[ad_1]

An ongoing Google malvertisement campaign delivers malware installers that leverage KoiVM virtualization technology to evade detection when installing the Formbook data stealer.
KoiVM is a plugin for the ConfuserEx .NET protector that obfuscates a program’s opcodes so that the virtual machine only understands them. Then, once launched, the virtual machine translates the opcodes to their original form so that the application can be executed.
“Virtualization frameworks such as KoiVM obfuscate executables by replacing original code, such as NET Common Intermediate Language (CIL) instructions, with virtualized code that only the virtualization framework understands,” says a new report from SentinelLabs.
“A virtual machine engine executes virtualized code by translating it into the original code at runtime.”
“When used for malicious purposes, virtualization makes malware analysis difficult and also represents an attempt to evade static analysis mechanisms.”
In a Google ad campaign spotted by Sentinel LabsThreat actors push the Formbook information-stealing malware as virtualized .NET loaders called “MalVirt”, which help distribute the final payload without triggering antivirus alerts.
Sentinel Labs comments that while KoiVM virtualization is popular for hacking tools and cracks, it is rarely used in malware distribution.
Instead, the security firm believes the new trend in its use could be one of multiple side effects of Microsoft disabling macros in Office.
Abuse of Google Search Ads
Over the past month, researchers have seen increased abuse Google search ads to distribute various malwareincluding RedLine Stealer, Gozi/Ursnif, Vidar, Rhadamanthys stealer, IcedID, Raccoon Stealer and many more.
In the ongoing campaign seen by SentinelLabs, threat actors are pushing MalVirt loaders in advertisements claiming to be for Blender 3D software.
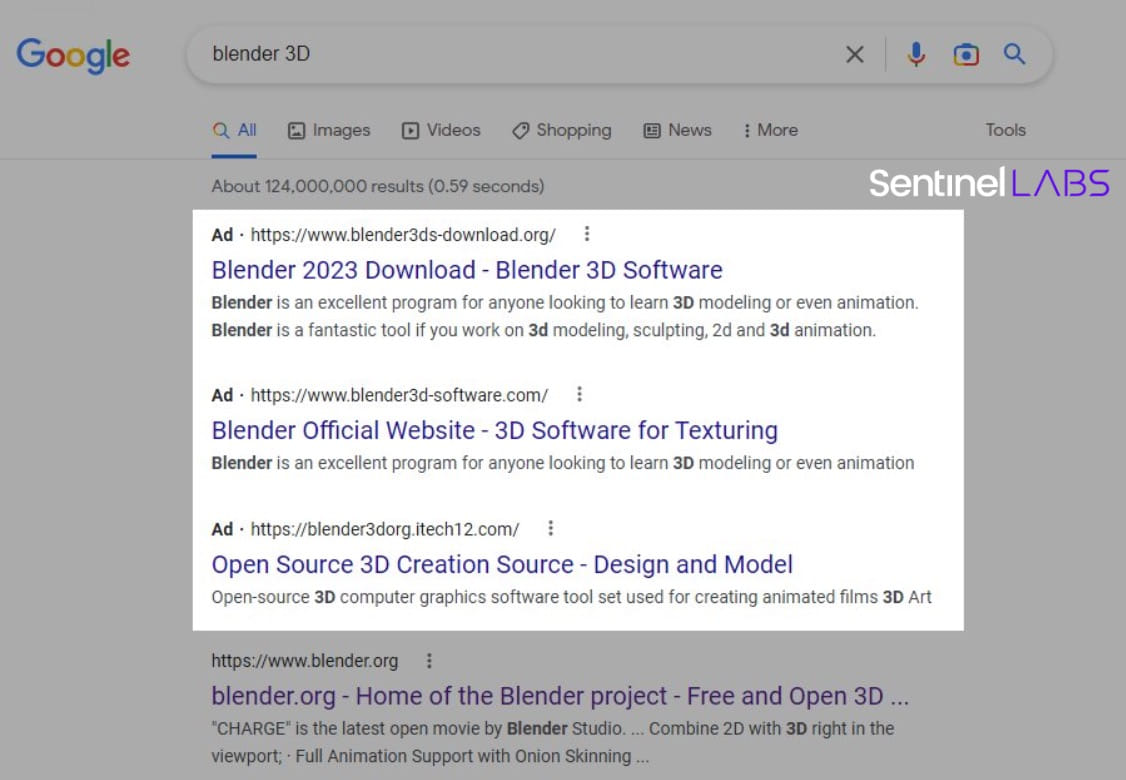
The downloads offered by these bogus sites use invalid digital signatures impersonating Microsoft, Acer, DigiCert, Sectigo, and AVG Technologies USA.
Although these invalid signatures do not cause Windows to show them as signed, MalVirt loaders still contain features to avoid detection.
“For example, some samples fix the AmsiScanBuffer function implemented in amsi.dll to bypass the Anti Malware Scan Interface (AMSI) that detects malicious PowerShell commands,” says researcher A. Milenkoski.
“Additionally, in an attempt to evade static detection mechanisms, some strings (such as amsi.dll and AmsiScanBuffer) are Base-64 encoded and AES encrypted.”
Loaders can also detect if they are running in a virtualized environment by querying specific registry keys, and if they do, execution halts to escape scanning.
MalVirt also uses a signed Microsoft Process Explorer driver loaded at system startup as a “TaskKill”, allowing it to modify running processes to evade detection.
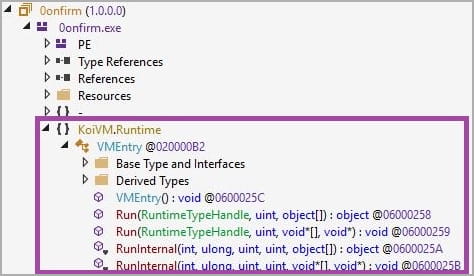
Also to avoid decompilation of virtualized code, loaders also use a modified version of KoiVM which has additional layers of obfuscation, making it even more difficult to decrypt.
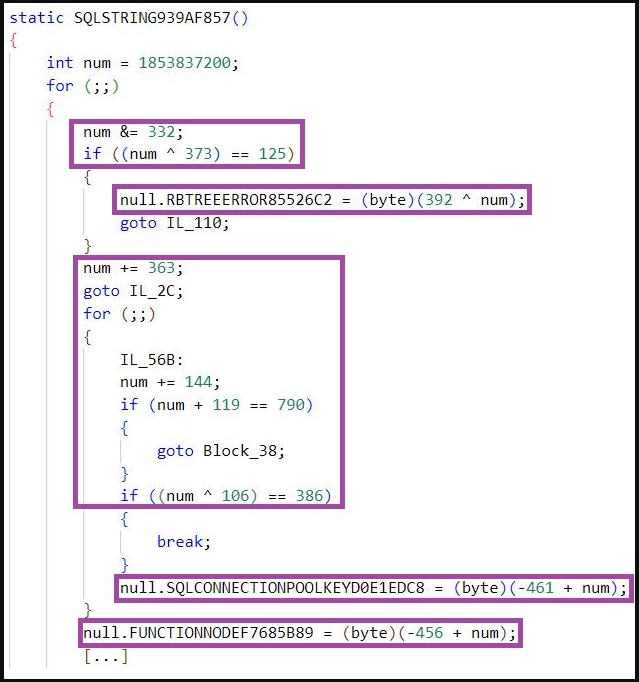
According to SentinelLabs, this custom KoiVM implementation confuses standard devirtualization frameworks such as “OldRod” by obfuscating its routine with arithmetic operations instead of using simple assignments.
Milenkoski says it’s possible to defeat the obfuscation in these MalVirt loaders and restore the original order of KoiVM’s 119 constant variables.
However, the additional obfuscation makes the task difficult, requiring considerable manual work, as existing automated tools cannot help.
Hide infrastructure
In addition to all the detection evasion systems used in the malware loader, a new trick is used by Formbook itself that helps conceal its true C2 (command and control) traffic and IP addresses.
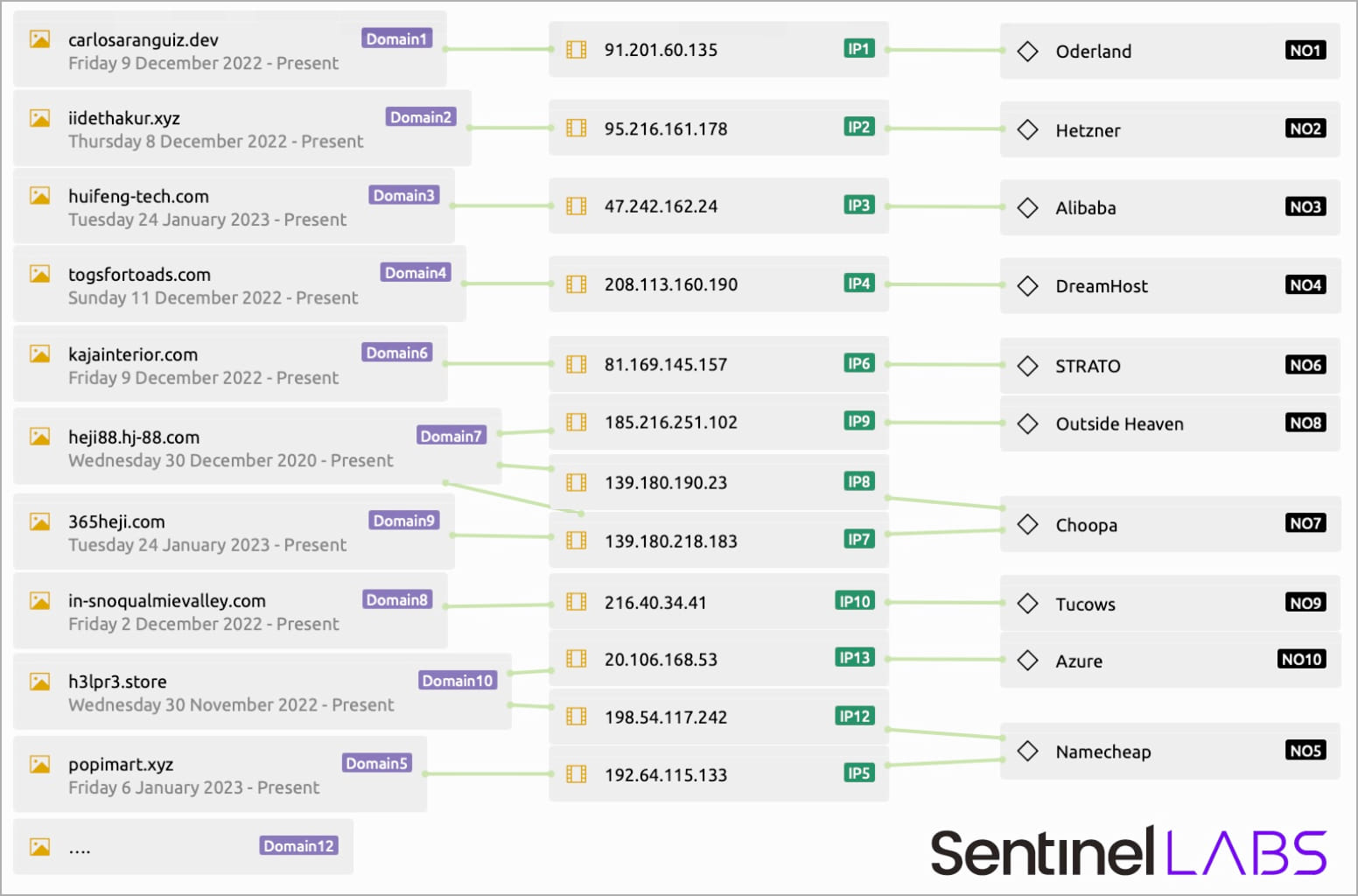
The information-stealing malware mixes its real traffic with various “smokescreen” HTTP requests whose contents are encrypted and encoded so that it does not stand out.
The malware communicates with these IP addresses randomly, selecting them from a hard-coded list with domains hosted by various companies.
SentinelLabs says that in the samples it analyzed, it saw Formbook communicating with 17 domains, only one of which was the actual C2 server, and the rest serving as mere decoys to confuse network traffic monitoring tools.
It’s a new system on a fairly old malware strain, which indicates that its operators want to give it some new features that will allow it to better stay hidden from security tools and analysts.
It remains to be seen whether threat actors have completely switched spam distribution from Formbook to Google search ads, but this is another example that users need to be very careful about the links they click on in search results. research.
[ad_2]
Source link
