[ad_1]

Threat actors abused an open redirect on the official UK Department for Environment, Food and Rural Affairs (DEFRA) website to direct visitors to fake adult dating sites OnlyFans.
OnlyFans is a content subscription service where paid subscribers have access to photos, videos and private posts from adult models, celebrities and social media personalities.
Since it is a widely used site and the name is recognizable, threat actors have created a series of fake OnlyFans adult dating sites to gain subscribers or steal people’s personal information.
Abusing open redirect on DEFRA
As part of this malicious campaign, threat actors abused an open redirect that looked like a legitimate UK government link, but redirected visitors to the fake dating site OnlyFans.
An example of this redirect is below:
http://riverconditions.environment-agency.gov.uk/relatedlink.html?class=link&link=https://pentestpartners.comRedirects are legitimate URLs on website web addresses that automatically redirect users from the initial site to another URL, usually to an external site.
For example, a website might have a redirect like www.example.com/redirect/www.google.com, which when clicked will automatically redirect the user to Google.
A open redirect can be modified by anyone, allowing threat actors and scammers to create redirects from a legitimate site to any site of their choice.
This allows threat actors to abuse open redirects and surface legitimate links in search results that send visitors to websites under their control to display phishing forms or distribute malware.
The malicious campaign abusing the open redirect on the DEFRA river conditions site was discovered last week by analysts from Pen Test Partners, who shared their findings with BleepingComputer.
“On Tuesday afternoon, a colleague of mine, Adam Bromiley, noticed an open redirect on the UK Environment Agency website. It came up when doing a Google search when he was looking for SoC (hardware System on Chip) datasheets!”, explained The report by Pen Test Partners.
These redirects were listed as Google search results promoting porn and adult sites, likely after being added to websites that were then indexed by Google’s web crawlers.
Source: Pen Test Partners
As you can see from the network requests monitored by Fiddler, clicking on the “riverconditions.environment-agency.gov.uk/relatedlink.html” link took visitors through a series of redirects that eventually landed them on various bogus adult sites, such as ‘kap5vo.cyou’, ‘https://rvzqo.impresivedate[.]com’, and more.
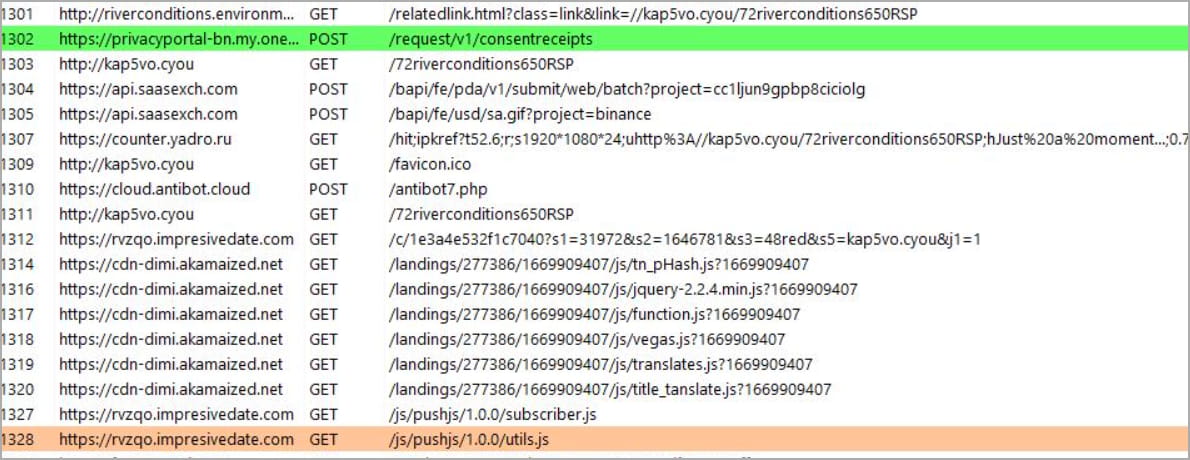
Source: Pen Test Partners
For example, when rvzqo.impresivedate[.]com is first opened, it shows a large animated OnlyFans logo, followed by the next fake dating site.
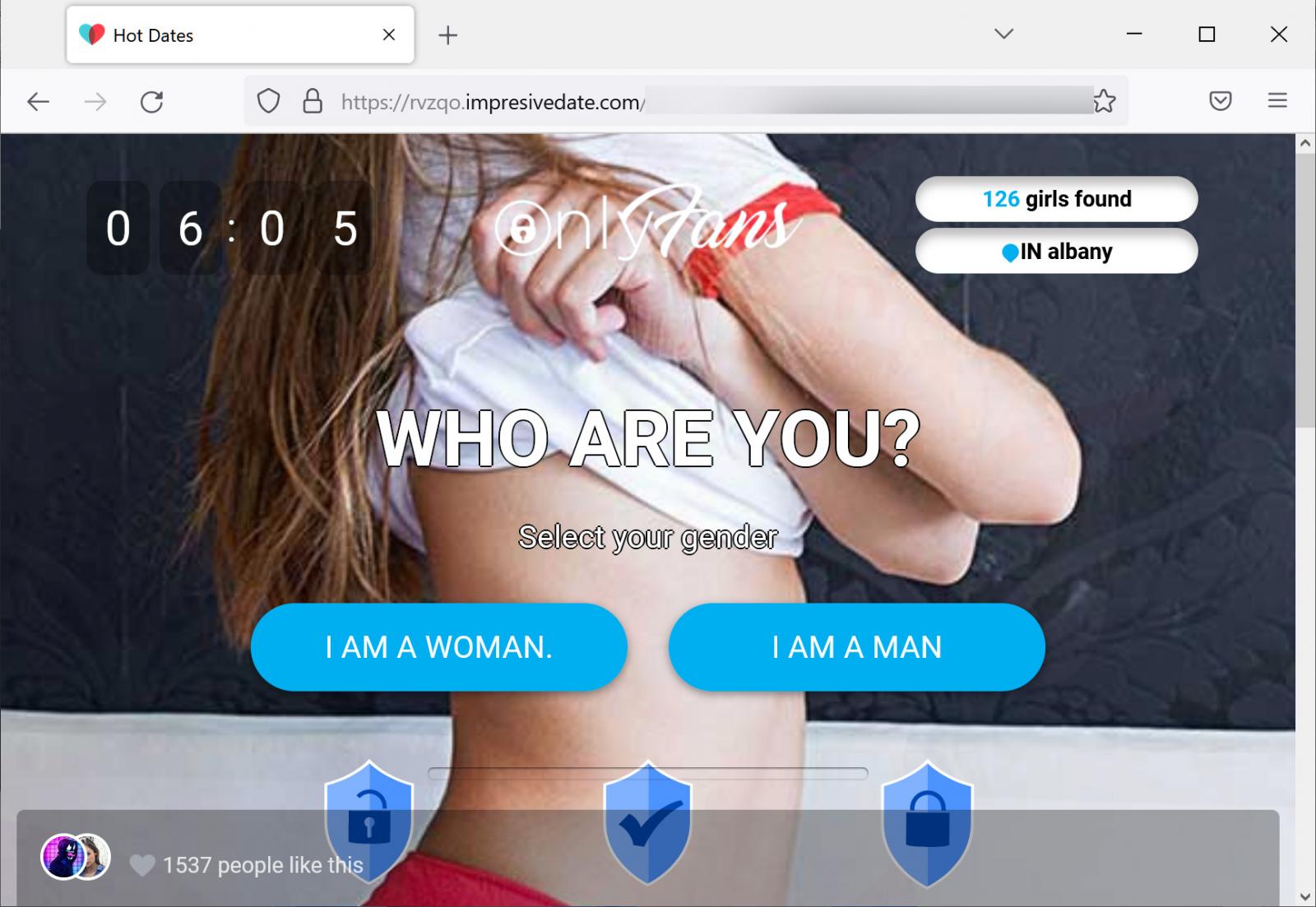
Source: BleepingComputer
These bogus OnlyFans sites prompt the user to answer a series of questions regarding the type of “date” they are looking for and eventually redirect them once again to adult “cheating” sites.
While most “.gov.uk” sites accept safety reports via HackerOne, the Environment Agency is not part of the scheme. Therefore, there was a 24-hour delay between the discovery of the open redirect and its reporting to the correct person at Defra.
The abused DEFRA domain at “riverconditions.environment-agency.gov.uk” was taken offline and its DNS records removed approximately 48 hours after Pen Test Partners submitted its report. Unfortunately, the website is still inaccessible at the time of this writing.
At the same time, a second researcher noticed the same issue via Google search results and made the issue public on Twitter.
BleepingComputer contacted DEFRA about the redirect attack and was told the agency was aware of the technical issues and moved the content to a new location which remains available.
“We are aware of the technical issues with the Conditions of the Thames website. Our teams have worked quickly to move content to a new site which the public can now easily access,” an Agency spokesperson said. UK for the Environment at BleepingComputer.
The abuse of open government redirect sites to push adult phishing sites is nothing new.
In 2020, a malicious SEO campaign abused a open redirect on many US government websiteslike weather.gov, to redirect visitors to porn sites.
Another malicious campaign that year abused an open redirect on HHS.gov to redirect visitors to COVID-19 phishing sites that spread malware.
More recently, we have reported attackers exploiting open redirects on Snapchat and American Express sites to direct visitors to Microsoft 365 phishing sites.
[ad_2]
Source link
