[ad_1]

A new hacking campaign is exploiting flaws in Sunlogin to deploy the Sliver post-exploitation toolkit and launch Windows Bring Your Own Vulnerable Driver (BYOVD) attacks to disable security software.
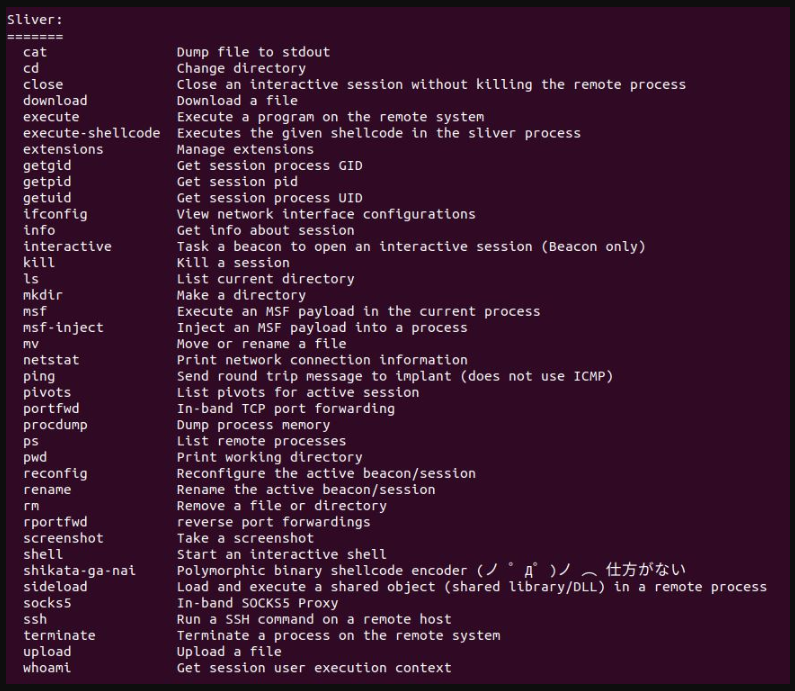
Sliver is a post-exploitation toolkit created by Bishop Fox that threat actors started using as an alternative to Cobalt Strike last summer, using it for network monitoring, running commands, loading reflective DLLs, creating sessions, manipulating processes, etc.
According to a report by AhnLab Security Emergency Response Center (ASEC), recently observed attacks target two 2022 vulnerabilities in Sunlogin, a remote control software from a Chinese developer.
After exploiting these vulnerabilities to compromise a device, attackers use the PowerShell script to open reverse shells or install other payloads, such as Sliver, Gh0st RAT or the XMRig Monero coin miner.
Leading a malicious driver to the attack
The attack begins by exploiting the CNVD-2022-10270 / CNVD-2022-03672 RCE vulnerabilities in Sunlogin v11.0.0.33 and earlier, using readily available proof-of-concept (PoC) exploits.
Intruders exploit the flaw to run an obfuscated PowerShell script to disable security products before deploying backdoors.
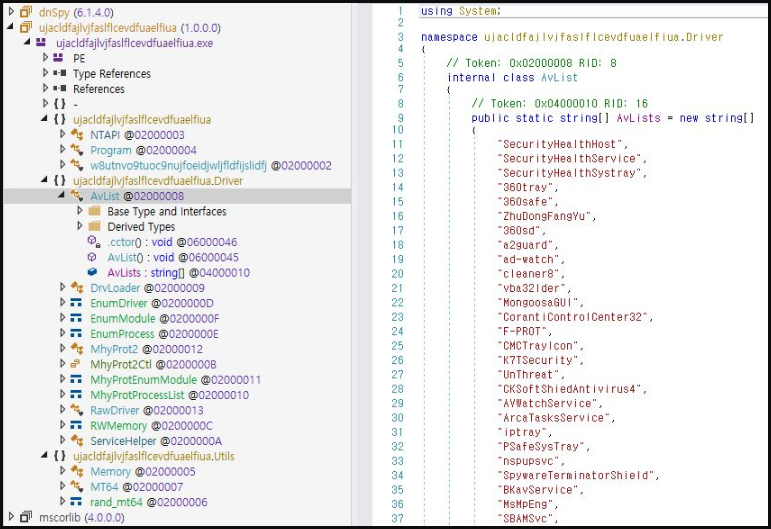
The script decodes a portable .NET executable and loads it into memory. This executable is a modified version of the open source tool Mhyprot2DrvControl, created to abuse vulnerable Windows drivers to perform malicious actions with kernel-level privileges.
Mhyprot2DrvControl specifically abuses the mhyprot2.sys file, a digitally signed anti-cheat driver for Genshin Impact that Trend Micro has observed being used for ransomware attacks since last year.
“Through a simple workaround process, the malware can gain access to the kernel area via mhyprot2.sys,” explains the ASEC in the report.
“The developer of Mhyprot2DrvControl has provided several features that can be used with the elevated privileges through mhyprot2.sys. Among these, the threat actor has used the feature that allows forced termination of processes to develop malware that stop several anti-malware products.”
Once the driver is loaded, hackers exploit its vulnerability to gain Windows kernel privileges, which can then be used to terminate security processes protected from user-mode programs.
The second part of the PowerShell script downloads Powercat from an external source and uses it to run a reverse shell that connects to the C2 server, providing the attacker with remote access to the hacked device.
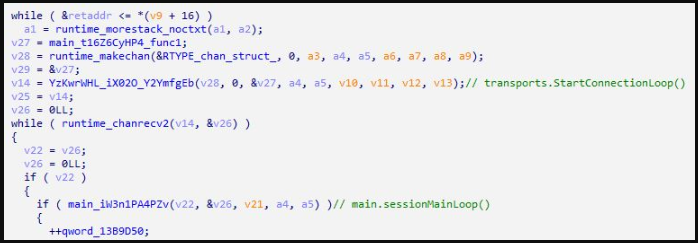
In some cases observed by ASEC, Sunlogin attacks were followed by the installation of a Sliver implant (“acl.exe”). The threat actors used the implant generated by the Sliver framework in “session mode” without using packers.
In other cases, attackers installed the Gh0st RAT (Remote Access Trojan) for remote file management, key logging, remote command execution and exfiltration capabilities of data.
Microsoft recommends that Windows administrators enable the block list of vulnerable drivers to protect against BYOVD attacks.
A Microsoft support article provides information about enabling the blocklist using the Windows Memory Integrity feature or Windows Defender Application Control (WDAC).
Another way to defend against this attack is to block the AV killer hash, “f71b0c2f7cd766d9bdc1ef35c5ec1743”, and monitor event logs for newly installed services named “mhyprot2”.
[ad_2]
Source link
