[ad_1]

The developers of the GoAnywhere MFT file transfer solution are warning customers of a zero-day remote code execution vulnerability on exposed administrative consoles.
GoAnywhere is a secure web-based file transfer solution that allows businesses to securely transfer encrypted files with their partners while maintaining detailed audit logs of who accessed the files.
The GoAnywhere security advisory was first made public by a journalist Brian Krebswho posted a copy on Mastodon.
A customer who received the notification told BleepingComputer that it affects both on-premises and SaaS implementations of GoAnywhere, but we could not independently confirm this at this time.
According to the security advisory, the exploit requires access to the administration console, which normally should not be exposed to the internet.
“A Zero-Day Remote Code Injection exploit has been identified in GoAnywhere MFT,” warns the GoAnywhere security advisory.
“The attack vector for this exploit requires access to the application’s admin console, which in most cases can only be accessed from within a private corporate network, via VPN or by authorized IP addresses (when running in cloud environments, such as Azure or AWS).”
As there is no patch currently available for the zero-day vulnerability, Fortra urges administrators to apply the following mitigation:
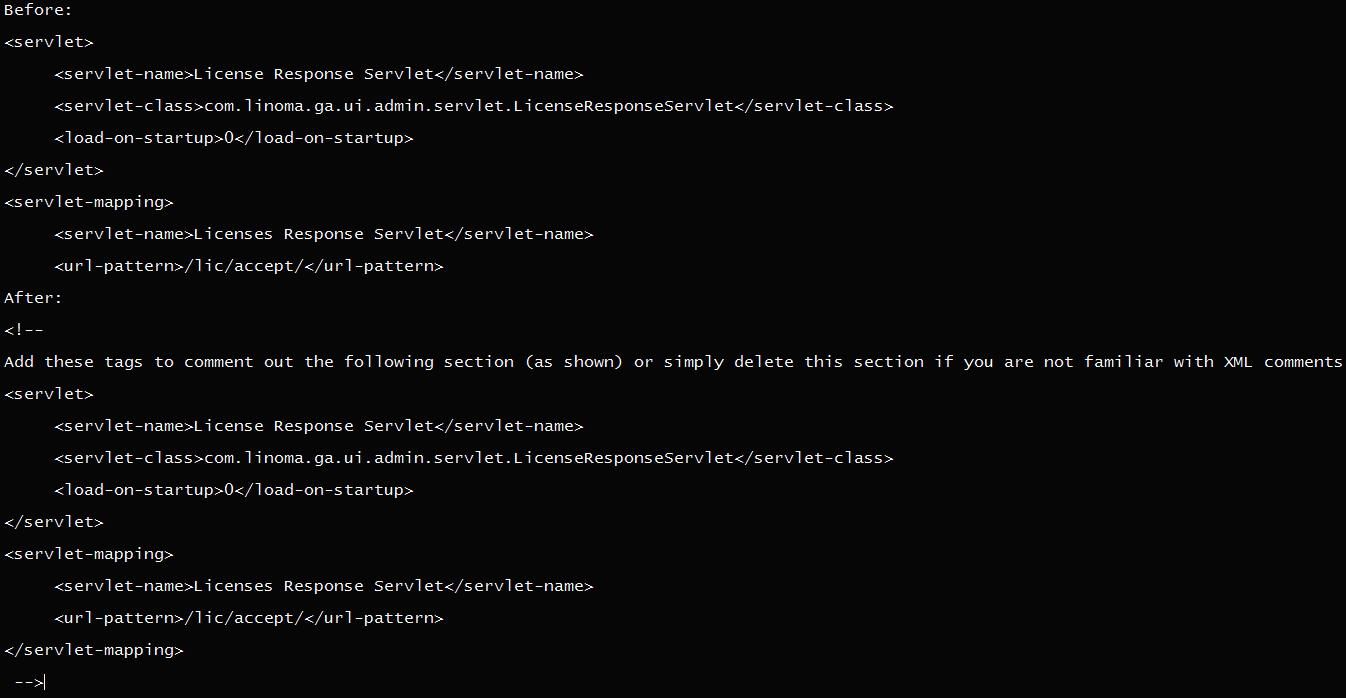
- On the file system where GoAnywhere MFT is installed, edit the “[install_dir]/adminroot/WEB_INF/web.xml.”
- Find and remove (remove or comment out) the following servlet and servlet mapping configuration in the screenshot below.
- Restart the GoAnywhere MFT application.
At this time, there is no other way to mitigate the attacks, as Fortra has not yet released a security update.
Fortra has also temporarily shut down its SaaS solution while they fix the bug.
The company also recommends that administrators perform an audit of their facilities, including:
- Check if any new unknown administrator accounts have been created by the “system” and if the “administrator audit log shows that a non-existent or disabled super user is creating this account”.
- Look for activity in the admin log (Reports -> Audit Logs -> Admin). Look for anything created by the root user.
security professional Kevin Beaumont performed a Shodan analysis to determine how many GoAnywhere instances are exposed on the internet and found 1,008 servers, mostly in the United States.
However, Beaumont said most admin consoles use ports 8000 and 8001, of which BleepingComputer only saw 151 exposed.
Although the attack surface may seem limited, it is important to note that large organizations use these products to transfer sensitive files with their partners.
BleepingComputer has identified local governments, healthcare companies, banks, energy companies, financial services companies, museums and computer parts manufacturers using the GoAnywhere file transfer solution.
Therefore, even a single breach exploiting GoAnywhere MFT’s zero-day flaw could leak sensitive information that could be used for extortion.
This exact scenario was seen in the Accellion FTA Hacks 2021 (File Transfer Appliance) by the Clop ransomware gang, which has impacted many prominent companies around the world.
BleepingComputer has contacted Fortra to request more details on active exploit exploitation, and we will update this post as soon as we receive a response.
[ad_2]
Source link
