[ad_1]

Researchers demonstrated how threat actors can abuse GitHub Codespaces’ port forwarding feature to host and distribute malware and malicious scripts.
GitHub Codespaces allows developers to deploy cloud-hosted IDE platforms in virtualized containers to write, modify, and test/run code directly in a web browser.
Since becoming widely available in November 2022, GitHub Codespaces has become a popular choice among developers who prefer it for its preconfigured container-based environment equipped with all the tools and dependencies needed for their projects.
Using GitHub Codespaces as a malware server
In a new report from Trend Micro, researchers demonstrate how GitHub Codespaces can easily be configured to act as a web server for distributing malicious content while potentially avoiding detection as the traffic originates from Microsoft.
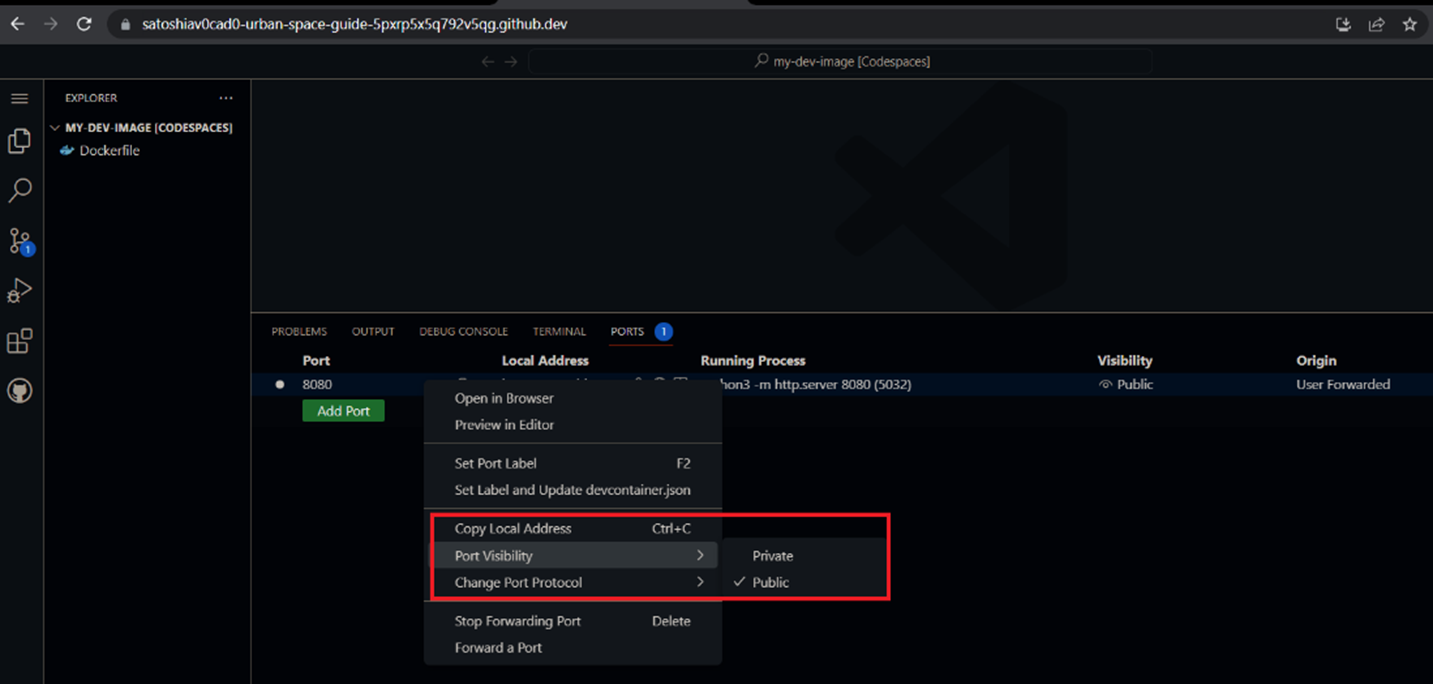
GitHub Codespaces allows developers to forward TCP ports to the public so that external users can test or view applications.
When forwarding ports in a Codespace VM, the GitHub feature generates a URL to access the application running on that port, which can be configured as private or public.
Private port forwarding requires authentication in the form of a token or cookies to access the URL. However, a public port is accessible to anyone who knows the URL without requiring authentication.
Source: Trend Micro
This GitHub feature gives developers flexibility in code demos, but Trend Micro says attackers today can easily abuse it to host malware on the platform.
Theoretically, an attacker could run a simple Python web server, upload malicious scripts or malware to their Codespace, open a web server port on their VM, and give it “public” visibility.
The generated URL can then be used to access hosted files, either for phishing campaigns or to host malicious executables downloaded by other malware.
This is precisely how threat actors abuse other trusted services such as Google Cloud, Amazon AWS, and Microsoft Azure for malware distribution campaigns.
“To validate our threat modeling abuse scenario hypothesis, we ran a Python-based HTTP server on port 8080, forwarded and publicly exposed the port,” reads the Trend Micro Report.
“In the process, we easily found the URL and the absence of cookies for authentication.”
Analysts say that if HTTP is used by default in the Codespaces port forwarding system, developers can set it to HTTPS, increasing the illusion of security for the URL.
Because GitHub is a trusted space, antivirus tools are less likely to raise alarms so threat actors can evade detection at minimal cost.
continue the attack
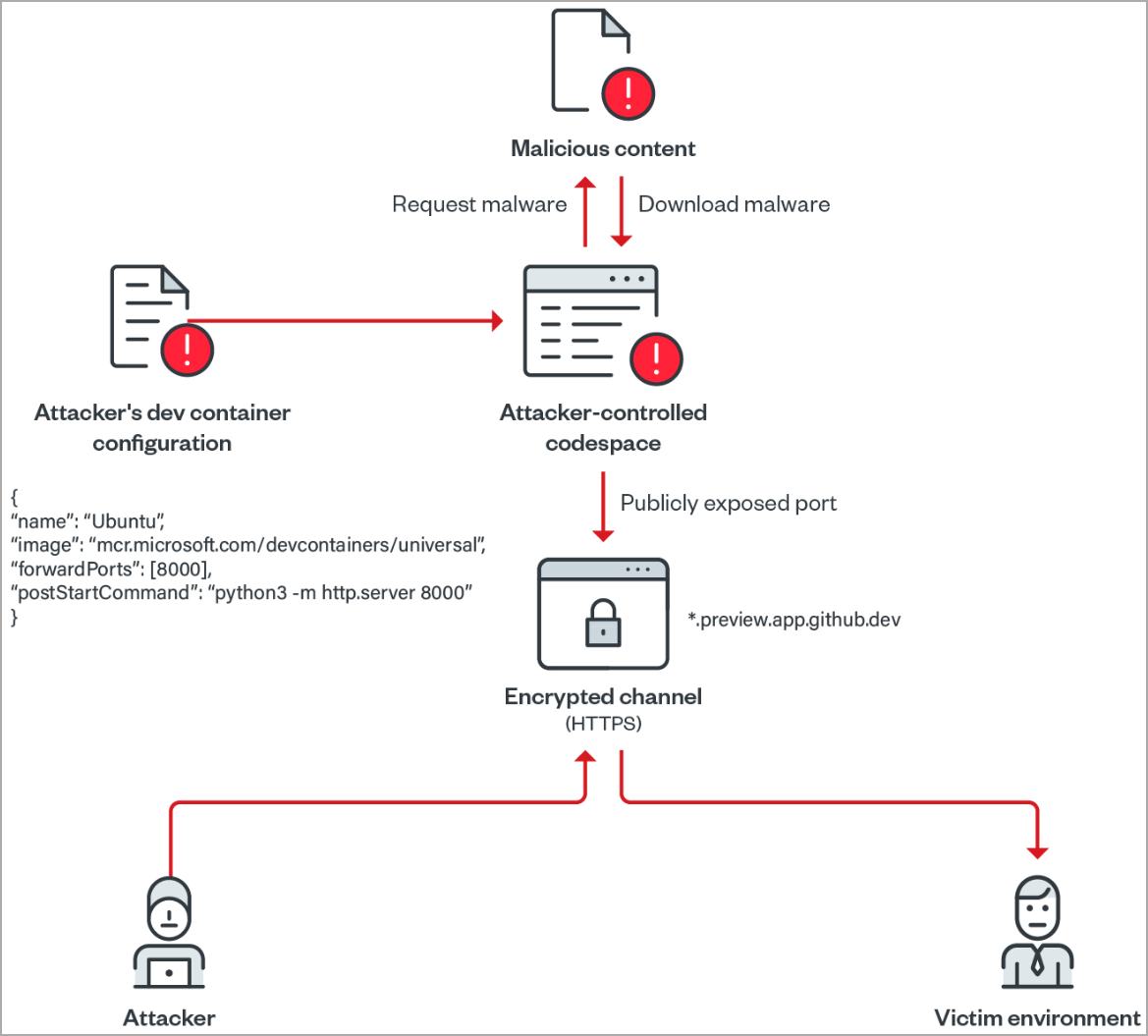
Trend Micro analysts also explore abuse Development Containers in GitHub Codespaces to make their malware distribution operations more efficient.
A “dev container” in GitHub Codespaces is a preconfigured container that contains all the dependencies and tools needed for a specific project. Developers can use it for quick deployment, share it with others, or connect through VCS.
An attacker can use a script to forward a port, run a Python HTTP server, and download malicious files to their Codespace.
Next, the port visibility is set to public, which creates a web server with an open directory that serves the malicious files to the targets.
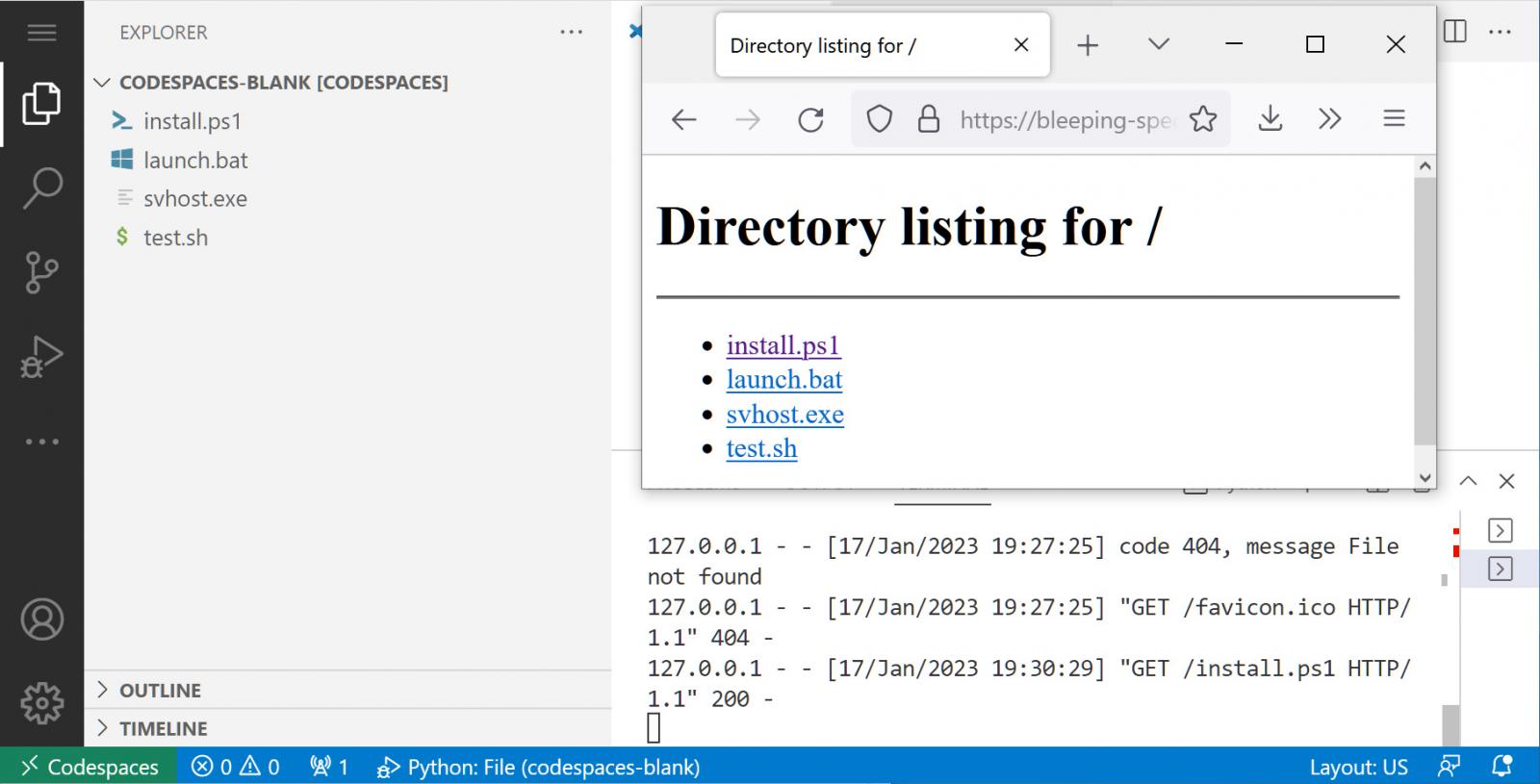
Trend Micro has created a proof-of-concept (PoC) for this, using a 100-second delay after URL access before dropping the web server.
BleepingComputer was able to replicate the creation of a “malicious” web server using Codespaces in less than 10 minutes, with no experience with the feature.
Source: BleepingComputer
“Using such scripts, attackers can easily abuse GitHub codespaces to rapidly spread malicious content by publicly exposing the ports of their codespace environments. Since each codespace created has a unique identifier, the associated subdomain is also unique,” Trend Micro explains in the report.
“This gives the attacker enough ground to create different instances of open directories.”
GitHub’s policy is that inactive codespaces are automatically deleted after 30 daysso attackers can use the same URL for an entire month.
While there is no known abuse of GitHub Codespaces at this time, the report highlights a realistic possibility, as threat actors generally prefer to target “free to use” platforms. which are also approved by security products.
BleepingComputer has contacted GitHub to comment on Trend Micro’s report, but we are still awaiting a response.
[ad_2]
Source link
