[ad_1]

Microsoft is introducing a new Exchange Online security feature that will automatically start throttling and eventually block all emails sent from “persistently vulnerable Exchange servers” 90 days after administrators receive a ping to secure them.
As Redmond explains, these are Exchange servers in on-premises or hybrid environments that are running end-of-life software or haven’t been patched for known security bugs.
“Any Exchange server that has reached end of life (for example, Exchange 2007, Exchange 2010, and soon Exchange 2013) or remains unpatched for known vulnerabilities,” the Exchange team explained.
“For example, Exchange 2016 and Exchange 2019 servers that are significantly behind on security updates are considered consistently vulnerable.”
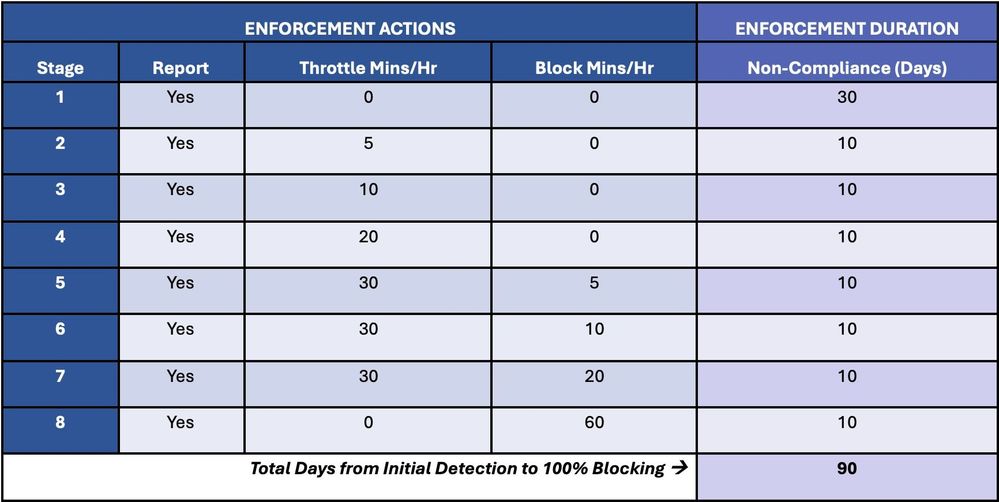
Microsoft says this new Exchange Online “transport-based application system” has three distinct functions: reporting, throttling, and blocking.
The primary goal of the new system is to help Exchange administrators identify unpatched or unsupported on-premises Exchange servers, allowing them to upgrade or patch them before they become security risks. .
However, it will also be able to throttle and possibly block emails from Exchange servers that have not been patched before reaching Exchange Online mailboxes.
This new enforcement system will only affect servers running Exchange Server 2007 using on-premises connectors to send mail to allow fine-tuning before rolling out to all versions of Exchange regardless how they connect to Exchange Online, after setting the
Redmond says it is following a phased approach designed to gradually increase throttling and introduce email blocking until all emails sent from vulnerable servers are rejected.
These enforcement actions are designed to slowly escalate until vulnerable Exchange servers are fixed by decommissioning (for end-of-life versions) or patched (in the case of versions still in support).
“Our goal is to help customers secure their environment wherever they choose to run Exchange,” said the exchange team.
“The enforcement system is designed to alert administrators to security risks in their environment and to protect Exchange Online recipients from potentially malicious messages sent from persistently vulnerable Exchange servers.”
For some administrators, ensuring that emails sent from vulnerable servers in their environment to Exchange Online mailboxes will not be automatically blocked will likely be another “incentive” in addition to their ongoing efforts to protect end users against potential attacks.
This announcement follows a January call to action when Microsoft urged customers to keep their on-premises Exchange servers up to date by applying the latest supported Cumulative Update (CU) so they are always ready for incoming emergency security updates.
Microsoft has also asked administrators to apply the latest patches to Exchange servers as soon as possible after releasing emergency out-of-band security updates to address ProxyLogon vulnerabilities exploited in attacks. month before official patches have been released.
More recently, Microsoft patched another set of Exchange RCE bugs known as ProxyNotShell, two months after the exploit was detected for the first time in nature.
A Shodan Research still shows a massive number of Exchange servers exposed to the internet, with thousands of them waiting to be protected from attacks targeting them with the ProxyLogon and ProxyShell exploits, two of most exploited vulnerabilities in 2021.
[ad_2]
Source link
