[ad_1]

A proof-of-concept exploit code is now available for a Remote Code Execution (RCE) vulnerability in several Zoho ManageEngine products.
This pre-authentication RCE flaw is identified as CVE-2022-47966 and stems from the use of an outdated and vulnerable version of the Apache Santuario library.
Unauthenticated attackers can execute arbitrary code on Acronis instances after a successful exploit if SAML-based single sign-on (SSO) is or has been enabled at least once before the attack.
The vulnerable software includes almost all ManageEngine products, but it has already been patched in several waves starting October 27, 2022, updating the third-party dependency to a secure version.
| Access Manager More | Active Directory 360 | Operating System Deployer |
| ADAudit Plus | AD Manager Plus | Password Manager Pro |
| ADSelfservice Plus | Analytics More | MAP 360 |
| App Control More | Asset Explorer | Patch Manager More |
| Browser Security More | Device Control More | Remote Monitoring and Management (RMM) |
| Endpoint Central | Endpoint Central MSP | Remote access more |
| Endpoint DLP | Key Manager More | Service Desk Plus |
| ServiceDesk Plus MSP | Support Center Plus | Vulnerability Manager More |
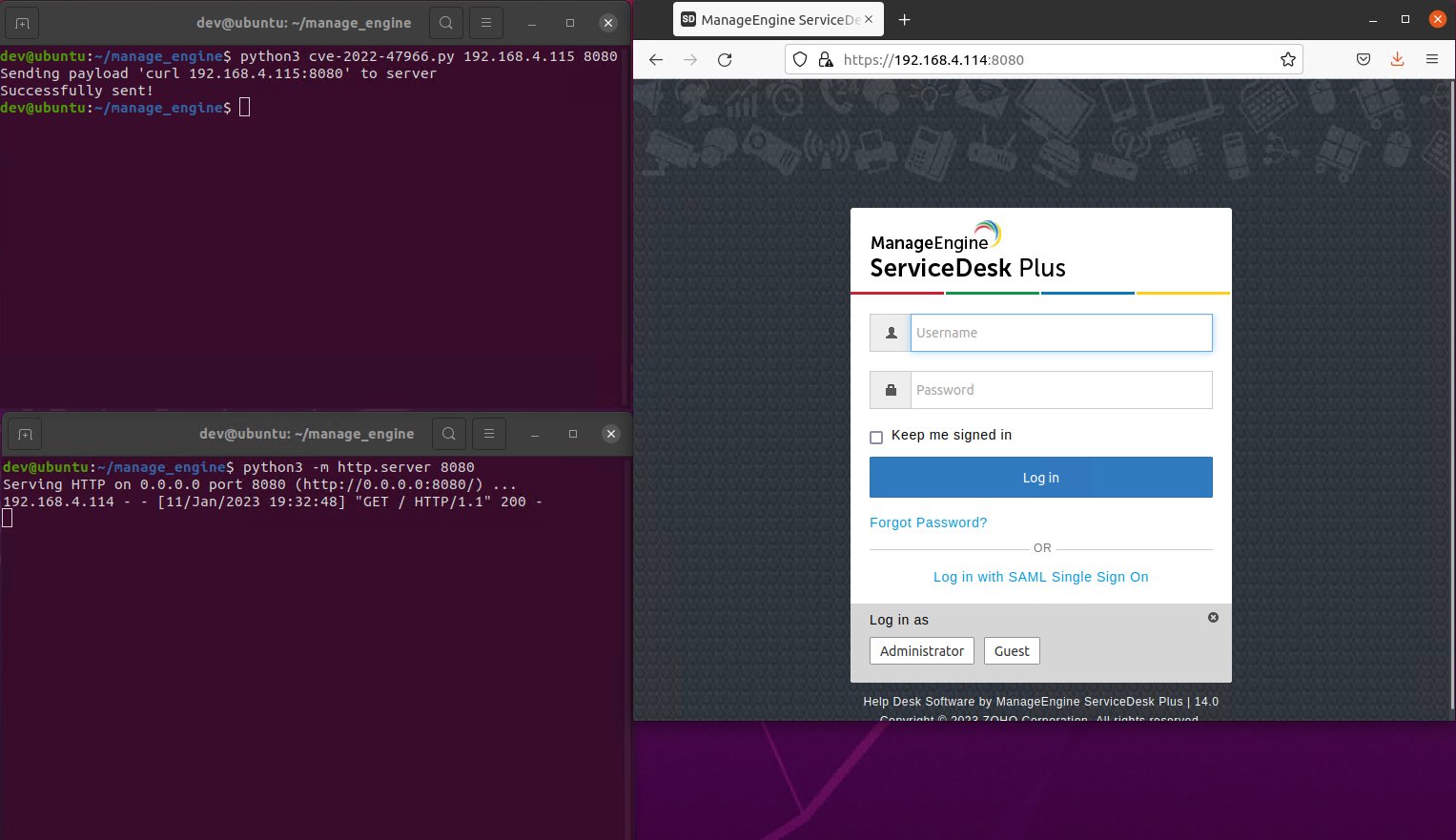
Horizon3 security researchers have published a proof-of-concept (PoC) exploit and technical analysis for the vulnerability earlier today, following a Thursday warning that a PoC CVE-2022-47966 will be available later this week.
“The vulnerability allows an attacker to achieve remote code execution by issuing an HTTP POST request containing a malicious SAML response,” the researchers said.
“This POC abuses the pre-authentication remote code execution vulnerability to execute a command with Java’s Runtime.exec method,” they added.
The PoC exploit has been tested on ServiceDesk Plus and Endpoint Central, and Horizon3 “expects this POC to work unmodified on many ManageEngine products that share part of their code base with ServiceDesk Plus or EndpointCentral.”
Horizon3 previously released exploit code for other critical security flaws in several different products, including:
- CVE-2022-28219a critical flaw in Zoho ManageEngine ADAudit Plus that allows attackers to compromise Active Directory accounts,
- CVE-2022-1388a critical vulnerability allowing remote code execution in F5 BIG-IP network equipment,
- and CVE-2022-22972a critical authentication bypass bug in several VMware products that may allow hackers to gain administrator privileges.
Incoming “spray and pray” attacks
Last week, Horizon3 researchers also warned of a potential wave of attacks following the release of the PoC exploit, as “the vulnerability is easy to exploit and a good candidate for attackers to “spray and pray “on the Internet”.
They found thousands of unpatched ServiceDesk Plus and Endpoint Central servers exposed online through Shodan, with around 10% of all detected devices exposed to CVE-2022-47966 attacks because they have SAML enabled.
Although there are no reports of attacks exploiting this vulnerability and no attempt to exploit it in the wildthreat actors will likely move quickly to develop custom RCE exploits based on Horizon3’s PoC code.
In recent years, financially motivated and state-backed threat groups have heavily targeted Zoho ManageEngine servers.
For example, threat actors have also sold access to the networks of hacked organizations on hacking forums after compromising Desktop Central instances exposed to the internet in July 2020.
Between August and October 2021, they were the target of a campaign orchestrated by nation-state hackers with similar tactics, techniques, and procedures (TTPs) as the Chinese hacking group APT27.
Following these and other attacks targeting ManageEngine, CISA and the FBI issued two joint advisories [1, 2] to warn state-backed attackers exploiting ManageEngine bugs to hijack critical infrastructure organizations.
[ad_2]
Source link
