[ad_1]

The Google Cloud Threat Intelligence team has open source YARA rules and a VirusTotal collection of Indicators of Compromise (IOCs) to help defenders detect Cobalt Strike components in their networks.
Security teams will also be able to identify versions of Cobalt Strike deployed in their environment through these detection signatures.
“We release to the community a set of Open Source YARA Rules and their integration as VirusTotal Collection to help the community report and identify Cobalt Strike components and their respective versions,” said Greg Sinclair, Security Engineer, Google Cloud Threat Intelligence.
“We decided that detecting the exact version of Cobalt Strike was an important part of determining the legitimacy of its use by non-malicious actors, as some versions have been abused by threat actors.”
This allows for improved detection of malicious activity by targeting non-current versions of Cobalt Strike (potentially leaked and hacked versions) as it makes it easier to differentiate between legitimate deployments and those controlled by threat actors.
As Google explained, hacked and leaked versions of Cobalt Strike are, in most cases, at least one version behind, which has allowed the company to collect hundreds of samples of stagers, models and tags used in the wild to create YARA-based detection rules with a high degree of accuracy.
“Our goal was to make high-fidelity detections to help identify the exact version of particular Cobalt Strike components. Where possible, we created signatures to detect specific versions of the Cobalt Strike component,” Sinclair said. added.
Google also shared a collection of detection signatures for Sliver, a legitimate, open-source adversary emulation framework designed for security testing that has also been adopted by malicious actors as a Alternative to Cobalt Strike.
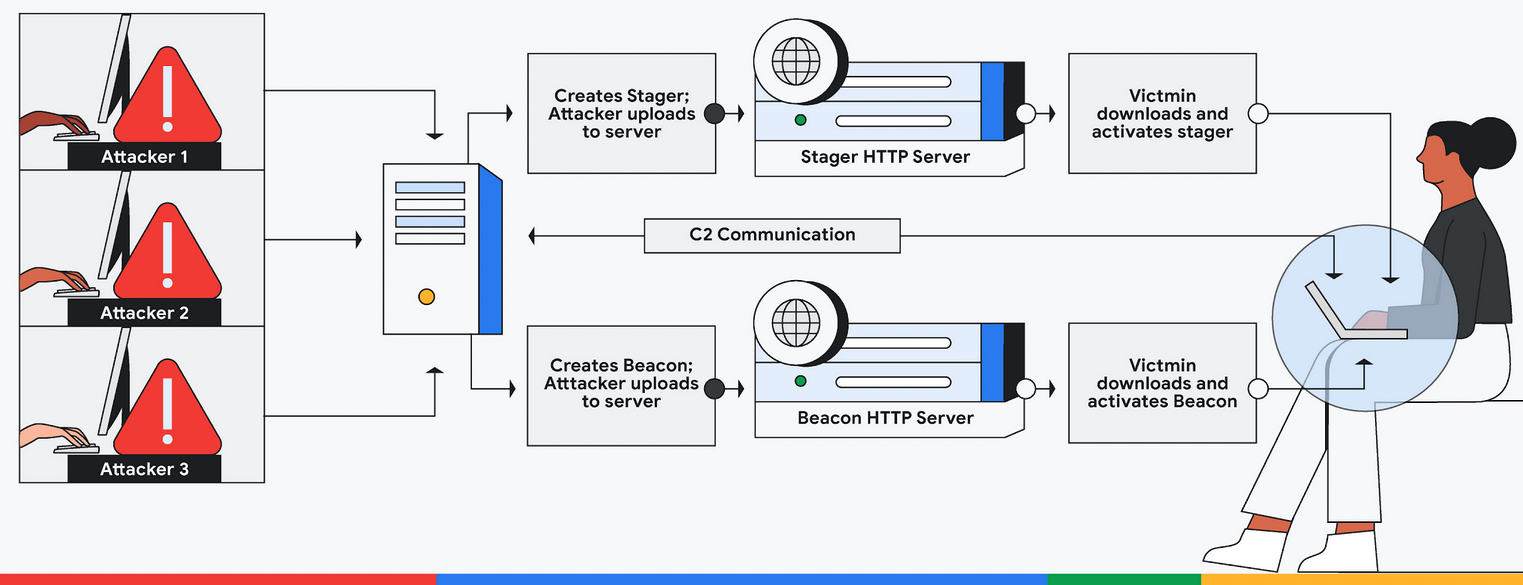
Cobalt Strike (manufactured by Fortra, formerly known as Help Systems) is a legitimate penetration testing tool that has been in development since 2012. It was designed as an attack framework for red teams analyzing security infrastructure. their organization to find vulnerabilities and security gaps.
While the developer attempts to control customers and will only sell licenses for legitimate uses, pirated copies of Cobalt Strike have also been obtained and shared by threat actors over time.
This has led Cobalt Strike to become one of the most commonly used tools in cyberattacks that could lead to data theft and ransomware.
In such attacks, it is used by threat actors for post-exploitation tasks after deploying so-called beacons that provide them with persistent remote access to compromised devices.
Using beacons deployed on victims’ networks, attackers can access compromised servers to harvest sensitive data or deploy other malware payloads.
Researchers from security firm Intezer also revealed that threat actors have also developed and are using (as of August 2021) their own Linux beacon (Vermilion Strike), compatible with Cobalt Strike, to gain persistence and remote command execution on Windows and Linux devices.
[ad_2]
Source link
