[ad_1]
A threat actor associated with cyber espionage operations since at least 2017 lures victims with fake Android VPN software that is a Trojan version of legitimate SoftVPN and OpenVPN software.
Researchers say the campaign was “highly targeted” and aimed to steal contact and call data, device location, as well as messages from multiple apps.
VPN Service Impersonation
The operation was attributed to an advanced threat actor being tracked as Bahamut, which is believed to be a group of mercenaries providing for-hire hacking services.
Lukas Stefanko, malware analyst at ESET, says Bahamut has repackaged SoftVPN and OpenVPN apps for Android to include malicious code with spying features.
By doing so, the actor ensured that the app would still provide the VPN functionality to the victim while exfiltrating sensitive information from the mobile device.
To hide their operation and for credibility purposes, Bahamut used the name SecureVPN (which is a legit VPN service) and created a fake website [thesecurevpn] to distribute their malicious application.
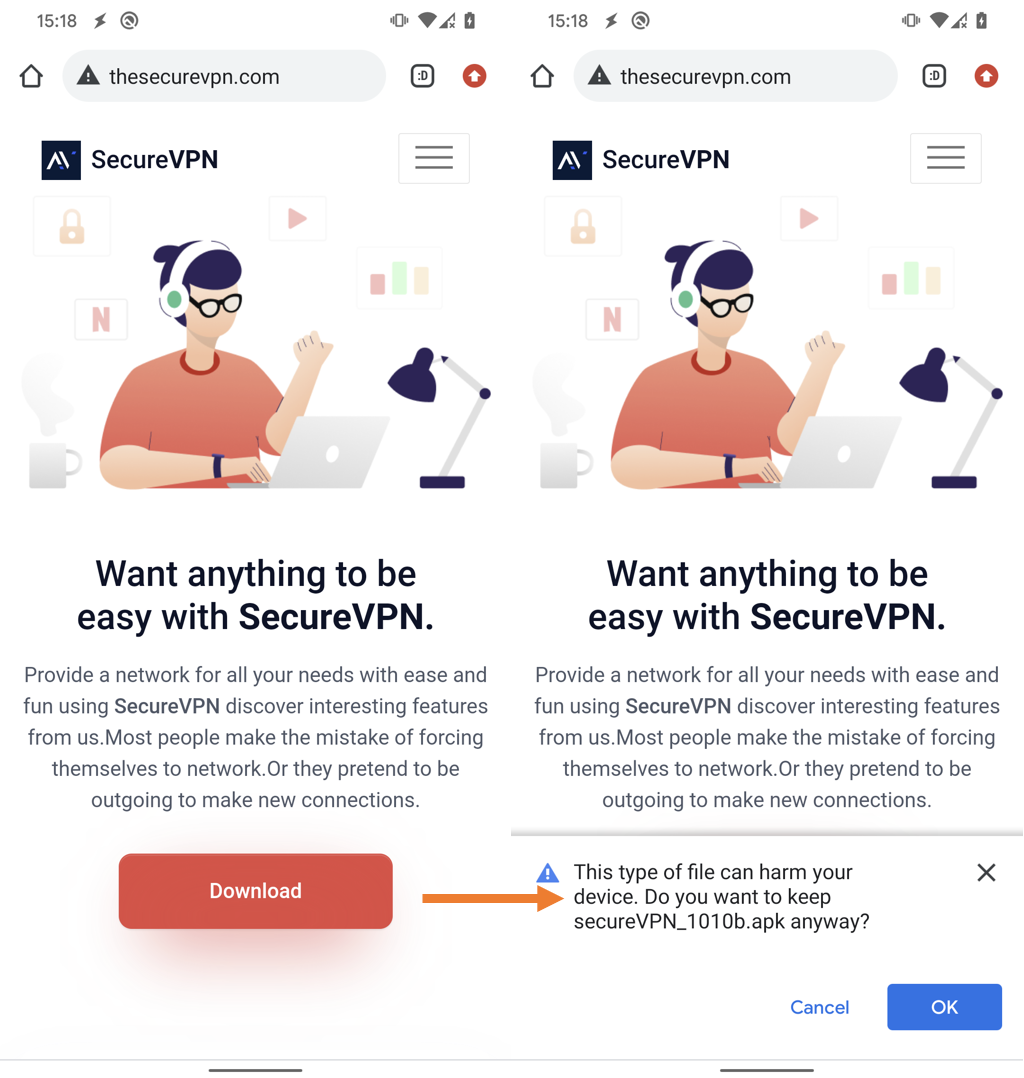
source: ESET
Stefanko says hackers’ scam VPN app can steal contacts, call logs, location details, text messages, spy on chats in messaging apps like Signal, Viber, WhatsApp, Telegram and Facebook Messenger, as well as collect a list of files available in external storage.
The ESET researcher discovered eight versions of Bahamut’s spy VPN app, all with chronological version numbers, suggesting active development.
All of the fake apps included code seen only in operations attributed to Bahamut in the past, such as the SecureChat campaign documented by cybersecurity firms Cyble and CoreSec360 [1, 2].
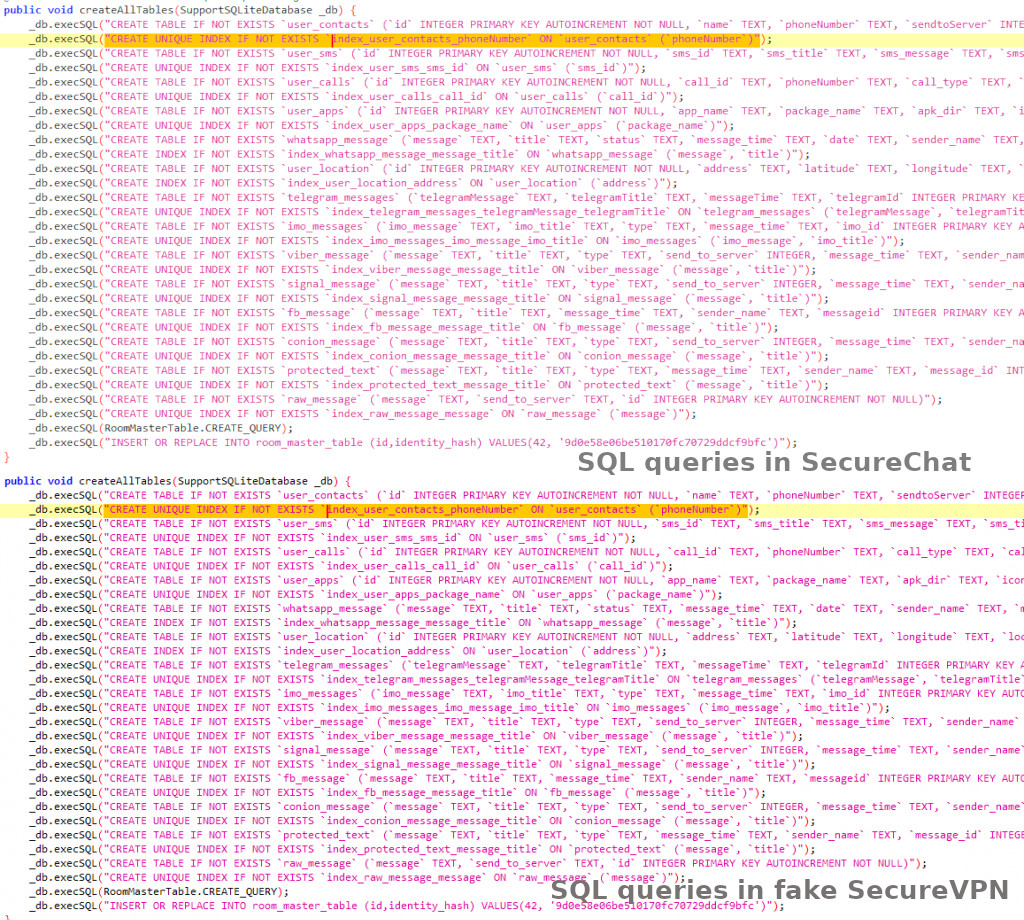
source: ESET
It should be noted that none of the trojanized VPN versions were available through Google Play, the official Android resource repository, another indication of the targeted nature of the operation.
The method of the initial delivery vector is unknown, but it could be anything from email phishing, social media, or other communication channels.
Bahamut Operation Details emerged in the public space in 2017 when reporters from investigative group Bellingcat published a story about the spy actor targeting Middle Eastern human rights activists.
Connecting Bahamut to other threat actors is a tall order given that the group relies heavily on publicly available tools, constantly changes tactics, and its targets are not in any particular region.
However, BlackBerry researchers note to a large extent report on Bahamut in 2020 that the group “seems to be not only well-funded and well-resourced, but also well-versed in research on security and the cognitive biases that analysts often possess”.
Some threat actor groups that Bahamut has been associated with include change of wind and Urpage.
[ad_2]
Source link
