[ad_1]

Security researchers have discovered a new malicious browser extension called Rilide, which targets Chromium-based products like Google Chrome, Brave, Opera, and Microsoft Edge.
The malware is designed to monitor browser activity, take screenshots, and steal cryptocurrency through scripts injected into web pages.
Trustwave SpiderLabs researchers found that Rilide mimics benign Google Drive extensions to hide in plain sight while abusing Chrome’s built-in features.
The cybersecurity firm detected two separate campaigns that distributed Rilide. One used Google Ads and Aurora Thief to load the extension using a Rust loader. The other distributed the malicious extension using the Ekipa Remote Access Trojan (RAT).
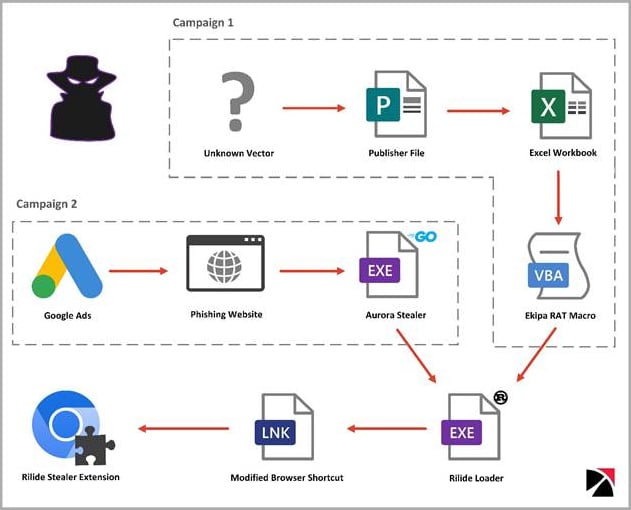
Although the origin of the malware is unknown, Trustwave reports that it has overlaps with similar extensions sold to cybercriminals. Meanwhile, parts of its code were recently leaked to an underground forum due to a dispute between cybercriminals over an unresolved payment.
A parasite in the browser
Rilide’s loader modifies web browser shortcut files to automate the execution of the malicious extension dropped on the compromised system.
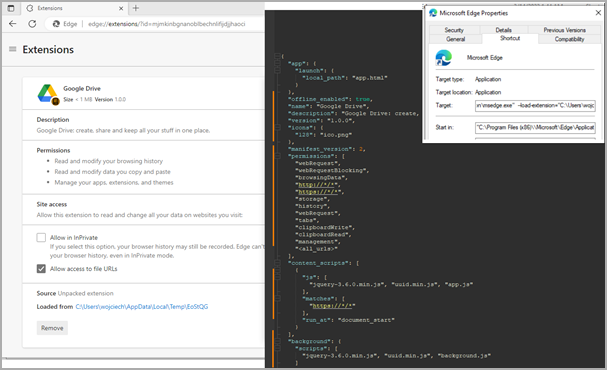
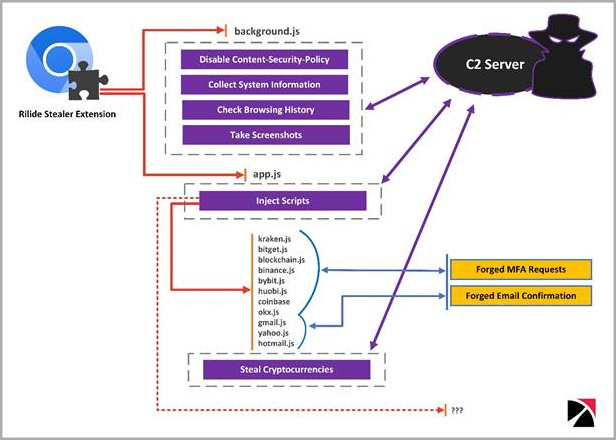
Upon execution, the malware executes a script to attach a listener that monitors when the victim switches tabs, receives web content, or web pages finish loading. It also checks whether the current site matches a list of available targets from the command and control server (C2).
If there is a match, the extension loads additional scripts injected into the webpage to steal information related to cryptocurrencies, email account credentials, etc. from the victim.
The extension also disables “Content Security Policy”, a security feature designed to protect against cross-site scripting (XSS) attacks, to freely load external resources that the browser would normally block.
In addition to the above, the extension regularly exfiltrates browsing history and can also capture screenshots and send them to C2.
Bypass two-factor authentication
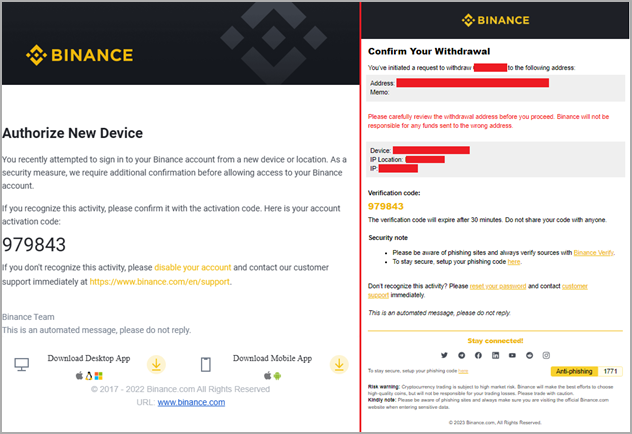
An interesting feature of Rilide is its 2FA bypass system, which uses fake dialogues to trick victims into entering their temporary codes.
The system is activated when the victim initiates a cryptocurrency withdrawal request to an exchange service targeted by Rilide. The malware intervenes at the right time to inject the script in the background and process the request automatically.
Once the user enters their code in the fake dialog, Rilide uses it to complete the withdrawal process to the threat actor’s wallet address.
“Email confirmations are also overridden on the fly if the user enters the mailbox using the same web browser”, explains Turstwave in the report.
“The withdrawal request email is replaced with a device authorization request prompting the user to provide the authorization code.”
Rilide showcases the growing sophistication of malicious browser extensions that now come with live monitoring and automated money-stealing systems.
While the deployment of Manifesto v3 on all Chromium-based browsers will improve resistance against malicious extensions, Trustwave comments that it will not eliminate the problem.
[ad_2]
Source link
