[ad_1]

Former Conti ransomware members have teamed up with FIN7 threat actors to distribute a new malware family named “Domino” in attacks on corporate networks.
Domino is a relatively new malware family consisting of two components, a backdoor named “Domino Backdoor”, which in turn drops a “Domino Loader” which injects an information-stealing malware DLL into the memory of another process.
IBM security intelligence researchers have been tracking former Conti and TrickBot members using the new malware in attacks since February 2023.
However, a new IBM report published on Friday links the actual development of the Domino malware to the FIN7 hacking group – a team of cybercriminals linked to a variety of malware, and BlackBasta and DarkSide ransomware operations.
Domino Malware Attacks
Since fall 2022, IBM researchers have been tracking attacks using a malware loader named “Dave Loader” which is linked to former members of Conti ransomware and TrickBot.
This loader was seen deploying Cobalt Strike beacons that use a ‘206546002’ watermark, seen in attacks by former Conti members in the Royal And Play ransomware ops.
IBM says Dave Loader was also seen deploying Emotet, which was used almost exclusively by the Conti ransomware operation in June 2022then later by the BlackBasta and Quantum ransomware gangs.
However, more recently, IBM said it saw Dave Loader install the new Domino malware family.
Most often, Dave Loader dropped “Domino Backdoor”, which then installed “Domino Loader”.
Domino Backdoor is a 64-bit DLL that enumerates system information, such as running processes, usernames, computer names, and returns them to the attacker’s command and control server. The backdoor also receives commands to execute or other payloads to install.
The backdoor was seen downloading an additional loader, Domino Loader, which installs a built-in .NET information stealer called “Nemesis Project”. He can also plant a Cobalt Strike beacon, for greater persistence.
“The Domino backdoor is designed to contact a different C2 address for domain-joined systems, suggesting that a more capable backdoor, such as Cobalt Strike, will download to higher value targets instead of Project Nemesis,” explain IBM researchers Charlotte Hammond and Ole. Villadsen.
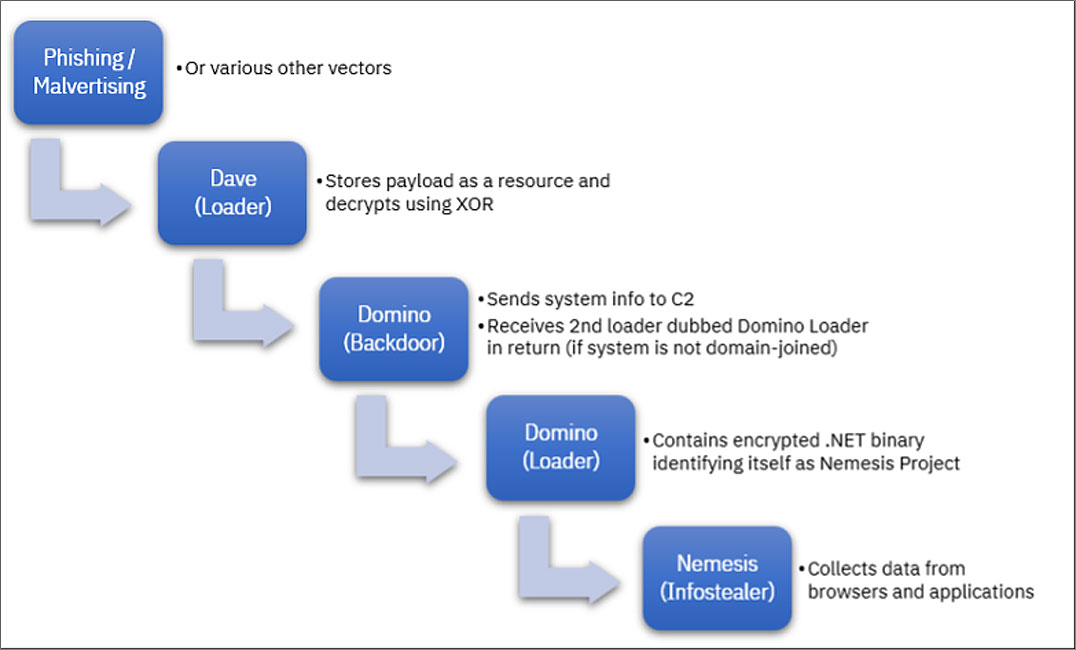
Source: IBM
Project Nemesis is standard information-stealing malware that can harvest credentials stored in browsers and apps, cryptocurrency wallets, and browser history.
Former Conti members team up with FIN7
Threat authors, especially those using ransomware, typically team up with other threat groups to distribute malware and for initial access to corporate networks.
For example, TrickBot, Emotet, BazarBackdoor and QBot (QakBot) have a long history of provide initial access to ransomware operationssuch as REvil, Maze, Egregor, BlackBasta, Ryuk and Conti.
Over time, the lines between malware developers and ransomware gangs have become blurred, making it difficult to distinguish between the two operations.
With the formation of the cybercrime syndicate Conti, those lines have blurred even more as the ransomware operation took control of both TrickBot and the development of BazarBackdoor for their own operations.
Moreover, after Content closedTHE ransomware operation divided into smaller cellswith members moving all over the ransomware space, including RoyalPlay, Quantum/Zeon/DagonBlackBasta, LockBit, and more.
IBM assigned the Domino malware family to FIN7 due to a large code overlap with Lizar (aka Tirion and DiceLoader), a post-exploitation toolkit associated with FIN7.
Additionally, IBM discovered that a loader named “NewWorldOrder”, normally used in FIN7’s Carbanak attacks, was recently used to push Domino malware.
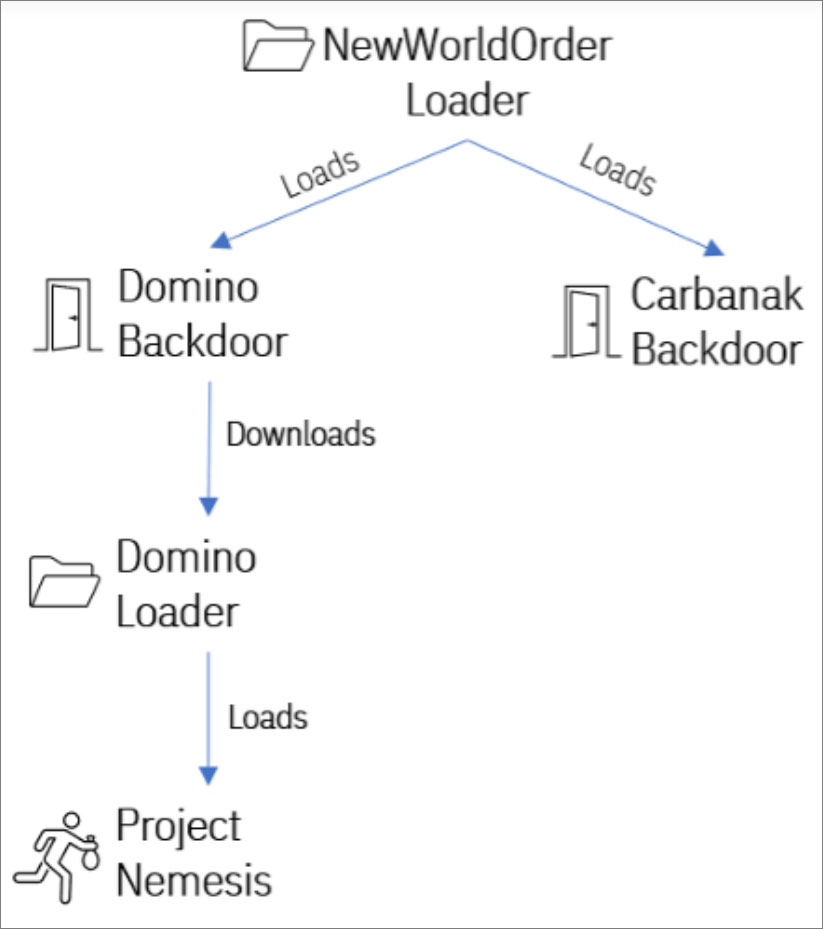
Source: IBM
So in a confusing joint venture we have Dave Loader (TrickBot/Conti) pushing the Domino malware (FIN7), which in turn deploys Project Nemesis or Cobalt Strike beacons believed to be associated with ex-member ransomware activity by Conti.
This means that defenders have to deal with a confusing web of malicious actors, all with malware allowing remote access to networks.
[ad_2]
Source link
