[ad_1]

GitHub will begin requiring active developers to enable two-factor authentication (2FA) on their accounts starting next week, March 13.
When extended to the entire enterprise user base, the 2FA registration requirement will help secure the accounts of over 100 million users.
The gradual rollout will begin next week with GitHub reaching out to smaller groups of admins and developers via email and will ramp up as the end of the year approaches to ensure integration is seamless. and that users have time to resolve any issues.
“GitHub has designed a deployment process intended to both minimize unplanned downtime and loss of productivity for users and prevent account lockouts,” said Hirsch Singhal, Staff Product Manager, and Laura Paine, Director product marketing.
“Groups of users will be invited to enable 2FA over time, with each group being selected based on the actions they have taken or the code they have contributed.”
If your account is selected for registration, you will receive an email and see a banner on GitHub.com asking you to register for the two-factor authentication (2FA) program.
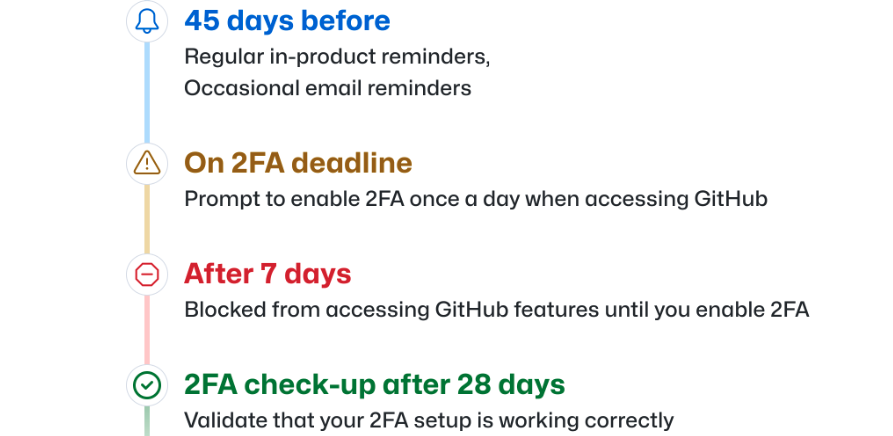
Afterwards, you will have 45 days to set up 2FA on your account, during which time you can continue to use your GitHub account as usual, except for occasional reminders.
GitHub will keep you updated on your activation deadline, and once it has passed you will be prompted to enable 2FA the first time you access GitHub.com and you will be locked out of certain features until 2FA is enabled.
This follows two previous announcements of Can And December that all developers contributing code to the platform will be required to enable 2FA by the end of 2023.
GitHub provides step-by-step instructions on 2FA setup on your behalf and collection of accounts when losing 2FA credentials.
Developers can use one or more 2FA options, including physical security keys, virtual security keys built into mobile devices such as smartphones and laptops, one-time password authenticator apps (TOTP ) or the GitHub Mobile app (after setting up TOTP or SMS 2FA).
Although SMS 2FA is also an option (In some countries), GitHub urges users to switch to security keys or TOTP apps, as hackers can bypass SMS 2FA or steal SMS 2FA authentication tokens to hijack developer accounts.
Securing the software supply chain
Enabling 2FA on GitHub accounts increases resilience against account takeover by blocking attempts to use reused passwords or stolen credentials in hacking attacks.
This is the company’s latest move to secure the software supply chain by moving away from basic password-based authentication.
Previously, the code hosting platform implemented device verification by email And deleted account passwords for authenticating Git operations.
Additionally, GitHub password authentication disabled via REST API back in November 2020 and introduced FIDO2 security key support to secure Git SSH operations in May 2021.
Over the years, GitHub has improved its account security measures by integrating two-factor authentication, connection alerts, block the use of compromised passwordsand providing WebAuthn support.
[ad_2]
Source link
