[ad_1]

A recently spotted malvertising campaign tricked users with an in-browser Windows Update simulation to deliver Aurora information-stealing malware.
Written in Golang, Dawn has been available on various hacker forums for more than a year, promoted as an information stealer with extensive capabilities and weak antivirus detection.
According to researchers from Malwarebytesthe malvertising operation relies on popunder advertisements on adult content websites with high traffic adult content and redirects potential victims to a malware distribution location.
Not a Windows Update
Popunder ads are cheap “pop-up” ads that launch behind the active browser window, remaining hidden from the user until they close or move the main browser window.
In December last year, Google reported that popunders were being used in a ad fraud campaign which amassed hundreds of thousands of visitors and tens of millions of fraudulent ad impressions.
The most recent spotted by Malwarebytes has a much lower impact, with nearly 30,000 users redirected and almost 600 downloading and installing the data-stealing malware on their systems.
However, the threat actor came up with an imaginative idea where the popunder renders a full-screen browser window that simulates a Windows system update screen.
The researchers tracked more than a dozen domains used in the campaigns, many of which appeared to impersonate adult websites, which simulated the fake Windows Update:
- activesd[.]ru
- chistauyavoda[.]ru
- xxxxxxxxxxxxxxx[.]ru
- active hard drive[.]ru
- oled8kultra[.]ru
- xhamster-18[.]ru
- oled8kultra[.]to place
- activesd6[.]ru
- activedebian[.]ru
- shluhapizdec[.]ru
- 04042023[.]ru
- clickaineasdfer[.]ru
- moskovpizda[.]ru
- pocketlvpizdy[.]ru
- evatds[.]ru
- click7adilla[.]ru
- grhfgetraeg6yrt[.]to place
All served to download a file named “ChromeUpdate.exe”, revealing the full-screen browser screen deception; however, some users were tricked into deploying the malicious executable anyway.
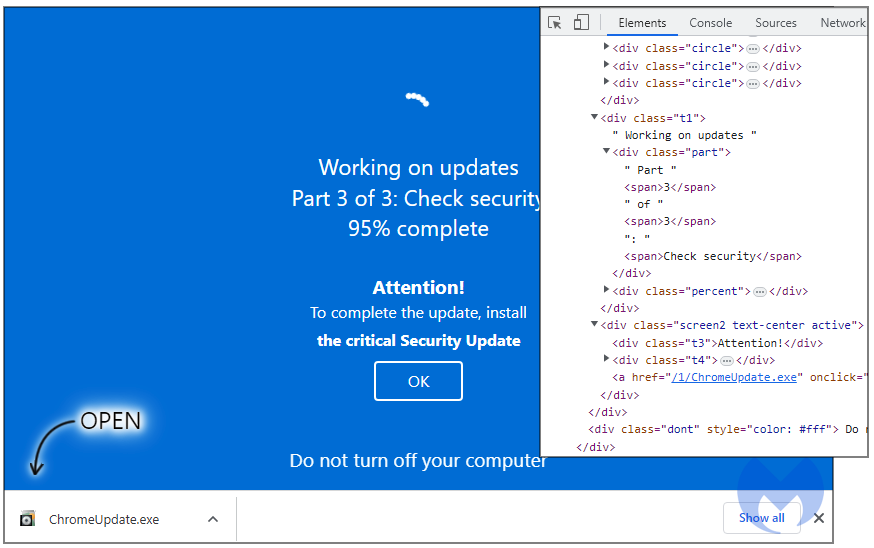
New malware loader
The purported Chrome Updater is a so-called “fully undetectable” (FUD) malware loader called “Invalid Printer” which appears to be used exclusively by this particular threat actor.
Malwarebytes says that when its analysts discovered an “invalid printer”, no antivirus engine on Virus Total flagged it as malicious. Detection began to pick up a few weeks later, however, following the publication of a relevant report Morphisec report.
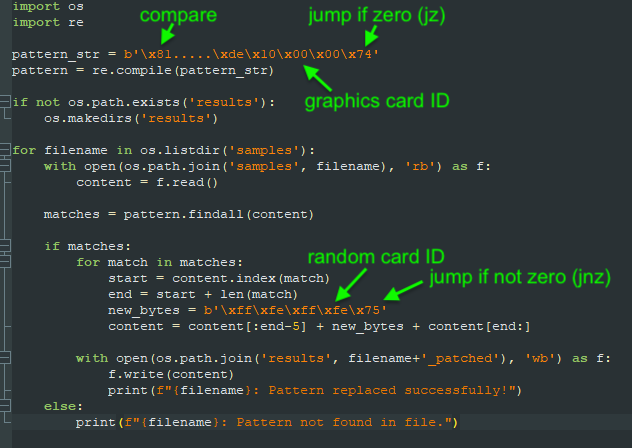
The invalid printer first checks the host’s graphics card to determine if it is running in a virtual machine or in a sandbox environment. If not, it unboxes and launches a copy of the Aurora Infostealer, the researchers found.
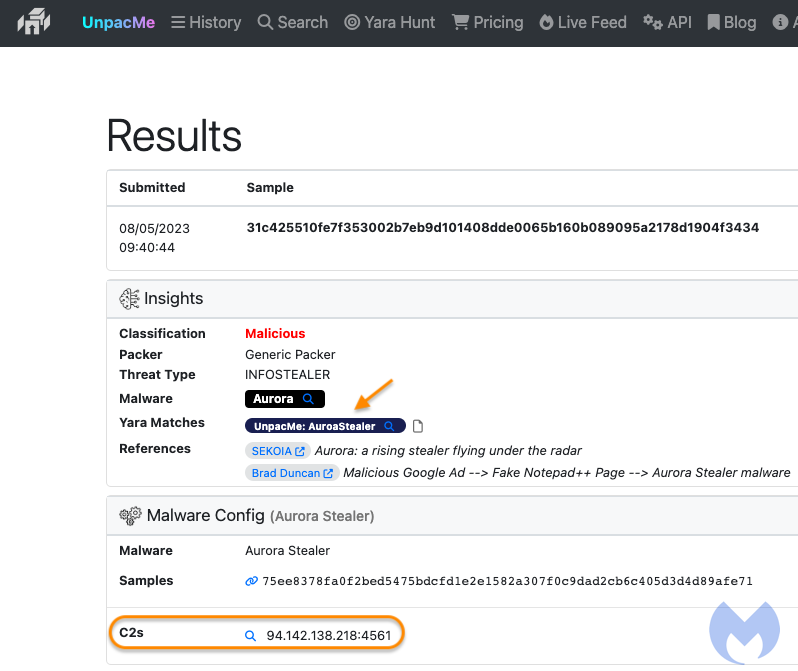
Malwarebytes comments that the threat actor behind this campaign seems to be particularly interested in creating hard-to-detect tools, and they are constantly uploading new samples to Virus Total to check how they perform against detection engines.
Jerome Segura, director of threat intelligence at Malwarebytes, noted that every time a new sample was first submitted to Virus Total, it came from a user in Turkey and that “in many cases, the name of the file seemed to come from the compiler (i.e. build1_enc_s.exe).”
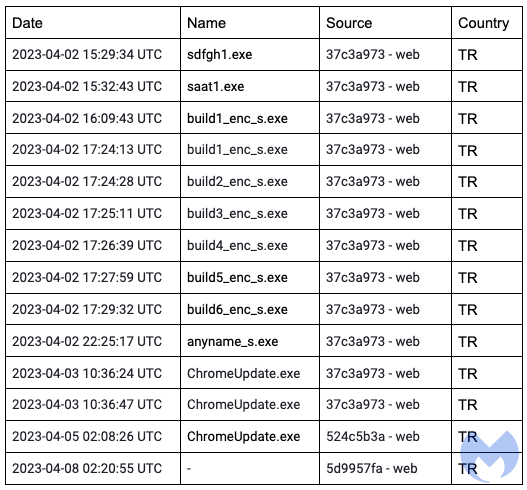
Further investigation revealed that the threat actor is also using a Amadey panel, potentially indicating the use of the well-documented malware recognition and loading tool, and also runs tech support scams targeting Ukrainians.
Malwarebytes provides technical analysis of malware installation and behavior, as well as a set of indicators of compromise that companies and security vendors can use to defend their users.
[ad_2]
Source link
