[ad_1]

Administrators, hosters and the French computer emergency response team (CERT-FR) warn that attackers are actively targeting unpatched VMware ESXi servers against a two-year-old remote code execution vulnerability to deploy ransomware.
Tracked as CVE-2021-21974The security flaw is caused by a heap overflow issue in the OpenSLP service that can be exploited by unauthenticated malicious actors in low complexity attacks.
“In view of the ongoing investigations, these attack campaigns seem to exploit the CVE-2021-21974 vulnerability, for which a patch has been available since February 23, 2021”, specifies the CERT-FR.
“The systems currently targeted would be ESXi hypervisors in version 6.x and earlier than 6.7.”
To block inbound attacks, administrators should disable the vulnerable Service Location Protocol (SLP) service on ESXi hypervisors that have not yet been updated.
CERT-FR strongly recommends applying the patch as soon as possible, but adds that unpatched systems should also be scanned for signs of compromise.
CVE-2021-21974 affects the following systems:
- ESXi 7.x versions earlier than ESXi70U1c-17325551
- ESXi 6.7.x versions earlier than ESXi670-202102401-SG
- ESXi 6.5.x versions earlier than ESXi650-202102101-SG
French cloud provider OVHcloud also released a report today linking this massive wave of attacks targeting VMware ESXi servers to the Nevada ransomware operation.
“According to ecosystem experts as well as authorities, they may be linked to Nevada ransomware and are using CVE-2021-21974 as a compromise vector. Investigations are still ongoing to confirm these assumptions,” said Julien Levrard, CISO from OVHcloud. said.
“The attack primarily targets ESXi servers in a version prior to 7.0 U3i, apparently via the OpenSLP port (427).”
At least 120 VMware ESXi servers worldwide have already been compromised in this ransomware campaign, according to a Shodan Research.
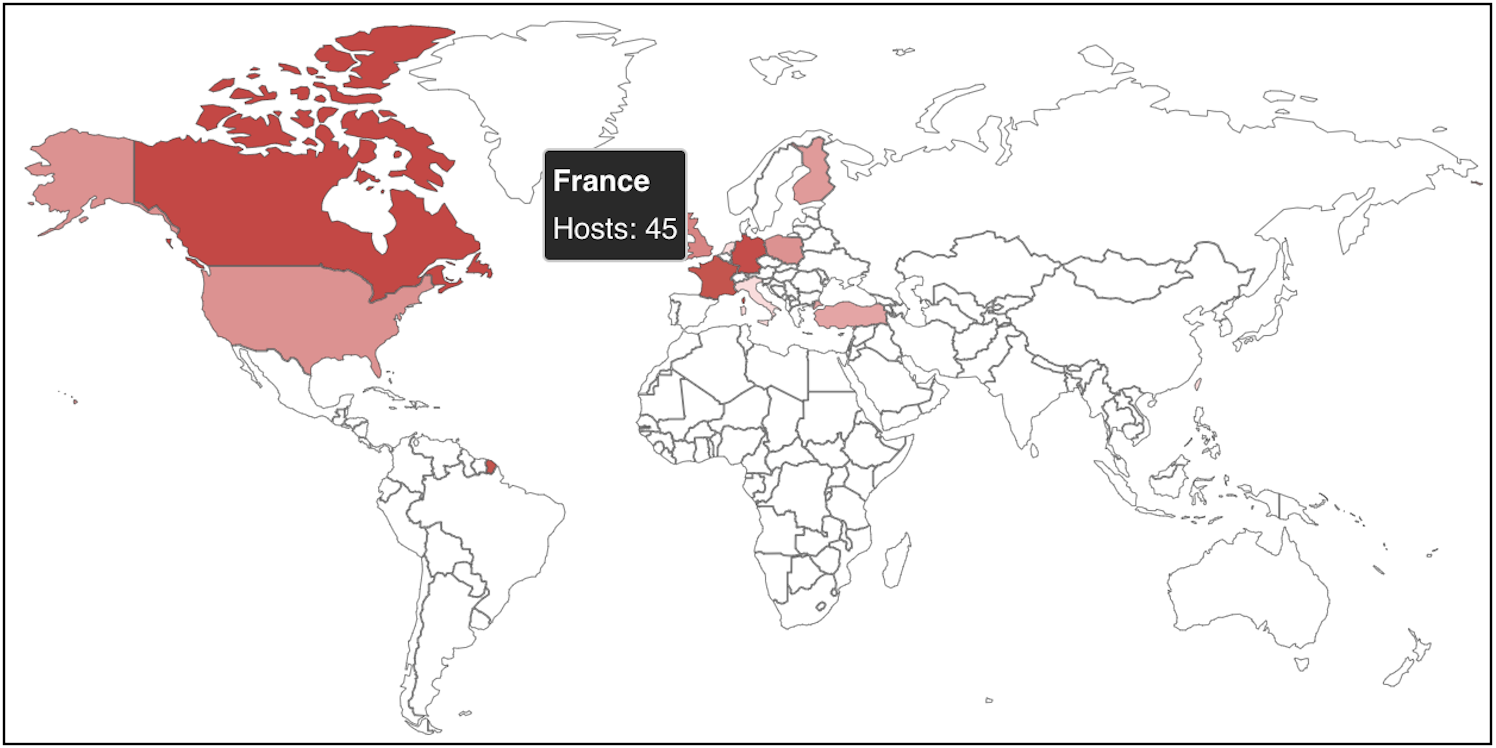
New ESXiArgs ransomware
However, from the ransom notes seen in this attack, they do not appear to be related to Nevada Ransomware and appear to be a new ransomware family.
For about four hours, the victims affected by this campaign have also started to report the attacks on BleepingComputer Forumasking for help and more information on how to recover their data.
The ransomware encrypts files with .vmxf, .vmx, .vmsd and .nvram extensions on compromised ESXi servers and creates a .args file for each encrypted document with metadata (probably needed for decryption).
Victims found ransom notes named “ransom.html” and “How to restore your files.html” on locked systems. Others said their notes were plaintext files.
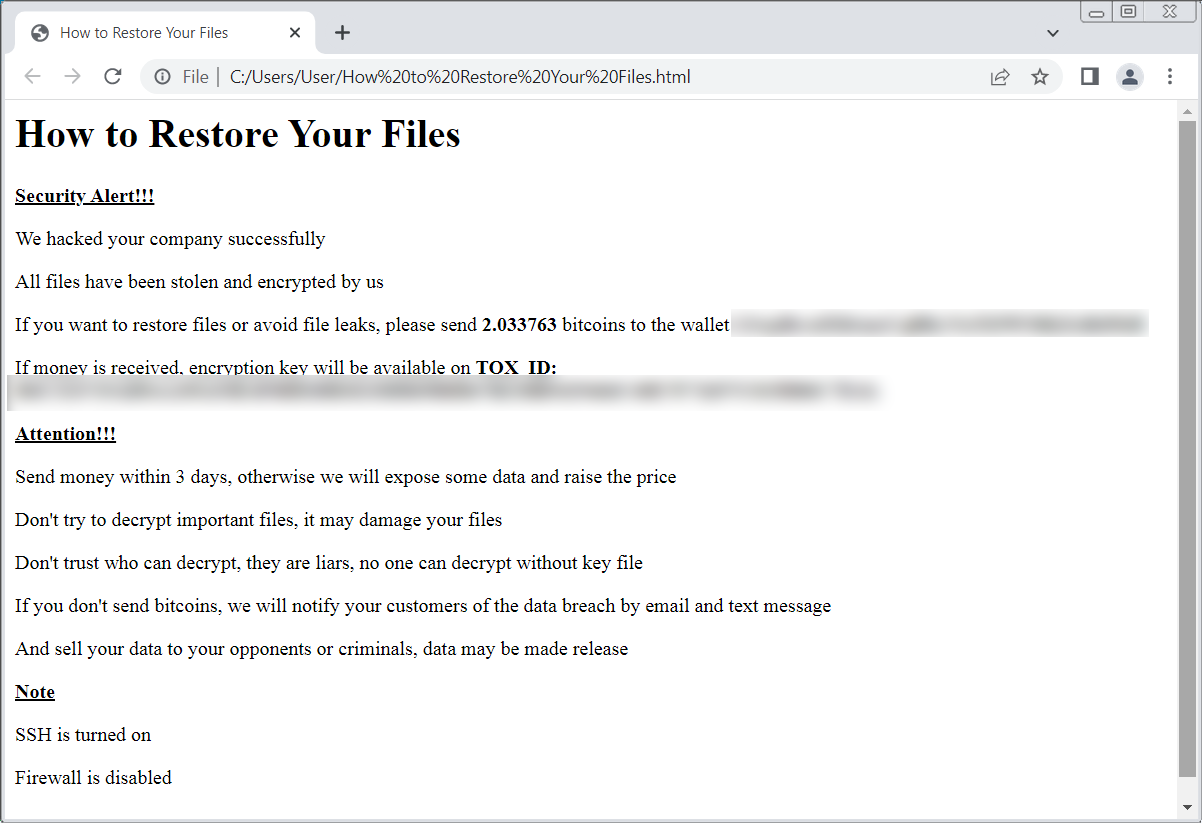
Identification ransomwareit is Michael Gillespie is currently tracking the ransomware as ‘ESXiArgs‘, but told BleepingComputer that until we can find a sample, there’s no way to determine if it has any weaknesses in the encryption.
BleepingComputer has a dedicated support topic where people report their experiences with this attack.
If you have any new information or a copy of the malware, please let us know so researchers can analyze it for weaknesses.
This is a developing story and will be updated with new information as it becomes available…
[ad_2]
Source link