, since these games specifically target cryptocurrency users, the main goal is likely to steal crypto wallets and the funds they contain, leading to costly attacks.
[ad_2]
Source link
