[ad_1]

Threat authors use a well-designed Pokemon NFT card game website to distribute NetSupport remote access tool and take control over victims’ devices.
pokemon go website[.]io”, which is still online at the time of writing, claims to be home to a new NFT card game built around the Pokemon franchise, providing users with strategic fun as well as NFT investment benefits.
Given the popularity of Pokemon and NFTs, it shouldn’t be difficult for the operators of the malicious portal to attract an audience to the site through malspam, social media posts, etc.
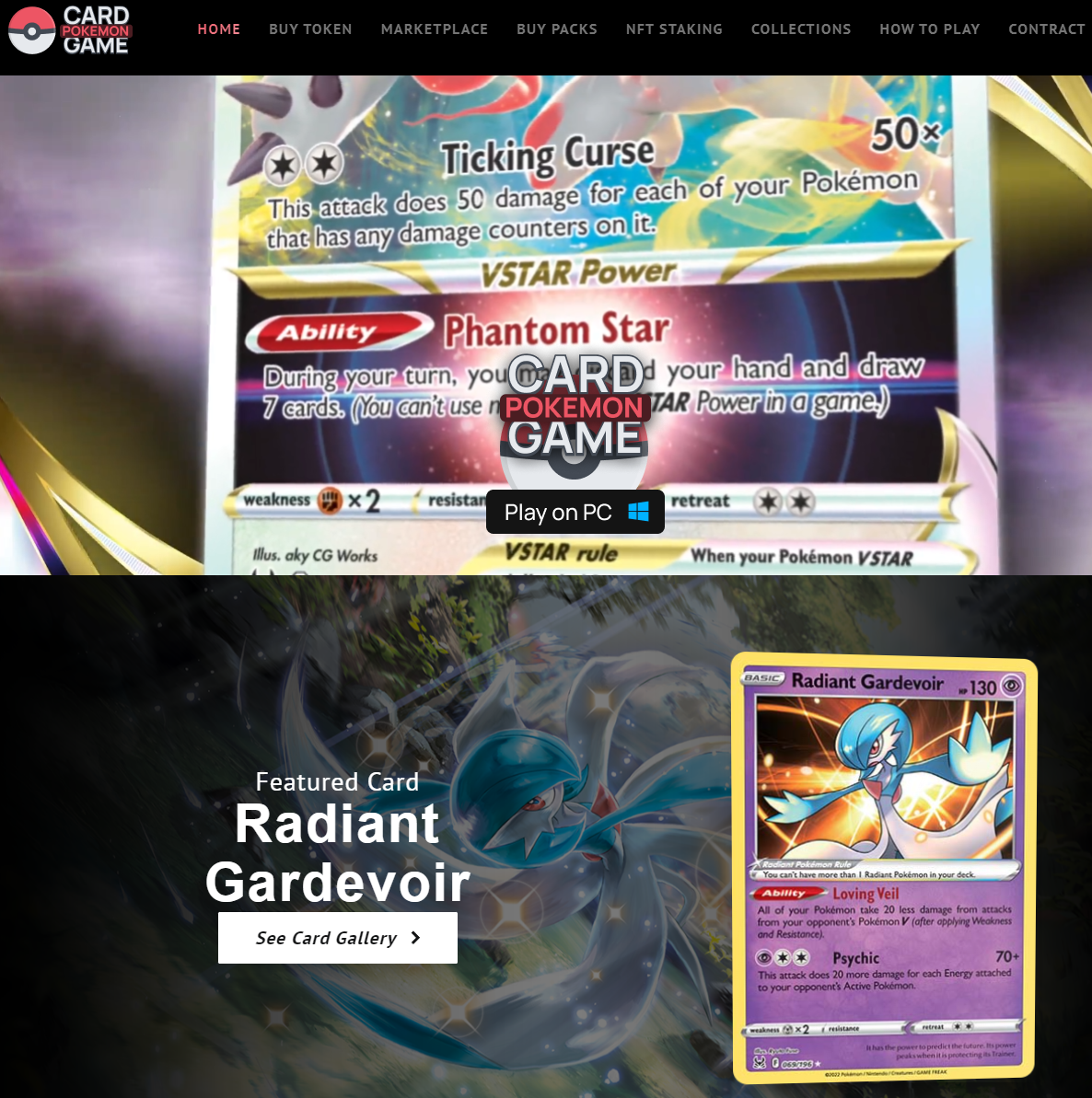
Those who click the “Play on PC” button download an executable that looks like a legitimate game installer but, in reality, installs the NetSupport Remote Access Tool (RAT) on the victim’s system.
The operation was discovered by analysts at A SECONDwhich reports that there was also a second site used in the campaign, at “beta-pokemoncards[.]io”, but it has since been taken offline.
The first signs of activity from this campaign appeared in December 2022, when earlier samples retrieved from VirusTotal showed the same operators pushing a fake Visual Studio file instead of the Pokemon game.
NetSupport RAT Removal
The NetSupport RAT executable (“client32.exe”) and its dependencies are installed in a new folder in the %APPDATA% path. They are set to “hidden” to help evade detection by victims performing manual file system inspections.
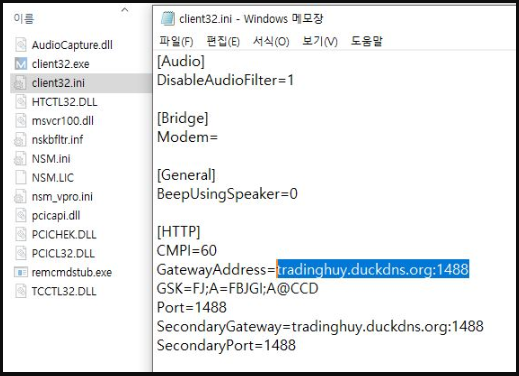
Additionally, the installer creates an entry in the Windows startup folder to ensure that the RAT will run when the system starts.
As NetSupport RAT (NetSupport Manager) is a legitimate program, hackers commonly use it in the hope that it will evade security software.
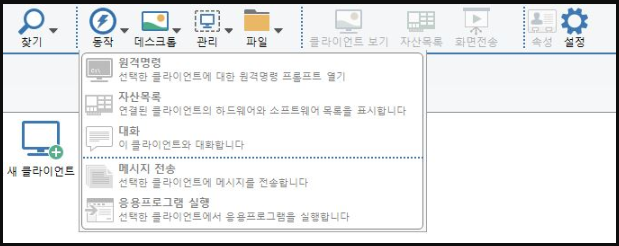
Threat actors can now connect to a user’s device remotely to steal data, install other malware, or even attempt to spread further across the network.
Although NetSupport Manager is a legitimate software product, it is commonly used by hackers as part of their malicious campaigns.
In 2020, Microsoft has warned on phishing actors using COVID-19 themed Excel files who dropped NetSupport RAT on recipients’ computers.
In August 2022, a campaign targeting the WordPress sites with fake Cloudflare DDoS protection pages installed NetSupport RAT and Raccoon Stealer on victims.
NetSupport Manager supports remote screen control, screen recording, system monitoring, remote system grouping for better control and many connectivity options including network traffic encryption.
That said, the consequences of such an infection are wide-ranging and serious, mainly regarding unauthorized access to users’ sensitive data and downloading additional malware.
[ad_2]
Source link
