[ad_1]

Threat actors spend a lot of their time on surveillance. Typical services generate numerous audit logs which can be difficult to analyze and locate potentially malicious events.
Since much of the monitoring is automated, creating a specific machine open to the internet, waiting for probes and attacks, is incredibly useful and is known as a honeypot.
The wealth of data collected by a honeypot enables analysis of known and unknown attacks, meaning an organization can proactively track and block threats.
Relying strictly on threat disclosures means you’re reactive, but with a honeypot you can identify a potential attack and block it before it becomes a problem!
Monitoring threats with honeypots
With visibility into active attacks, it can be easier to understand the scope of the threat. For example, over several weeks in October 2022, Specops collected 4.6 million password attempts on their honeypot system.
In any given year, that’s in addition to the millions of potential passwords an attacker can use to break into your organization.
So how do honeypots work? A honeypot is nothing more than a system to trick threat actors into attempting an exploit. Once connected, the honeypot logs the malicious attempt for later analysis.
An example of a basic honeypot is a Microsoft server virtual machine (VM) with an open Remote Desktop Protocol (RDP) connection to the internet. With logging, you can see all of an attacker’s attempts for usernames.
Taking this to the next level, many different types of software cover a wide range of potential pathways in a system. For example, pyrdp offers a man-in-the-middle approach. This allows you to monitor a threat actor attempting an attack in real time, while controlling the attack.
Walking through discoveries
What do recent reports on the status of attacks show?
Blumira analyzed the data from their honeypot from 2019 to 2020 against their Google Cloud Platform (RDP) virtual machine and found that over 179,000 unique usernames were attempted in at least 122 countries.
Additionally, from 2019 to 2020, the incidence of attacks increased by 85%, reflecting the increasingly sophisticated and automated monitoring that threat actors use to collect the data needed for ransomware and infrastructure attacks.
Another example of how a basic Windows virtual machine, with RDP open to the internet, can be quickly attacked is the analysis of attacks by TrustedSec.
They found an unprotected Windows 7 virtual machine online for just 9 days and logged over 2,800 access attempts. Of these, 46 passed. Many simply tested if the access worked, but many actively installed ransomware within minutes of logging in!
How to Mitigate Malicious Remote Access Attempts
Although the examples given here focus on RDP connections, a honeypot is not limited to this type of connection, and any remote access system is subject to attacks, such as SSH.
What should an organization do to minimize potential harm?
Three potential solutions will go a long way in protecting against many attacks.
- Implement strong password policies with checks against a list of breached passwords.
- Protect any account with Multi-Factor Authentication (MFA), ensuring that even stolen passwords cannot be used.
- Restrict remote connection access behind a VPN or Zero Trust connection.
Strong password policies
If an attacker gains access to a password dialog, which most persistent attackers can do despite all other protections, having a strong password policy is essential. Sufficiently long and complex passwords ensure that they will not be easily cracked if their hashes are stolen.
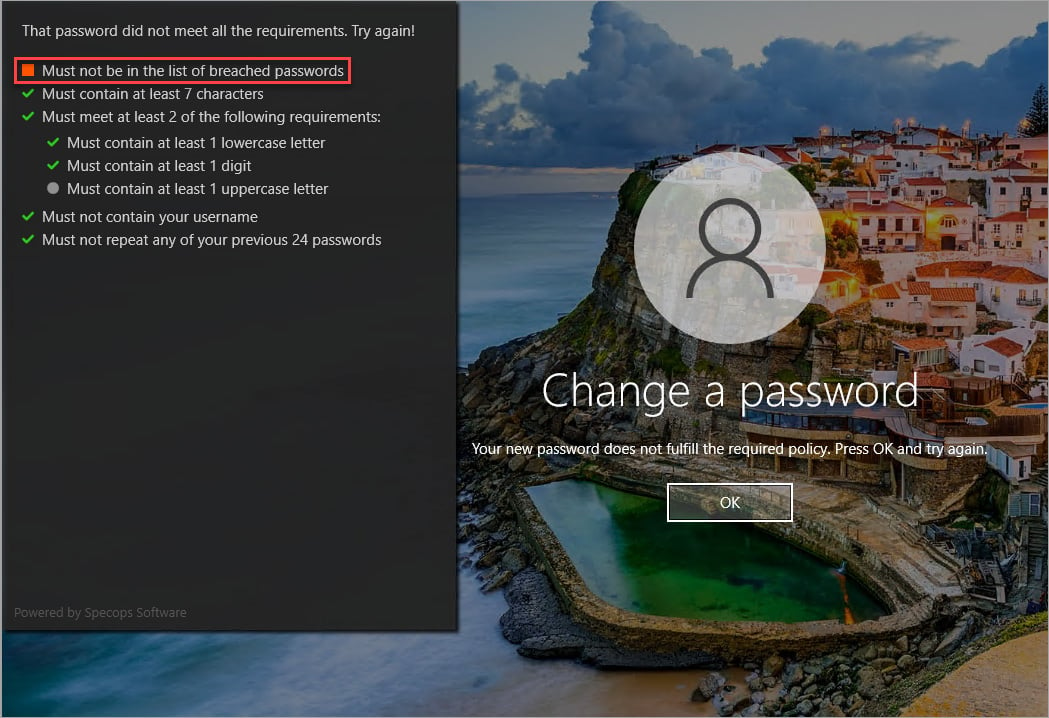
Even before the password is created, a breached password list that checks the new password against known stolen credentials ensures that the most common variations are not used. Unique and complex passwords make an attacker’s job much more complicated.
Specops password policy with Breached Password Protection verifies your users’ passwords and prevents them from choosing a compromised password.
Many threat actors rely on pre-created lists of cracked passwords shared between services, but with password protection verification in case of a breach, the likelihood of this use drops dramatically!
Source: ATALearning
Protect accounts with MFA
Above a strong password policy is the use of MFA. With a second authentication requirement, even a correctly guessed or stolen password does not guarantee access. This indicates that an attempt was made when it was not intended, allowing a user to alert IT and take appropriate action.
Remote Access Limitation
Finally, removing the connection from the public Internet makes it difficult for an attacker to even attempt to gain access to the system. Typically, the connection is placed behind a VPN. Yet, due to the complexity of the configuration, newer systems use the concept of zero trust which verifies that every connection is authenticated and protected.
Protect your organization by learning from honeypots
Learning from the many active threats discovered through honeypots enables an organization to take proactive steps to stay one step ahead of attackers. Locking down outside connections through VPNs or zero-trust services isn’t foolproof for the most persistent threat actors.
Combined with MFA, a strong password policy ensures that threat actors will be blocked even when an attacker sneaks in. Apply strong passwords with a solution such as Specops Password Policy and be proactive in the security of your organization!
Sponsored and written by Specops software
[ad_2]
Source link
