[ad_1]

Threat actors linked to the IceFire ransomware operation are now actively targeting Linux systems around the world with a new dedicated encryptor.
SentinelLabs security researchers found that the gang penetrated the networks of several media and entertainment organizations around the world in the past few weeks, starting in mid-February, according to a report shared in advance with BleepingComputer.
Once inside their networks, attackers deploy their new malware variant to encrypt victims’ Linux systems.
When executed, IceFire ransomware encrypts files, appends the ‘.ifire’ extension to the filename, and then covers its tracks by deleting itself and the binary.
It is also important to note that IceFire does not encrypt all files on Linux. The ransomware strategically avoids encrypting specific paths, allowing critical parts of the system to remain operational.
This calculated approach aims to avoid a complete system shutdown, which could cause irreparable damage and even greater disruption.
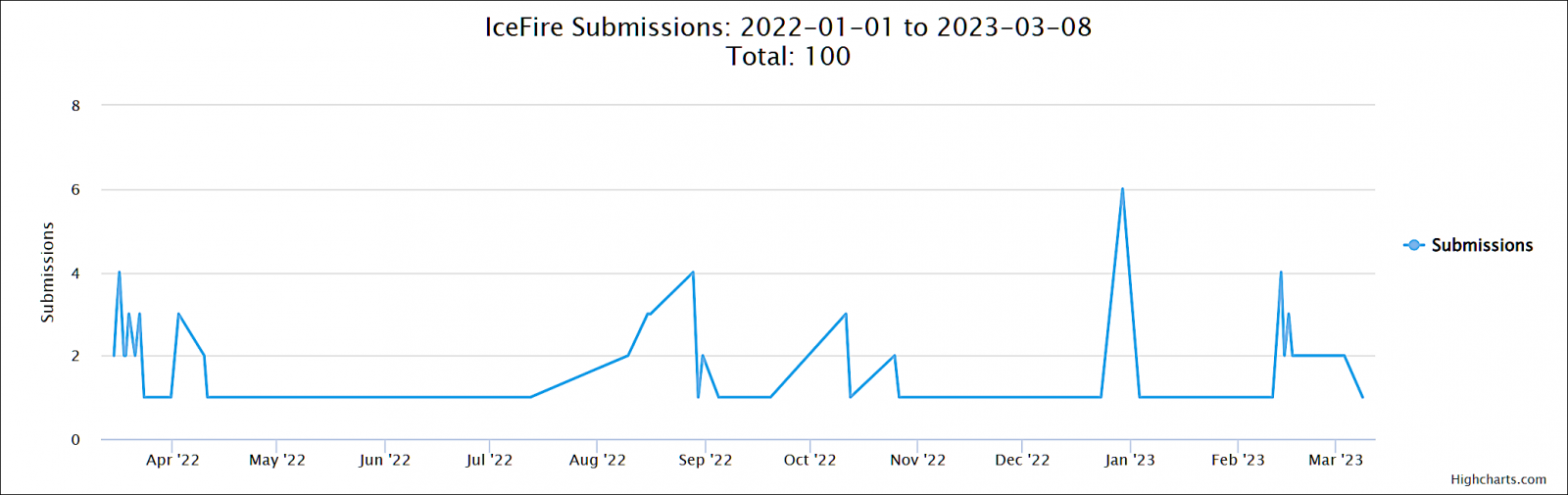
Active for at least March 2022 and mostly inactive since late November, IceFire ransomware returned in early January in new attacks, as shown by submissions on the ID-Ransomware platform.
IBM Aspera Faspex targeting
IceFire operators are exploiting a deserialization vulnerability in IBM Aspera Faspex file sharing software (tracked as CVE-2022-47986) to hack into vulnerable target systems and deploy their ransomware payloads.
This high-severity pre-authentication RCE vulnerability was patched by IBM in January and has been exploited in attacks since early February [1, 2] surface management company after attack Assetnote published a technical report containing the exploitation code.
CISA too added the security breach of its catalog of vulnerabilities exploited in the wild in February 2021, ordering federal agencies to patch their systems until March 14.
“Compared to Windows, it is more difficult to deploy ransomware against Linux, especially on a large scale. Many Linux systems are servers: typical infection vectors like phishing or unwanted downloads are less effective,” explains Sentinel Labs.
“To overcome this, actors are turning to exploiting application vulnerabilities, as demonstrated by operator IceFire by deploying payloads through an IBM Aspera vulnerability.”
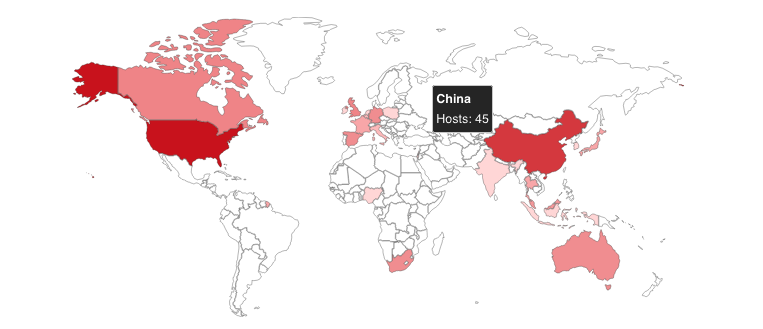
Shodan shows more than 150 Aspera Faspex servers online presentations, mostly in the United States and China.
Most ransomware strains encrypt Linux servers
IceFire ransomware’s decision to expand Linux targeting after previously focusing on attacking Windows systems alone is a strategic shift that aligns with other ransomware groups that have also begun attacking Linux systems in recent years. last years.
Their decision fits a trend that companies have moved to VMware ESXi virtual machines on Linux, which offer improved device management and much more efficient resource management.
After deploying their malware to ESXi hosts, ransomware operators can use a single command to encrypt victims’ Linux servers in bulk.
Although the IceFire ransomware does not specifically target VMware ESXi virtual machines, its Linux encryptor is equally effective, as shown by victims’ encrypted files submitted to the ID-Ransomware platform for analysis.
“This development for IceFire reinforces the growing popularity of Linux-targeted ransomware through 2023,” SentinelLabs says.
“While the groundwork was laid in 2021, the Linux ransomware trend accelerated in 2022 as illustrious groups added Linux encryptors to their arsenal.”
Similar ciphers have been released by several other ransomware gangs, including Conti, LockBit, Hello Kitty, BlackMatter, REvil, AvosLocker, RansomEXXAnd Hive.
Emsisoft CTO Fabien Wosar previously told BleepingComputer that other ransomware gangs (in addition to the ones we’ve already discussed), including Babuk, GoGoogle, Snatch, PureLocker, Mespinoza, RansomExx/Defray, and DarkSide, have been developing and deploying their own Linux encryptors during of attacks.
[ad_2]
Source link
