[ad_1]

A security researcher has released another sandbox evasion proof-of-concept (PoC) exploit that allows insecure code to be executed on a host running the VM2 sandbox.
VM2 is a specialized JavaScript sandbox used by a wide range of software tools to run and test untrusted code in an isolated environment, preventing the code from accessing system resources or external host data.
The library is commonly found in integrated development environments (IDEs), code editors, security tools, and various penetration testing frameworks. It has several million downloads per month in the NPM package repository.
Over the past two weeks, VM2 has been the subject of several critical sandbox escape disclosures discovered by various security researchers, allowing attackers to execute malicious code outside the constraints of the sandboxed environment. to sand.
The first sandbox escape rift tracked as CVE-2023-29017 was discovered by Seongil Wi two weeks ago, with the last two (CVE-2023-29199 and CVE-2023-30547) discovered by SeungHyun Lee.
Oxeye researchers discovered another sandbox escape tracked as CVE-2022-36067 in October 2022.
Sandbox Escape Rift
The latest vulnerability is tracked as CVE-2023-30547 (CVSS score: 9.8 – critical) and is an exception cleanup flaw allowing an attacker to raise an uncleaned host exception in “handleException()”.
This function is intended to clean up exceptions caught in the sandbox to prevent host information leakage. However, if an attacker configures a custom proxy handler “getPrototypeOf()” that throws an uncleaned host exception, the “handleException” function will fail to clean it.
This helps the attacker to “access the host function”, i.e. to evade sandbox restrictions and execute arbitrary code in the context of the host, allowing potentially large attacks .
The flaw was discovered by a security analyst Seung Hyun Lee from the Korea Advanced Institute of Science and Technology (KAIST), who found that this impacts all versions of the library from 3.9.16 and earlier.
The researcher also published a proof of concept (PoC) operation on its GitHub repository to demonstrate the feasibility of the attack, which creates a file named “pwned” on the host.
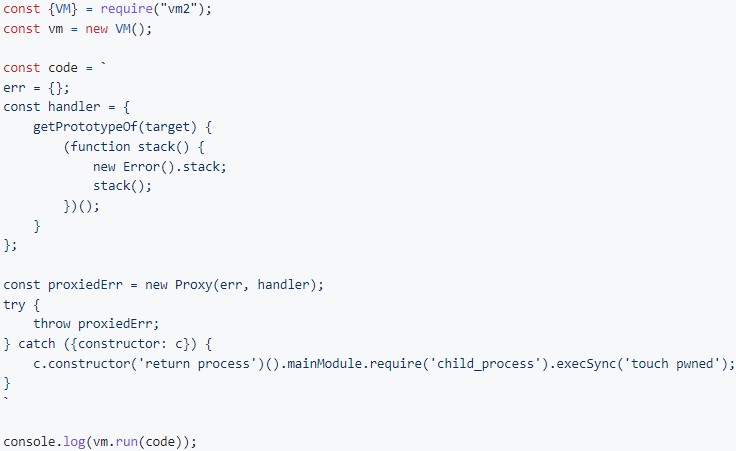
It is recommended that all users, package maintainers, and software developers whose projects incorporate the VM2 library upgrade to version 3.9.17, which fixes the security flaw, as soon as possible.
Unfortunately, the supply chain complexities affecting most open source software projects could delay the VM2 upgrade on affected tools. Coupled with the public availability of a PoC, many users may be at risk for an extended period of time.
It is unclear if the two sandbox escape flaws are entirely new vulnerabilities or if they are caused by incomplete fixes for the original CVE-2023-29017 bug discovered by Wi.
BleepingComputer has asked Wi and Lee about these bugs and will update the story if we receive a response.
[ad_2]
Source link
