[ad_1]

A major cybercrime firm known as “Lemon Group” is said to have pre-installed malware known as “Guerilla” on nearly 9 million Android-based smartphones, watches, TVs and TV boxes.
Threat actors use Guerrilla to load additional payloads, intercept one-time passwords from SMS, set up a reverse proxy from the infected device, hijack WhatsApp sessions, etc.
According to a report by Trend Microwhose analysts uncovered the massive criminal enterprise and presented details about it during the recent Black Hat Asia conference, part of the attackers’ infrastructure overlaps the Triada Trojan Operation from 2016.
Triada was a banking Trojan found pre-installed in 42 models of Android smartphones of low-cost Chinese brands that sell their products all over the world.
Trend Micro says it first exposed the Lemon group in February 2022, and soon after, the group was reportedly rebranded as “Durian Cloud SMS.” However, the attackers’ infrastructure and tactics remained unchanged.
“While we have identified a number of activities that Lemon Group performs for big data, marketing and advertising companies, the core business involves the use of big data: analyzing massive amounts of data and the corresponding characteristics manufacturer shipments, different advertising content obtained from different users at different times, and hardware data with detailed software push,” the Trend Micro report explains.
Malware installation
Trend Micro did not specify how Lemon Group infects devices with the malware containing Guerilla, but did say that the devices its analysts examined had been re-flashed with new ROMs.
Analysts have identified more than 50 different ROMs infected with initial malware loaders, targeting various Android device vendors.
“The criminal group has infected millions of Android devices, primarily cell phones, but also smartwatches, smart TVs and more,” reads the description of Trend Micro’s Black Hat speech.
“The infection turns these devices into mobile proxies, tools for stealing and selling text messages, online social media and messaging accounts, and monetization through ads and click fraud.”
Possible ways to achieve this compromise include supply chain attacks, compromised third-party software, a compromised firmware update process, or the enlistment of insiders in the manufacturing or distribution chain of the product.
Trend Micro says it originally purchased an Android phone and extracted its “ROM image” to discover the modified firmware implanted by Lemon Group.
This device had a modification on the system library ‘libandroid_runtime.so’ to contain additional code that would decrypt and run a DEX file.
Code from the DEX file is loaded into memory and executed by Android Runtime to enable the main plugin used by the attackers, called “Sloth”, and also provide its configuration, which contains a Lemon Group domain to be used for communications.
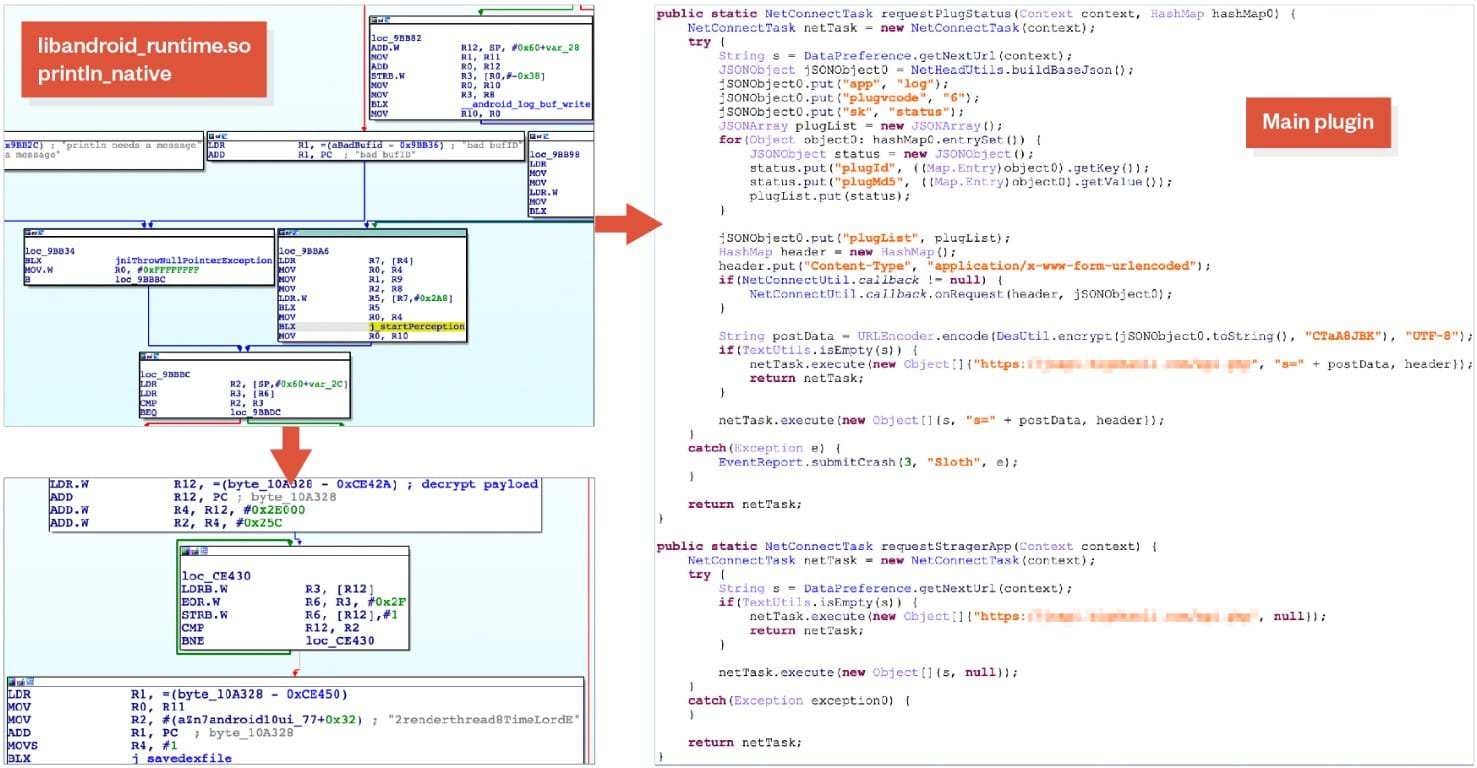
Guerrilla Malware
The main Guerrilla malware plugin loads additional plugins dedicated to performing specific functionality, including:
- SMS plug-in: Intercepts one-time passwords for WhatsApp, JingDong and Facebook received by SMS.
- Proxy plug-in: Configures a reverse proxy from the infected phone allowing attackers to use the victim’s network resources.
- Cookie plug-in: empties Facebook cookies from the app’s data directory and exfiltrates them to the C2 server. It also hijacks WhatsApp sessions to deliver unwanted messages from the compromised device.
- Splash plug-in: Displays intrusive advertisements to victims when they use legitimate apps.
- silent plug-in: Install additional APKs received from the C2 server or uninstall existing apps as instructed. Installing and launching the app is “silent” in the sense that it happens in the background.
These functions allow the Lemon Group to establish a diversified monetization strategy which could include selling compromised accounts, hijacking network resources, offering application installation services, generating fraudulent ad impressions, offering proxy services and verified account services via SMS phone (PVA).
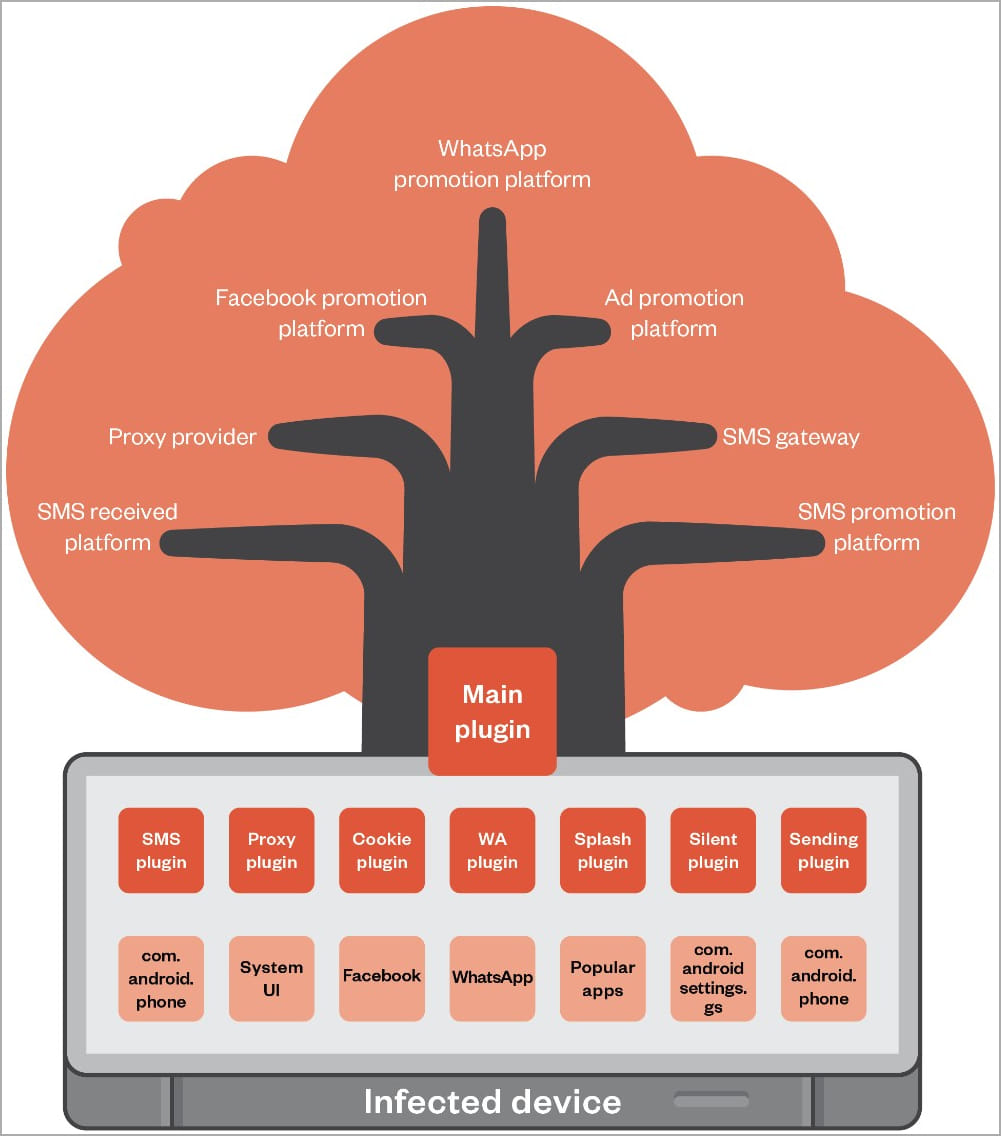
Global impact
Trend Micro reports that Lemon Group previously claimed control of nearly nine million devices across 180 countries on its service offering site. The most affected countries are the United States, Mexico, Indonesia, Thailand and Russia.
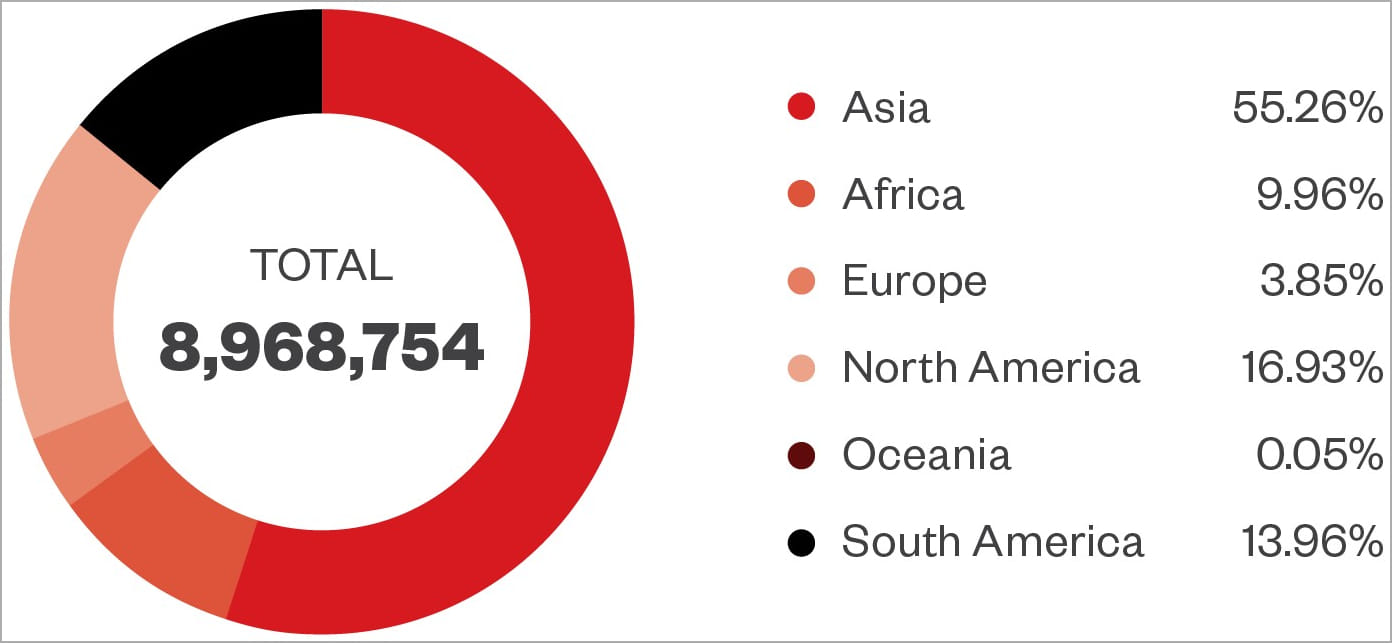
“Furthermore, through our telemetry data, we have confirmed that there are millions of infected devices being exploited globally. The main cluster of these devices are found in Southeast Asia and Eastern Europe. , however, this is a truly global issue,” Trend Micro said.
Trend Micro suggests that the actual number of Android devices infected with Guerrilla may be higher. However, these devices have not yet communicated with the attackers’ command and control servers as they are still awaiting purchase.
By monitoring the operation, analysts detected more than 490,000 mobile numbers used to generate one-time password requests for SMS PVA services of JingDong, WhatsApp, Facebook, QQ, Line, Tinder and other platforms.
The identification of over half a million compromised devices linked to a single service offered by this cybercrime syndicate signifies a substantial global reach of their malicious operations.
BleepingComputer asked Trend Micro where they purchased the pre-infected phone, how it was sold, and which brands were affected, but no response was immediately available.
[ad_2]
Source link
