[ad_1]

Hackers are now actively scanning thousands of WordPress websites for vulnerable versions of the Essential Addons for Elementor plugin during massive internet scans, attempting to exploit a critical account password reset flaw disclosed earlier in the day. month.
The critical severity flaw is identified as CVE-2023-32243 and affects Essential Addons for Elementor versions 5.4.0 through 5.7.1, allowing unauthenticated attackers to arbitrarily reset administrator account passwords and take over sites website.
The defect that impacted over a million websites was discovered by PatchStack on May 8, 2023 and patched by the vendor on May 11, with the release of version 5.7.2 of the plugin.
Scale of operation
On May 14, 2023, researchers published a proof-of-concept (PoC) exploit on GitHub, making the tool widely available to attackers.
At the time, a BleepingComputer reader and website owner reported that his site had been hit by hackers who reset the admin password by exploiting the flaw. Yet the extent of the exploitation was unknown.
A Wordfence report released yesterday sheds more light, with the company claiming to have observed millions of attempts to detect the plugin’s presence on websites and blocked at least 6,900 exploit attempts.
The day after the flaw was disclosed, WordFence logged 5,000,000 survey scans looking for the plugin’s ‘readme.txt’ file, which contains the plugin’s version information, and therefore determines whether a site is vulnerable.
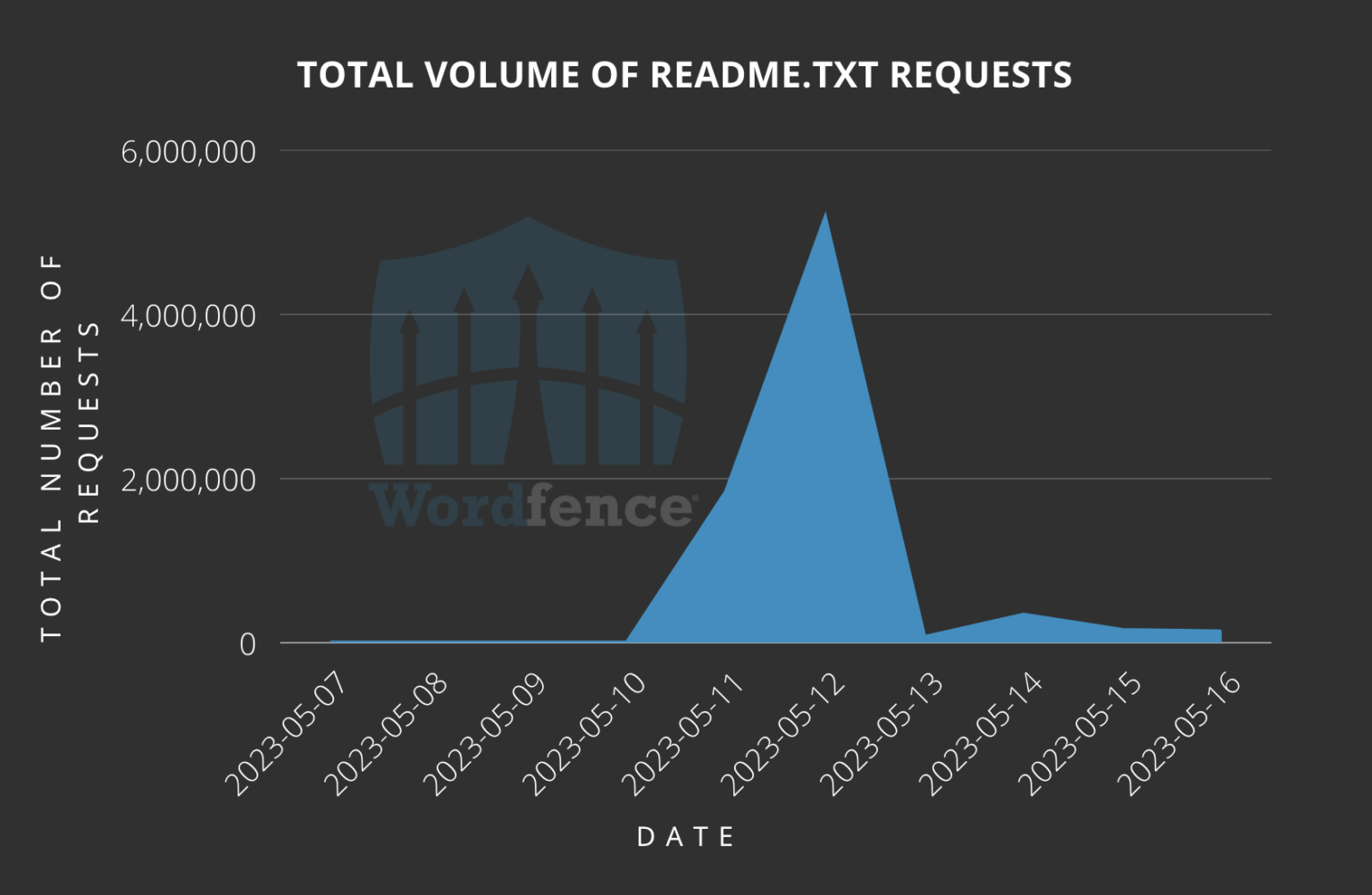
“While there are services that probe installation data for legitimate purposes, we believe this data indicates that attackers began searching for vulnerable sites as soon as the vulnerability was revealed,” Wordfence comments in the report.
Most of these requests came from just two IP addresses, “185.496.220.26” and “185.244.175.65”.
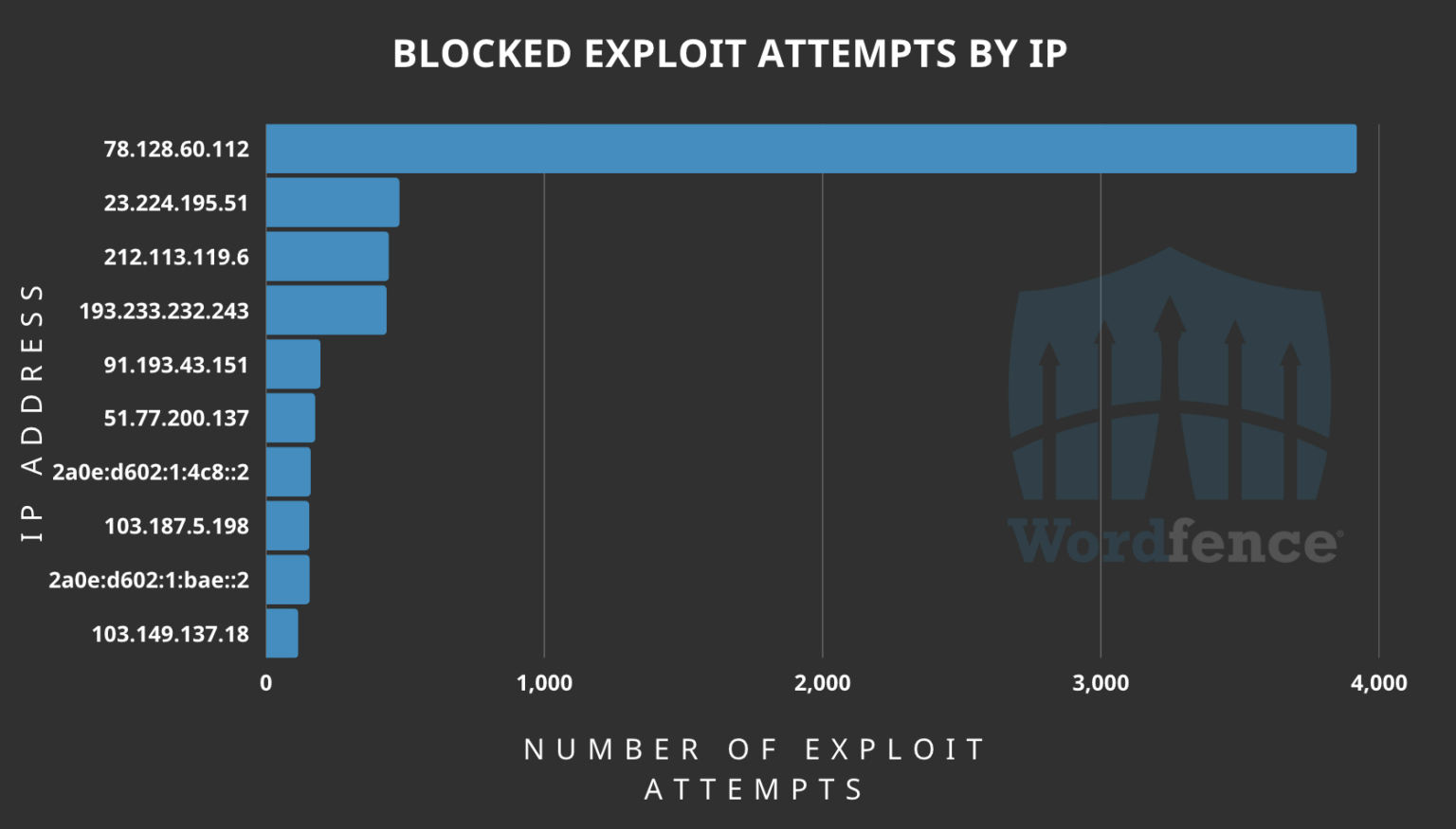
Regarding exploit attempts, the IP address ‘78.128.60.112’ had a considerable amount of volume, using the PoC exploit posted on GitHub. Other high-ranking attacking IPs count between 100 and 500 attempts.
Website owners using the “Essential Addons for Elementor” plugin are advised to apply the available security update by immediately installing version 5.7.2 or later.
“Given the ease with which this vulnerability can be successfully exploited, we strongly recommend that all users update the plugin as soon as possible to ensure that their site is not compromised by this vulnerability,” advises Wordfence.
Additionally, website administrators should use the indicators of compromise listed in Wordfence’s report and add the offending IP addresses to a blocklist to stop these and future attacks.
Users of Wordfence’s free security package will be covered by protection against CVE-2023-32243 on June 20, 2023, so they are also at risk currently.
[ad_2]
Source link
