[ad_1]

Remote desktop connections are such a powerful magnet for hackers that an exposed connection can average more than 37,000 times per day from various IP addresses.
During this phase, the attacks are automated. But once they get the right access credentials, hackers start manually searching for important or sensitive files.
Hackers invade RDP
An experiment using high interaction honeypots with an RDP connection accessible from the public web shows how relentless the attackers are and that they operate on a daily schedule very similar to office hours.
For three months, researchers from GoSecurea threat research and response company headquartered in the United States and Canada, recorded nearly 3.5 million login attempts to its RDP honeypot system.
Andreanne Bergeron, cybersecurity researcher at GoSecure, explained at the NorthSec cybersecurity conference in Montreal, Canada, that the honeypots are linked to a research program that aims to understand attackers’ strategies that could be translated into prevention tips.
The honeypot has been running intermittently for over three years and has been running steadily for over a year but the data collected for the presentation represents only three months, between July 1 and September 30, 2022.
During this time, the honeypot was hit 3,427,611 times from over 1,500 IP addresses. However, the number of attacks for the whole year reached 13 million login attempts.
To whet the appetite of attackers, the researchers named the system to appear to be part of a bank’s network.
As expected, the compromise attempts relied on brute force attacks based on multiple dictionaries and the most common username was “Administrator” and some variation of it (e.g. short version, different language, or case of letters).
In some 60,000 cases, however, the attacker did some scouting before trying to find the correct connection and ran usernames that are obviously out of place in the set below.
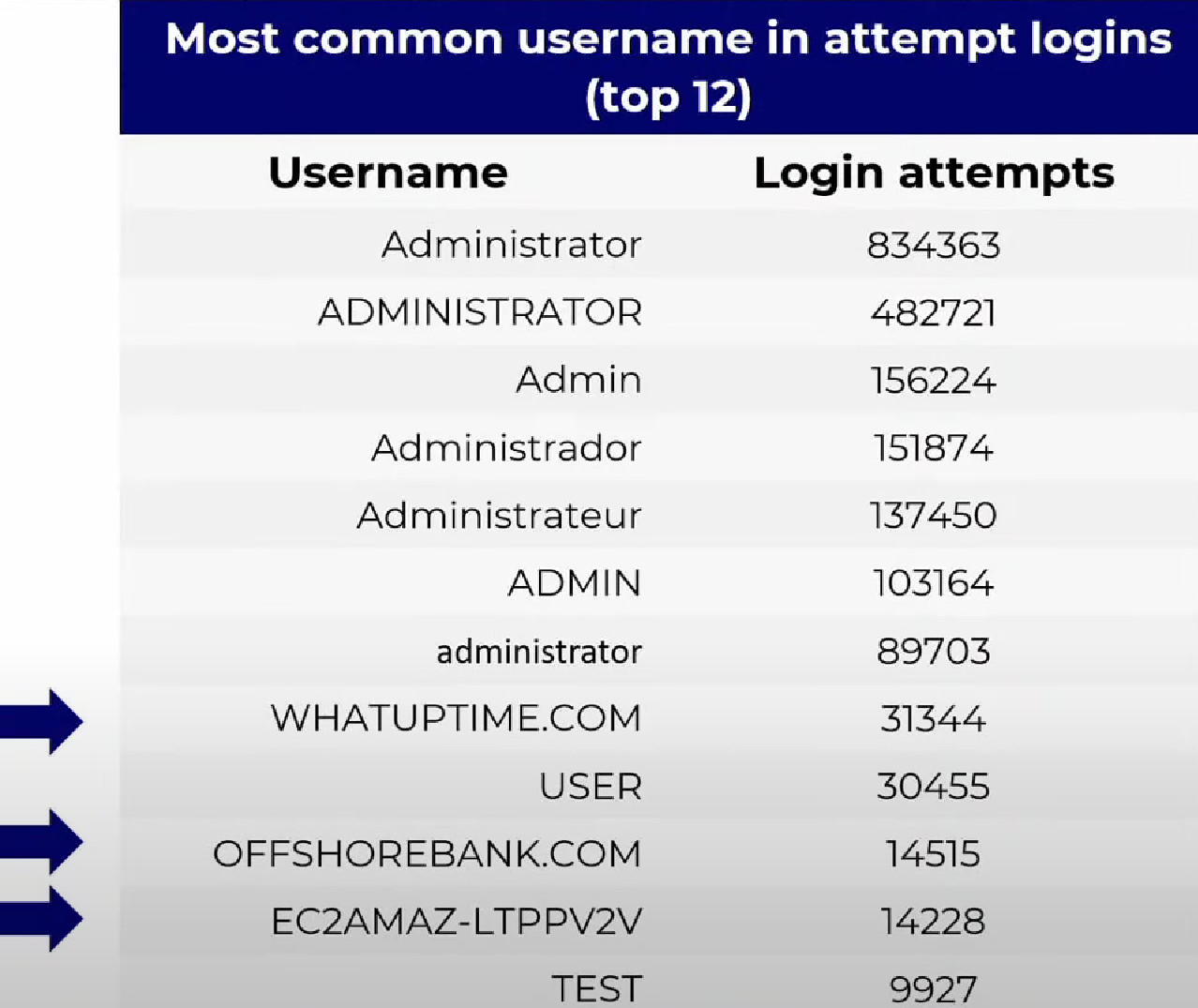
Bergeron explained that the three odd usernames in the image above are related to the honeypot system (RDP certificate and host names, and hosting provider).
The presence of this data in the first 12 logins tried indicates that at least some of the hackers did not blindly test the credential pairs to log in, but first gathered information about the victim. .
Bergeron told us that the system collected hashes of passwords and researchers were able to restore weaker ones. The results showed that the most common strategy was to use a variation of the RDP certificate, followed by variations of the word “password” and a simple string of up to ten digits.
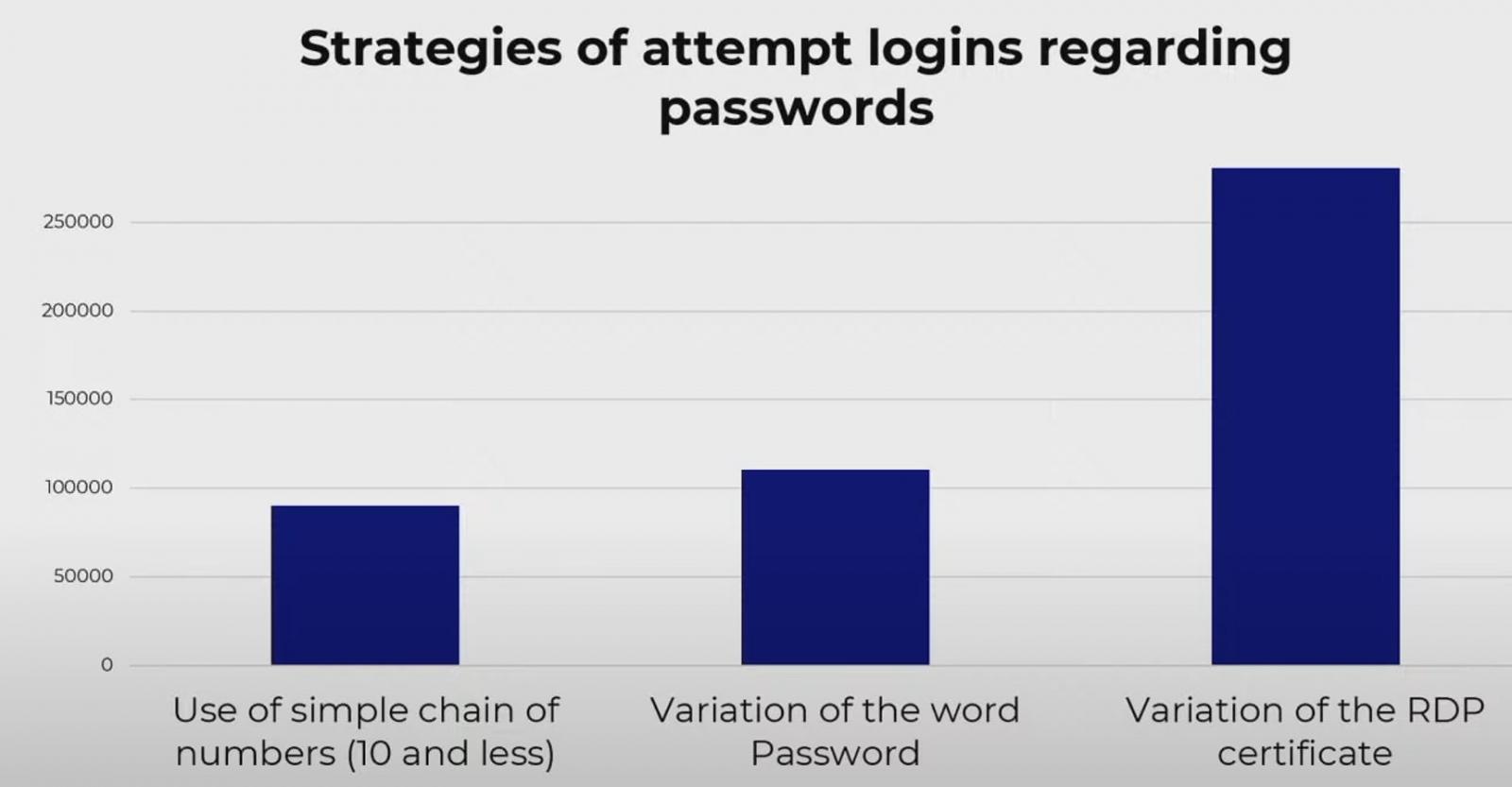
An interesting observation when correlating these statistics with attack IP addresses is that the RDP certificate name was used exclusively in connection attempts from IP addresses in China (98%) and Russia (2 %).
However, this does not necessarily mean that the attackers are from both countries but are using infrastructure in both regions.
Another observation is that many attackers (15%) combined thousands of passwords with just five usernames.
A normal working day
Human involvement in the attack became more evident after this initial brute force phase when hackers began snooping around the system looking for valuable data.
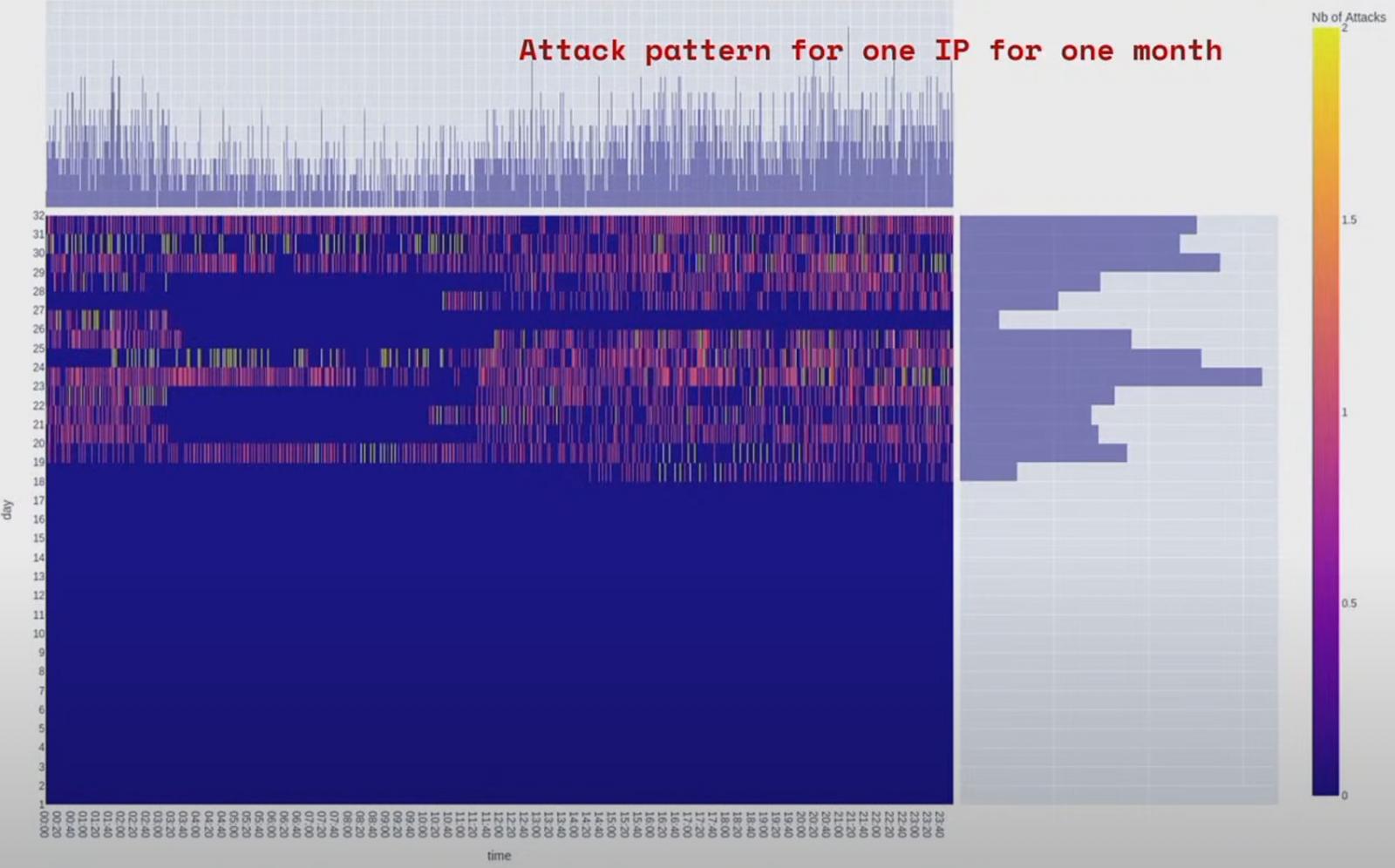
Digging deeper into the data, Bergeron created a heatmap for the IP addresses targeting the honeypot and noticed that the activity formed a daily pattern with pauses indicating the hackers were taking a break.
Many activities span four hours and up to eight hours, although some sessions lasted up to 1 p.m. This suggests human intervention, at least to launch the attacks, and seems to follow some timeline.
The fact that brute force activity stopped during weekend days adds weight to this observation, perhaps suggesting that attackers are treating hacking activity as regular work.
It should be noted that these were automated login attempts that did not require human oversight once the script was properly modified.
In one example, Bergeron noticed an eight-hour gap between attacks and deduced that this might indicate an attacker working shifts.
The human touch and level of sophistication was also visible in the attacks customized for the target (14%) as well as the addition of a delay between each login attempt, to mimic the activity of a real person.
Human involvement in the attack became more evident after this initial brute force phase when hackers began snooping around the system looking for valuable data.
Although researchers reduced the difficulty of logging into the honeypot with the “admin/admin” credential pair, Bergeron told BleepingComputer that only 25% of hackers started crawling the machine for important files.
Bergeron also said the honeypot was empty, which likely explains why only a quarter of the attackers lingered to search for data. However, the next step in the investigation would be to populate the server with fake corporate files and monitor the attacker’s movements and actions.
To record and store attack data, which includes live video streams of the adversary’s RDP session, the research used PyrRDPan open source interception tool developed at GoSecure by Olivier Bilodeauthe company’s director of cybersecurity research and chairman of the NorthSec conference.
Lecture by Andréanne Bergeron at NorthSec this year is titled “Human vs. Machine: The Level of Human Interaction in Automated Attacks Targeting the Remote Desktop Protocol”. All the interventions of the two stages of the conference are available on NorthSec YouTube Channel.
[ad_2]
Source link
