[ad_1]

Companies rely on their end users, but those same users often don’t follow security best practices. Without the right password security policies, a single end-user password mistake can be a costly breach of your organization’s defenses.
End users want to get their jobs done quickly and efficiently. Password prompts can be considered a nuisance and users may not know the best practices to follow or understand the importance of following them.
Sharing, reusing, and weak passwords can put your organization at risk, so having the right policies in place for security is essential!
Password risk
Passwords have been a staple of computers for as long as many users can remember and remain essential for keeping systems secure. Although there are many ways to create passwords, not all are equally effective. It’s important to consider the different ways a password-protected system can fail.
The most obvious problem is easy-to-guess passwords, such as “password1”. An attacker could easily crack this password after only a few attempts. However, passwords can be insecure in other ways, such as reusing the same password across multiple sites, sharing a password with colleagues, or even memorizing a password on a public computer.
Easily hacked characters and patterns
Password cracking technology is constantly evolving and getting faster. There are even specialized password cracking tools readily available. From phishing to social engineering attacks, brute force attacks, dictionary attacks, and malware, all are forms of password cracking.
Users often use a base word when creating their password. Basic words such as password, welcome, and admin are widely used and are among the top ten. When asked to change their password or create a new one, they often substitute numbers for certain letters of a word or add special characters (for example, “!” or “#”) at the beginning and at the end of the password.
However, password hackers have incorporated these patterns into their tools, making them less effective.
Password sharing and password reuse
Many users use the same password across multiple sites to make it easier to remember credentials. For example, if a user is scammed on a social media site like Facebook, the attacker could try the same password on the work site.
Altogether, shared passwords and password reuse offer multiple ways for attackers to target a business through its end users.
Proper Password Management Procedures
Password theft and misuse can take many forms. A typical example is when employees use their personal devices to access corporate resources and communications. A user’s personal device may not have the proper security pins, making it vulnerable.
Additionally, if an employee has their corporate email on their phone or accesses corporate resources and their device is stolen, without proper security and access controls, this creates a huge security risk.
Unfortunately, mobile security is often an afterthought for many organizations.
Best practices for securing passwords
With all the ways passwords can be insecure, what are the best practices for creating and managing them, and how can users be encouraged to follow them? Over time, as organizations have become more knowledgeable about password policy, the recommended steps have evolved, especially in recent years.
- Creating Secure Passwords – Creating a secure password is more than just avoiding easily cracked characters and passwords. According to NIST recommendationspasswords must be at least eight characters long (if not, more) and do not contain sequential characters (for example, “1234”). Additionally, complexity requirements should be reduced to enable users to create memorable yet secure passwords.
- Avoid Sharing and Reusing Passwords – A unique password for every site and app, with no sharing, ensures that a password stolen elsewhere won’t compromise an organization. Requiring each user to have their own account and not allowing shared passwords increases accountability and logging capabilities while improving security.
- Verify that passwords are not on breached password lists – Before accepting a password creation or change, systems should review the most recent breached password lists and alert users if the password is deemed insecure.
- Use Multi-Factor Authentication (MFA) – Improve security from any password-protected account with multi-factor authentication (MFA). A second factor will limit an attacker’s ability to access the account in the event of a hacked password.
The recent Weak Password Report discovered that 83% of compromised passwords meet the password length and complexity requirements of password regulatory standards. This indicates that even when following best practices, strong password policy enforcement must occur for continued password security.
Enforce a strong password policy to eliminate vulnerabilities
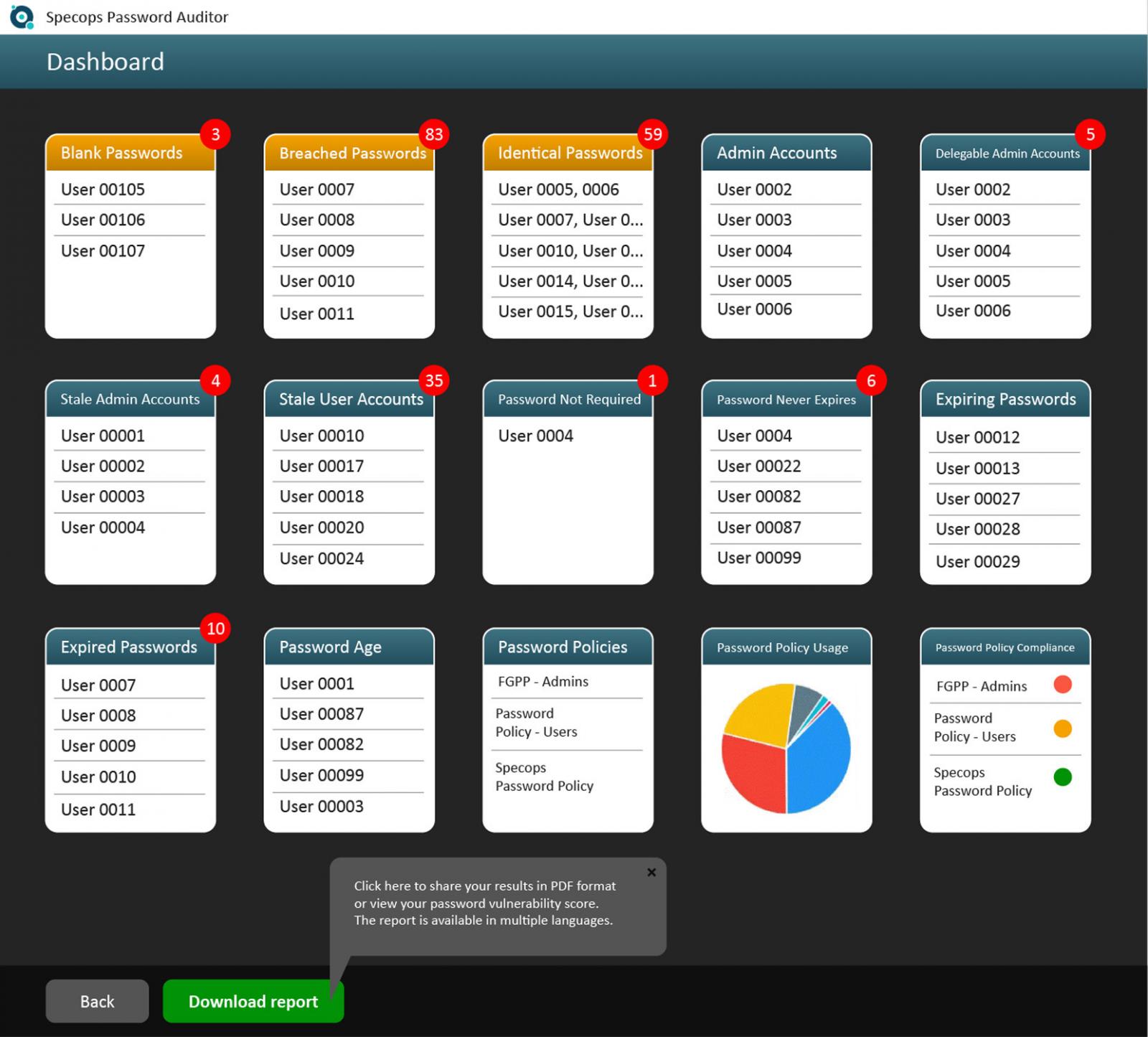
Do you know the overall password health of your organization? To perform a quick password health check for your organization, you can download and run a free scan of your Active Directory.
Perform a thorough examination of your environment with Specops Password Auditor. Scan your AD for non-compliant passwords or over 940 million compromised passwords and get a free read-only report.
This will give you a holistic view of your users and detect password vulnerabilities in your organization.
Despite the emergence of biometrics and access keys, passwords remain a key component of many business systems. To ensure the continued security of your business, it is essential to have a well-defined password policy in place.
Specops password policy reinforces standard Microsoft Active Directory password policies with compliance-focused templates, comprehensive password creation rules, and breached password protection that lets you block over 3 billion passwords compromise. With real-time feedback from end users, users can also see what is required in creating the password.
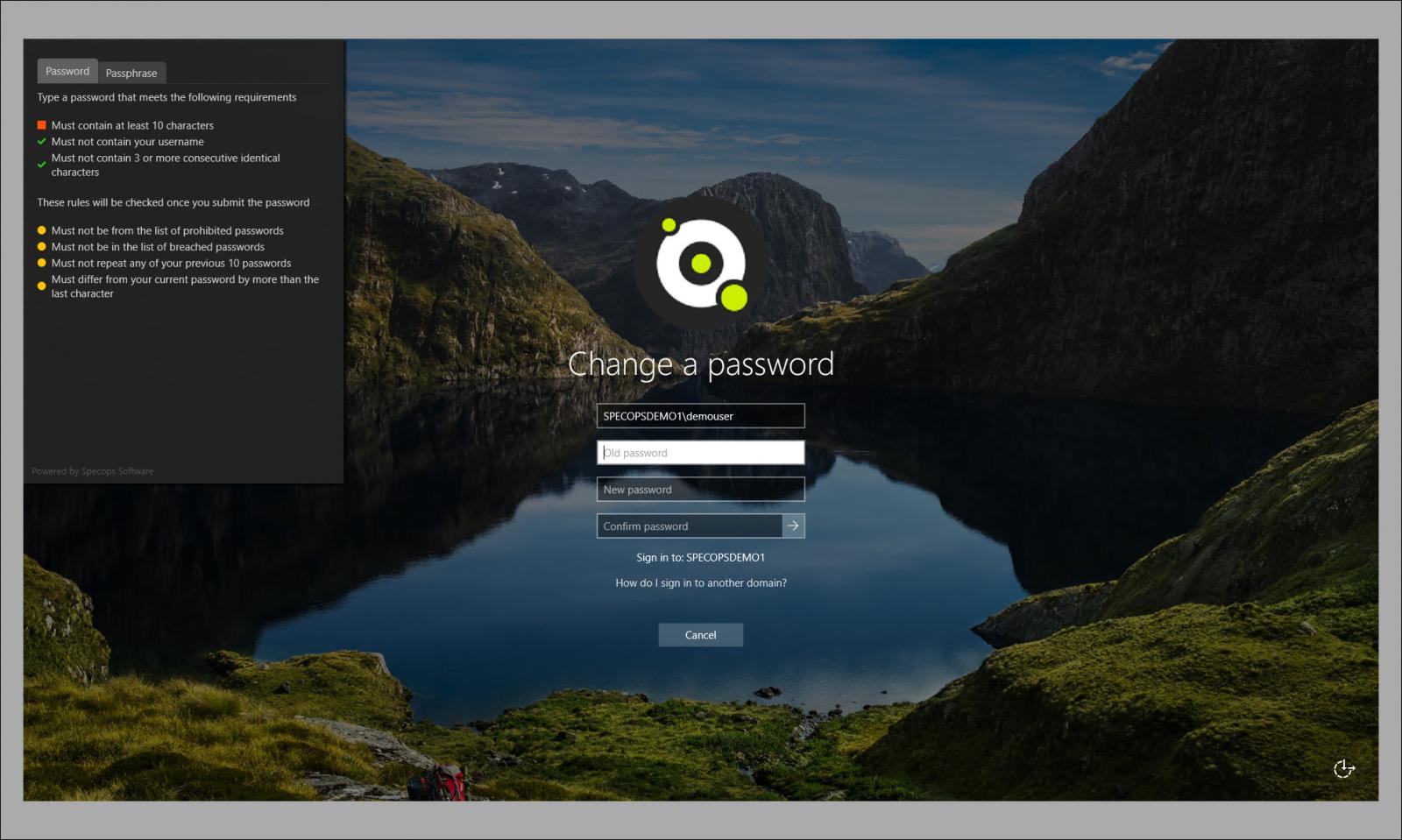
Protecting End User Passwords
Supporting end-user productivity and security while maintaining a strong security posture can be challenging. Shared and reused insecure passwords are a very real and persistent threat to any organization.
Secure password policies enforced by tools such as Specops password policy secure your environment and your end users and reduce the vulnerabilities of your organization!
Sponsored and written by Specops software
[ad_2]
Source link
