[ad_1]

Security researchers warn that cybercriminals are increasingly using Action1 remote access software to persist on compromised networks and to execute commands, scripts and binaries.
Action1 is a remote monitoring and management (RMM) product commonly used by managed service providers (MSPs) and the enterprise to remotely manage endpoints on a network.
The software allows administrators to automate patch management and security update deployment, install software remotely, catalog hosts, troubleshoot endpoints, and get on-time reporting real.
While these types of tools are extremely useful for administrators, they are also valuable for threat actors who may use them to deploy malware or gain persistence on networks.
Run binaries as system
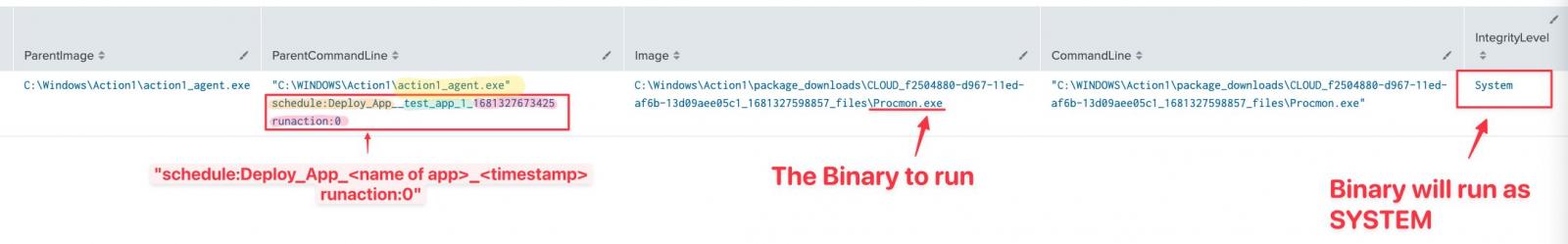
Costasmember of the volunteer analyst group The DFIR Reportnoticed that the Action1 RMM platform was being abused by several malicious actors for reconnaissance activities and to execute code with system privileges on network hosts.
THE researcher says that after installing the Action1 agent, adversaries create a policy to automate the execution of the binaries (e.g. Process Monitor, PowerShell, Command Prompt) needed for the attack.
Tsale points out that aside from remote access capabilities, Action1 is available for free up to 100 endpoints, which is the only restriction of the free version of the product.
Action1 abused in ransomware attacks
BleepingComputer has attempted to learn more about incidents where the Action1 RMM platform is abused and has been told by sources that it has been observed in ransomware attacks by multiple threat actors.
The product has been exploited in the initial stages of at least three recent ransomware attacks using distinct malware strains. However, we were unable to find the specific ransomware deployed during the incidents.
However, we’ve been told that the tactics, techniques, and procedures (TTPs) echo an attack the BlackBerry Incident Response team investigated last summer.
Threat researchers attributed the attack to a group called Monti, which was unknown at the time. Hackers violated the environment after exploiting the Log4Shell Vulnerability.
BlackBerry analysis showed that most of the indicators of compromise (IoCs) in the Monti attack were seen in ransomware incidents attributed to the Conti syndicate. One IoC that stood out was the use of the Action1 RMM agent.
While Conti attacks relied on remote access software, typical choices were the AnyDesk application and the trial access to the Atera RMM – to install agents on the compromised network thus obtaining remote access to all hosts.
There are also cases where brokers initial access sold to organizations through Zoho’s ManageEngine Desktop Central software, a product that allows administrators to manage Windows, Linux and Mac systems on the network.
From a ransomware perspective, legitimate RMMs are versatile enough to meet their needs, provide wide network reach, and ensure continued persistence, as environment security officers typically don’t flag platforms. as a threat.
AI-based filtering
While Action1 RMM is used legitimately worldwide by thousands of administrators, the vendor is aware that the product is being misused by malicious actors in the post-compromise phase of a lateral movement attack.
Mike Walters, vice president of Vulnerability and Threat Research and co-founder of Action1 Corporation, told BleepingComputer that the company last year introduced an artificial intelligence-based system to detect abnormal user behavior and prevent hackers to use the platform for malicious purposes.
“Last year, we deployed a threat actor filtering system that analyzes user activity for suspicious behavior, automatically suspends potentially malicious accounts, and alerts Action1’s dedicated security team to investigate. the problem” – Mike Walters
Action1 is working on including new measures to stop misuse of the platform, the researcher said, adding that the company is “fully open to cooperation with victims and legal authorities” on cases where Action1 has been exploited for cyberattacks.
[ad_2]
Source link