[ad_1]

An alleged Iranian state-backed threat actor known as “Agrius” is currently deploying a new strain of ransomware named “Moneybird” against Israeli organizations.
Agrius has been actively targeting entities in Israel and the Middle East region since at least 2021 under multiple aliases while deployment of data erasers in destructive attacks.
Check Point researchers who discovered the new strain of ransomware believe that Agrios developed it to help expand their operations, while the use of “Moneybird” is yet another of the threat group’s attempts to cover their tracks.
Moneybird Attacks
Check Point researchers say threat actors initially gain access to corporate networks by exploiting vulnerabilities in public servers, giving Agrius an initial foothold within the organization’s network.
Next, hackers hide behind Israel-based ProtonVPN nodes to deploy variant ASPXSpy webshells hidden in “Certificate” text files, a tactic Agrius has used in previous campaigns.
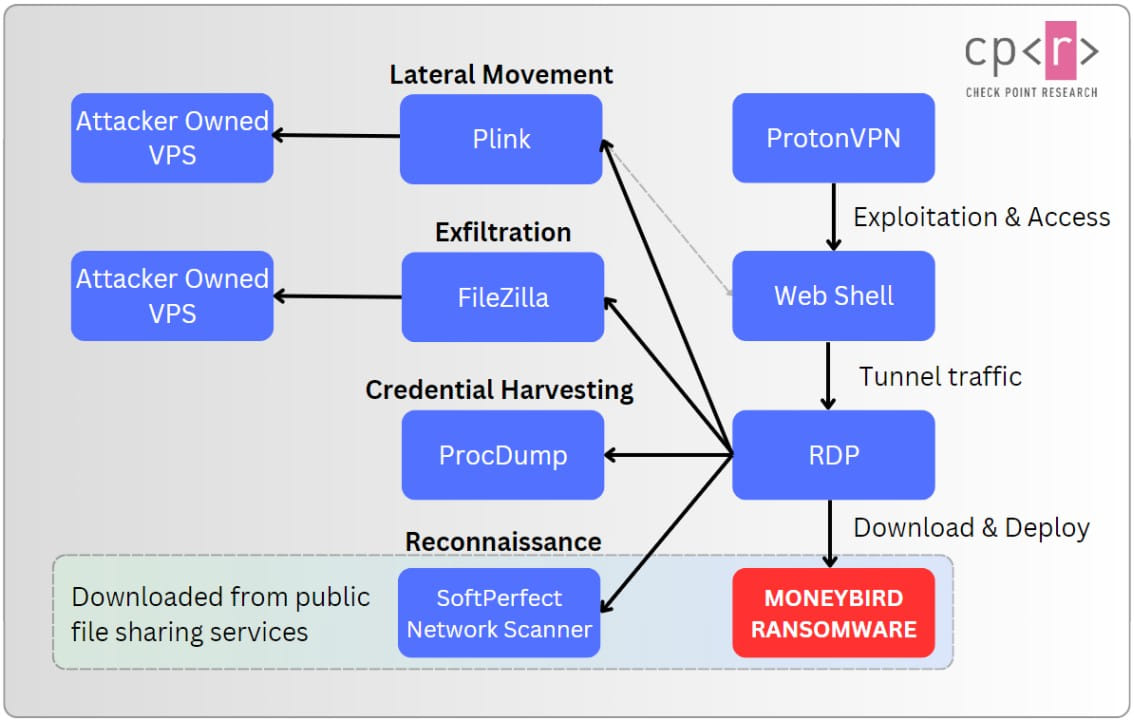
After deploying the webshells, the attackers use open source tools that help in network reconnaissance using SoftPerfect Network Scanner, lateral movement, secure communication using Plink/PuTTY, stealing credentials with ProcDump and data exfiltration using FileZilla.
In the next phase of the attack, Agrius retrieves the Moneybird ransomware executable from legitimate file-hosting platforms such as “ufile.io” and “easyupload.io”.
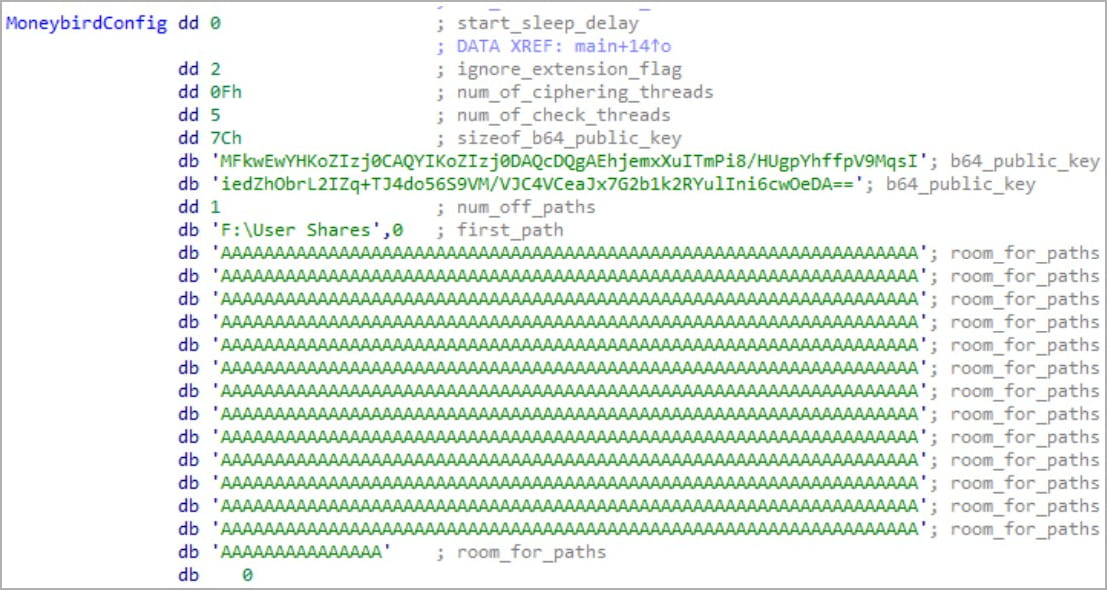
At launch, the C++ ransomware strain will encrypt target files using AES-256 with GCM (Galois/Counter Mode), generating unique encryption keys for each file and appending encrypted metadata to their end.
In the cases observed by Check Point, the ransomware only targeted “F:\User Shares”, a common shared folder on corporate networks used to store corporate documents, databases and other files related to the collaboration.
This narrow targeting indicates that Moneybird is more about disrupting business than locking down affected computers.
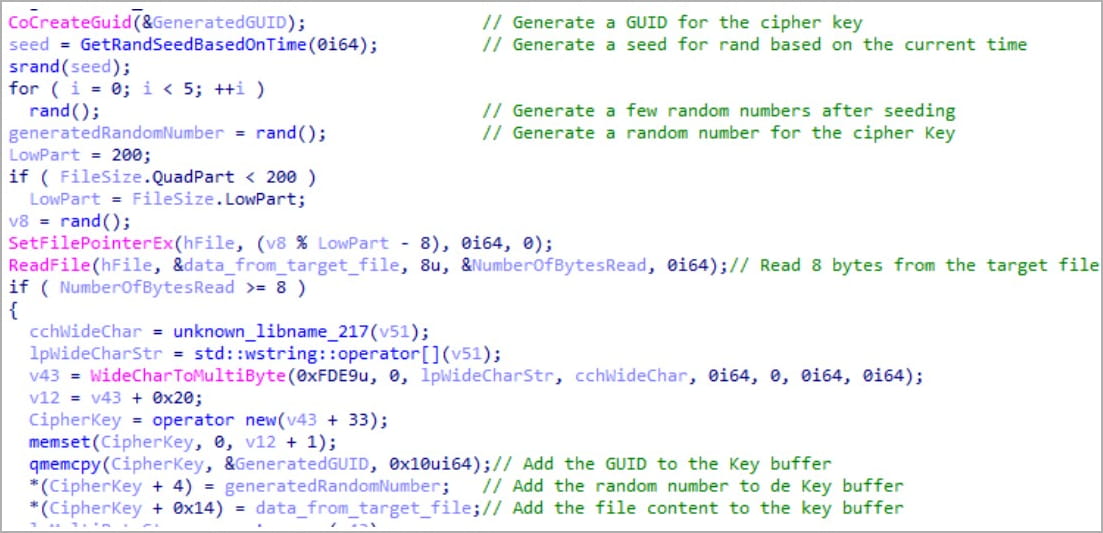
Check Point explains that restoring data and decrypting files would be extremely difficult because the private keys used to encrypt each file are generated using system data GUID, file content, file path and random numbers. .
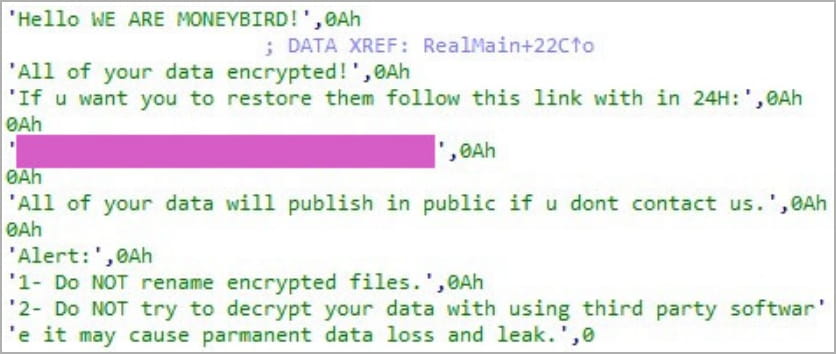
After the encryption, ransom notes are dropped on the affected systems asking the victim to follow the provided link within 24 hours for instructions on how to restore their data.
“Hello WE ARE MONEYBIRD! All your data is encrypted! If you want to restore it, follow this link within 24 hours,” the Moneybird ransom note reads.
Unlike previous Agrius-related attacks, Moneybird is seen as ransomware, rather than a windshield wiper, intended to generate revenue to fund the malicious operations of threat actors.
However, in the case seen by Check Point Research, the ransom demand was so high that it was known from the start that a payment was unlikely to be made, making the attack essentially destructive.
“Yes, negotiations could be possible, but the demand was extremely high, which leads us to believe that this is part of the trick. They knew that nobody would pay, so damages and data leaks were expected. This was not a windshield wiper,” Eli Smadga, research group leader at Check Point Research, told BleepingComputer.
A simple but effective ransomware
Check Point explains that Moneybird lacks command-line scanning capabilities that allow for victim-specific configurations and greater deployment versatility and instead relies on a built-in configuration blob.
This means that the ransomware’s behavior parameters are preset and cannot be easily adjusted for every target or circumstance, making the strain unsuitable for mass campaigns.
For Agrius, however, Moneybird remains an effective business disruption tool, and further development leading to the release of newer and better versions could make it a formidable threat to a wider range of Israeli organizations.
[ad_2]
Source link
