[ad_1]

Mobile app vulnerabilities exposed post-2012 Hyundai and Genesis car models to remote attacks that unlocked and even started the vehicles.
Yuga Labs security researchers discovered the issues and explored similar attack surfaces in the SiriusXM “smart vehicle” platform used in cars from other manufacturers (Toyota, Honda, FCA, Nissan, Acura and Infinity ) that allowed them to “unlock, remote start, locate them, flash them, and honk them.
At this time, the researchers have not published detailed technical accounts of their findings, but have shared information on Twitter, in two separate threads (hyundai, SiriusXM).
Hyundai problems
Hyundai and Genesis’ mobile apps, named MyHyundai and MyGenesis, allow authenticated users to start, stop, lock and unlock their vehicles.
After intercepting the traffic generated by the two applications, the researchers analyzed it and were able to extract the API calls for further investigation.
They found that owner validation is performed based on the user’s email address, which was included in the JSON body of POST requests.
Then analysts discovered that MyHyundai did not require email confirmation upon registration. They created a new account using the target’s email address with an extra control character at the end.
Finally, they sent an HTTP request to the Hyundai endpoint containing the spoofed address in the JSON token and the victim’s address in the JSON body, bypassing the validity check.
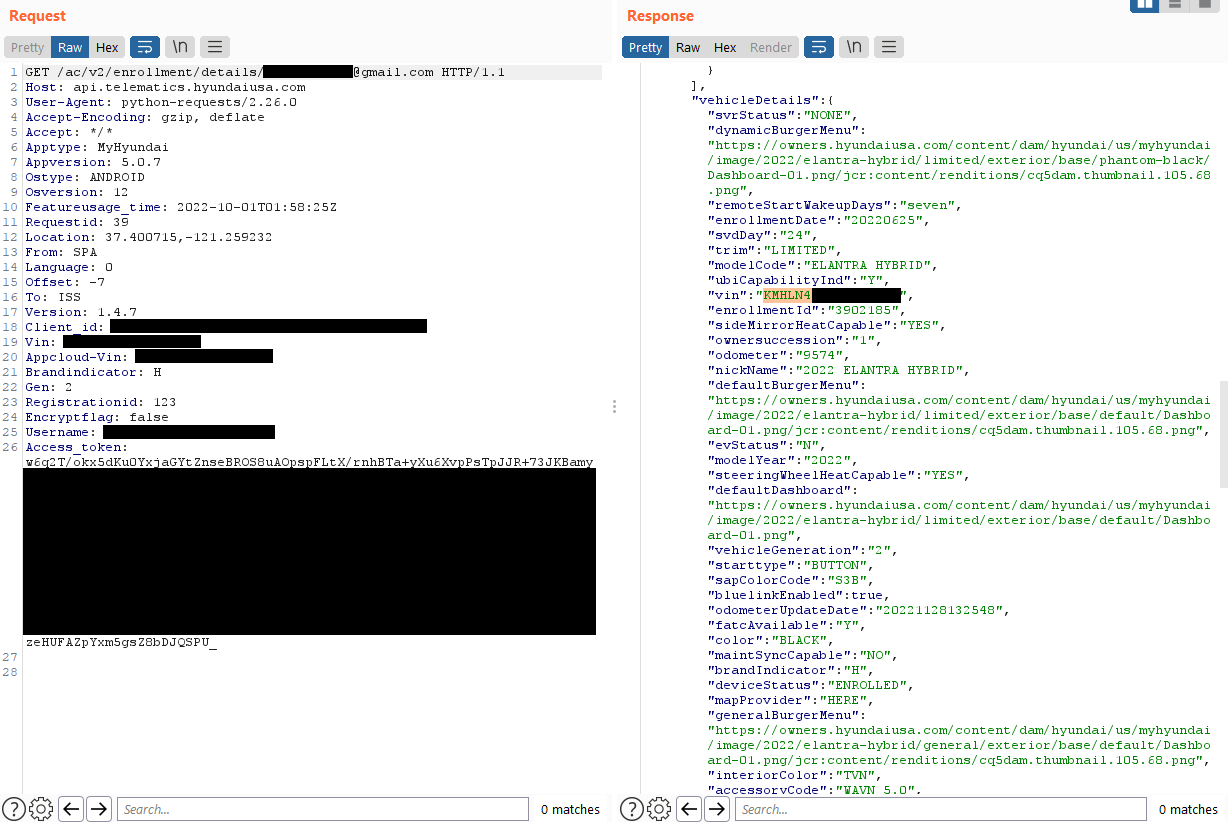
To verify that they could use this access for an attack on the car, they tried to unlock a Hyundai car used for research. A few seconds later, the car unlocks.
The multi-stage attack was eventually integrated into a custom Python script, which only needed the target’s email address for the attack.
Since exploiting this involved many steps, we took all the necessary requests to exploit it and put it into a python script that only needed the victim’s email address. After entering this, you can then execute all commands on the vehicle and support the real account. pic.twitter.com/Bz5G5ZvHro
—Sam Curry (@samwcyo) November 29, 2022
SiriusXM issues
SiriusXM is, among other things, an automotive telematics service provider used by more than 15 car manufacturers. The provider claims to operate 12 million connected cars that run more than 50 services under a unified platform.
Yuga Labs analysts found that mobile apps for Acura, BMW, Honda, Hyundai, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru and Toyota use SiriusXM technology to implement remote vehicle management functionality .
They inspected the Nissan app’s network traffic and discovered that it was possible to send forged HTTP requests to the endpoint just by knowing the target’s vehicle identification number (VIN).
The response to the unauthorized request contained the target’s name, phone number, address and vehicle details.
Considering that VINs are easy to locate on parked cars, usually visible on a plate where the dashboard meets the windshield, an attacker could easily access them. These identification numbers are also available on sites specializing in the sale of cars, so that potential buyers can consult the history of the vehicle.
In addition to disclosing information, requests can also contain commands to perform actions on cars.
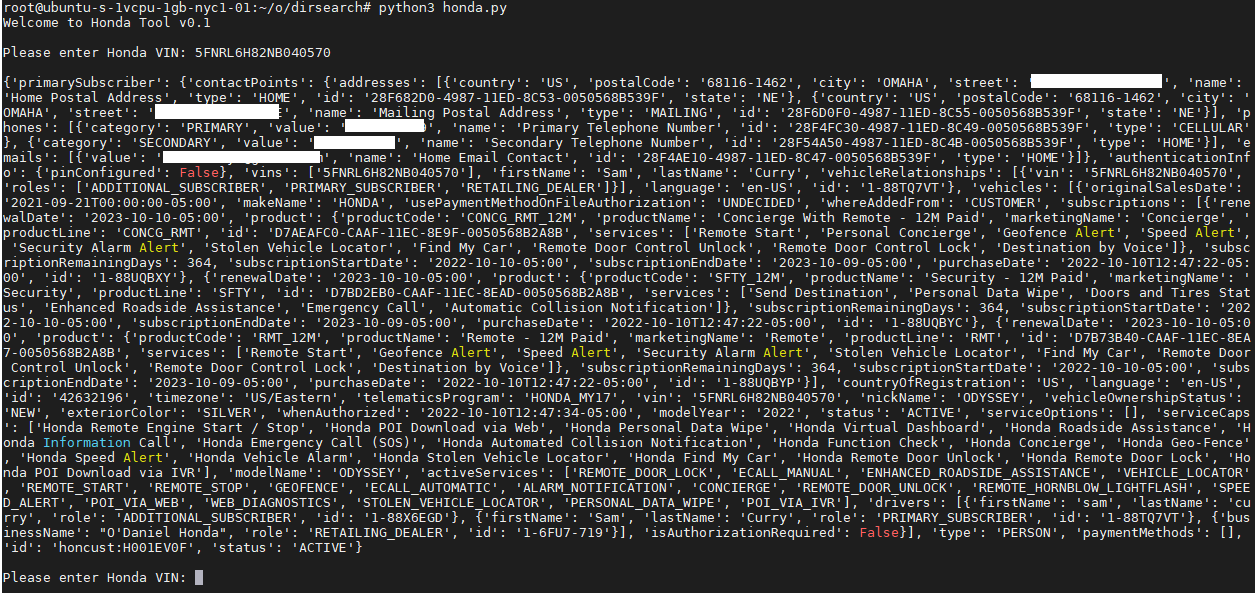
BleepingComputer has contacted Hyundai and SiriusXM to ask if the above issues have been exploited against real customers, but has not received a response at press time.
Prior to releasing the details, Yuga Labs informed Hyundai and SiriusXM of the defects and associated risks. Both vendors have patched the vulnerabilities.
[ad_2]
Source link
