[ad_1]
Chinese state-sponsored hacking group APT41 found abusing Google Command and Control (GC2) red team tool in data theft attacks on Taiwanese media and company Italian job search.
APT 41, also known as HOODOO, is a Chinese state-sponsored hacking group known for targeting a wide range of industries in the United States, Asia, and Europe. Mandiant was hacking group tracking since 2014, claiming that its activities overlap with other well-known Chinese hacking groups, such as BARIUM and Winnti.
In Google’s April 2023 Threat Horizons report, published last Friday, security researchers from its Threat Analysis Group (TAG) revealed that APT41 abused the GC2 red team tool in attacks. .
GC2, also known as Google Command and Control, is an open source project written in Go that was designed for red team activities.
“This program was developed in order to provide command and control that does not require any special configuration (like: custom domain, VPS, CDN, …) during Red Teaming activities,” the draft reads. GitHub repository.
“Additionally, the program will only interact with Google domains (*.google.com) to make detection more difficult.”
The project consists of an agent deployed to compromised devices, which then reconnects to a Google Sheets URL to receive commands to execute.
These commands force deployed agents to download and install additional payloads from Google Drive or exfiltrate stolen data to the cloud storage service.
GC2 abused in attacks
According to Google’s report, TAG disrupted an APT41 phishing attack against a Taiwanese media company that was attempting to distribute the GC2 agent via phishing emails.
“In October 2022, Google’s Threat Analysis Group (TAG) halted a campaign by HOODOO, a Chinese government-backed attacker also known as APT41, which targeted a Taiwanese media organization by sending emails. -phishing emails that contain links to a password-protected file hosted in Drive,” explained the Google Threat Horizons Report.
“The payload was an open source red team tool called ‘Google Command and Control’ (GC2).”
Google says APT41 also used GC2 in attacks against an Italian job search site in July 2022.
Using the agent, Google indicates that the threat actors attempted to deploy additional payloads to the device and exfiltrate data to Google Drive, as shown in the attack workflow shown -below.
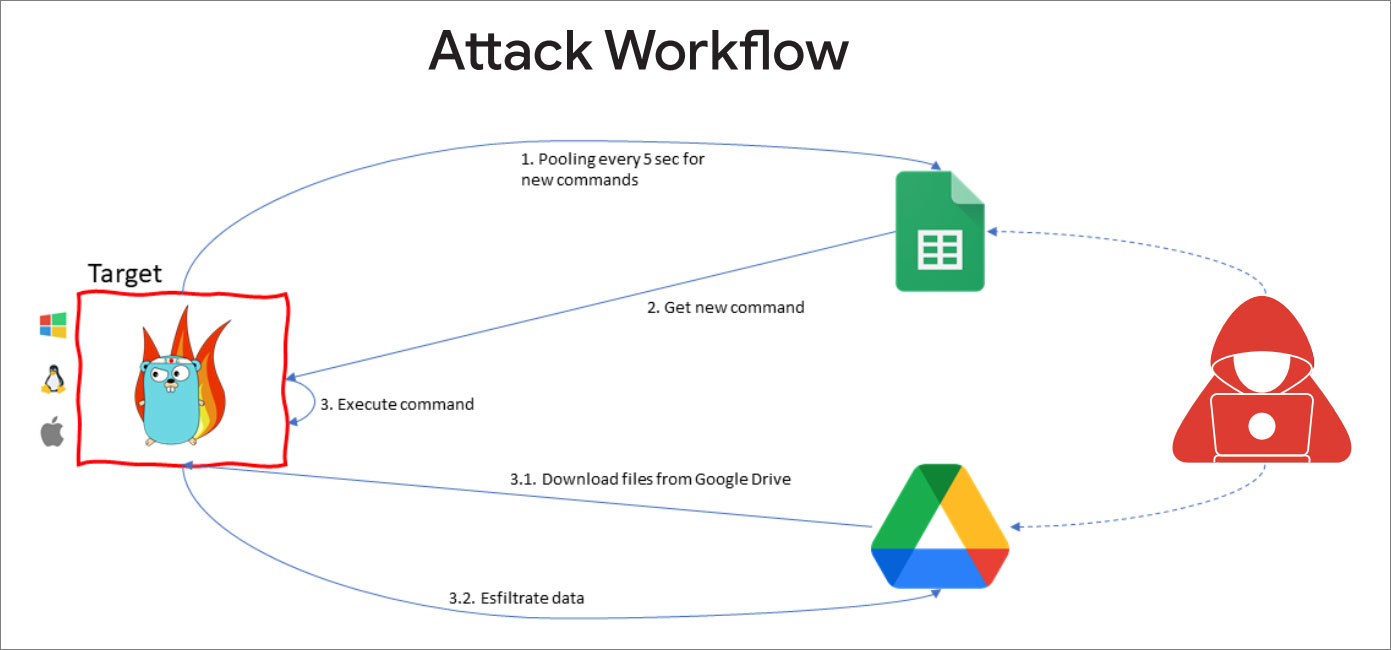
Source: Google
Although it is unknown what malware was distributed in these attacks, APT41 is known to deploy a wide variety of malware to compromised systems.
A Mandiant Report 2019 explains that threat actors use rootkits, bootkits, custom malware, backdoors, point-of-sale malware, and even ransomware in an isolated incident.
Threat actors are also known to deploy Winnti malware and the China Chopper web shell, tools commonly used by Chinese hacking groups, and Cobalt Strike for persistence in compromised networks.
In 2020, the Ministry of Justice charged three Chinese nationals suspected of being part of APT41 for carrying out supply chain attacks [CCleaner, ShadowPad, ShadowHammer]data theft and breaches against countries around the world.
BleepingComputer contacted Google to learn more about the payloads they saw in these attacks, but no response was immediately available.
A shift to legitimate tools
APT41’s use of GC2 is another indicator of a trend for threat actors to turn to legitimate red team tools and RMM platforms as part of their attacks.
While the use of Cobalt Strike in attacks has been prevalent for years, it has also led to significant investment in detecting it in attacks, making it more easily spotted by defenders.
For this reason, threat actors have started turning to other red team tools, such as Brute Honey Badger And Wickto evade detection during their attacks.
More recently, ransomware gangs started abusing the Action1 remote monitoring and management (RMM) tool for persistence on compromised networks and to run commands, scripts and binaries.
Unfortunately, as with any tool that can help red teamers perform drills or administrators manage a network remotely, they can also be abused by threat actors in their own attacks.
[ad_2]
Source link
