[ad_1]

GitHub rotated its private SSH key to GitHub.com after the secret was accidentally posted to a public GitHub repository.
The software development and version control department says the private RSA key was only exposed “briefly” but that it took action “too cautiously”.
Unclear exposure window
In a brief blog post published today, GitHub acknowledged discovering this week that the RSA SSH private key for GitHub.com had been ephemerally exposed in a public GitHub repository.
“We immediately acted to contain the exposure and began investigating to understand the root cause and impact,” writing Mike Hanley, GitHub’s Chief Security Officer and Senior Vice President of Engineering.
“We have now completed the key replacement, and users will see the change propagate over the next thirty minutes. Some users may have noticed that the new key was briefly present from 02:30 UTC during preparations for this change.”
from GitHub.com last public key fingerprint are shown below. These can be used to validate that your SSH connection to GitHub’s servers is secure.
As some may notice, only the GitHub.com RSA SSH key was impacted and replaced. No modification is required for ECDSA or Ed25519 users.
SHA256:uNiVztksCsDhcc0u9e8BujQXVUpKZIDTMczCvj3tD2s (RSA)
SHA256:br9IjFspm1vxR3iA35FWE+4VTyz1hYVLIE2t1/CeyWQ (DSA – obsolete)
SHA256:p2QAMXNIC1TJYWeIOttrVc98/R1BUFWu3/LiyKgUfQM (ECDSA)
SHA256:+DiY3wvvV6TuJJhbpZisF/zLDA0zPMSvHdkr4UvCOqU (Ed25519)
“Please note that this issue is not the result of any compromise of GitHub systems or customer information,” GitHub says.
“Instead, the exposure was the result of what we believe was an inadvertent release of private information.”
The blog post, however, is unresponsive When exactly was the key exposed and for how long, which makes the exposure timeline a bit murky. These timestamps can usually be verified from security logs, if available, and Git commit history.
GitHub further states that it has “no reason to believe” that the exposed key was misused and rotated the key “out of an abundance of caution”.
But, rotating a private key once it has been leaked, however “briefly” it may be, is in any case a necessary step to protect users from adversaries who could potentially impersonate your server or spy user login.
The exposed RSA key in question does not provide access to GitHub infrastructure or customer data, Hanley said.
“This change only affects Git operations over SSH using RSA. Web traffic to GitHub.com and HTTPS Git operations are unaffected.”
Double check that fingerprint
Although GitHub has changed the private SSH keys, several documents and software projects, including those from GitHubcontinue to use the SSH fingerprint of its now revoked key:
SHA256:nThbg6kXUpJWGl7E1IGOCspRomTxdCARLviKw6E5SY8
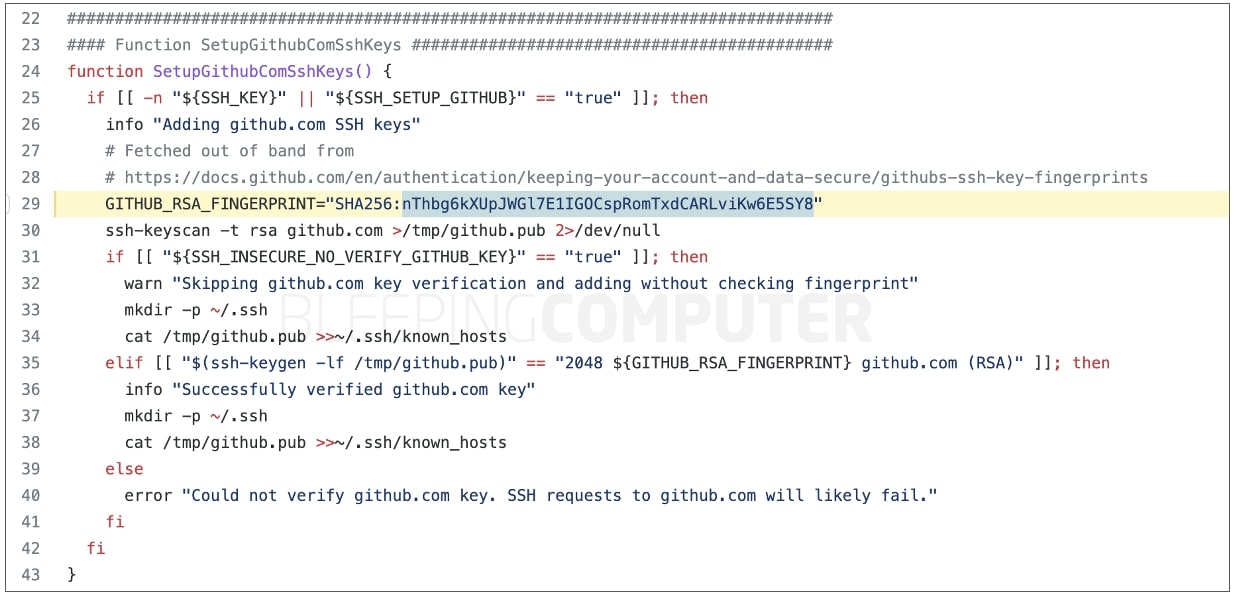
Thus, users need to update their ~/.ssh/known_hosts file with GitHub’s new key fingerprint, otherwise they might see security warnings when making SSH connections. When receiving such warnings, users should ensure that the fingerprint displayed on their screen matches that of the latest key from GitHub.com.
As of last year, GitHub’s updated SSH host keys are also posted on its API metadata endpoint.
[ad_2]
Source link
