[ad_1]

Over 1,600 publicly available Docker Hub images hide malicious behavior, including cryptocurrency miners, embedded secrets that can be used as backdoors, DNS hijackers, and website forwarders.
Docker Hub is a cloud-based container library allowing users to freely search and download Docker images or upload their creations to the public library or personal repositories.
Docker images are templates for quickly and easily building containers containing ready-to-use code and applications. Therefore, those looking to set up new instances often turn to Docker Hub to quickly find an easily deployable application.
Unfortunately, due to abuse of the service by malicious actors, over a thousand malicious downloads pose serious risks to unsuspecting users who deploy malware-laden images to locally hosted or cloud-based containers. .
Many malicious images use names that disguise them as popular and trustworthy projects, so threat actors have clearly uploaded them to trick users into downloading them.
Sysdig researchers have delved into the issue, trying to gauge the extent of the problem, and have reported on images found that show some form of malicious code or mechanism.
Docker Hub Traps
In addition to images reviewed by the Docker Library Project, which have been verified for reliability, hundreds of thousands of images with unknown status are on the service.
Sysdig used its automated scanners to examine 250,000 unverified Linux images and identified 1,652 as malicious.
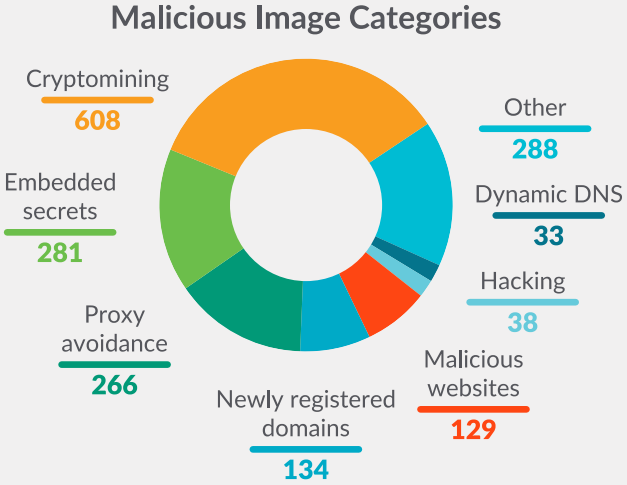
The largest category was crypto miners, found in 608 container images, targeting server resources to mine cryptocurrency for threat actors.
The second most common occurrence was images hiding embedded secrets, measuring 281 cases. The secrets embedded in these images are SSH keys, AWS credentials, GitHub tokens, NPM tokens, and others.
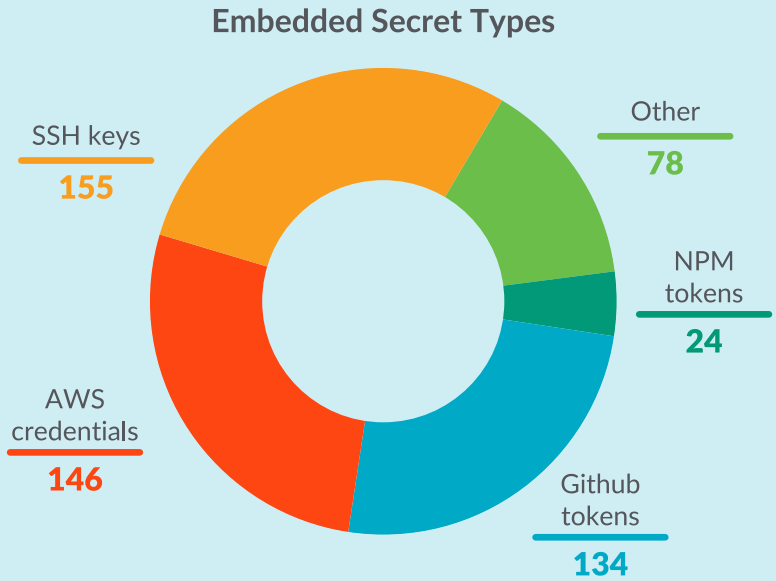
Sysdig comments that these secrets may have been left on public images by mistake or intentionally injected by the threat actor who created and uploaded them.
“By embedding an SSH key or API key in the container, the attacker can access it once the container is deployed,” Sysdig warns in The report.
“For example, uploading a public key to a remote server allows owners of the corresponding private key to open a shell and execute commands via SSH, similarly to implanting a backdoor .”
Many malicious images discovered by Sysdig used typosquatting to impersonate legitimate and trustworthy images, only to infect users with crypto-miners.
This tactic lays the groundwork for some very successful cases, like the two examples below, which have been downloaded nearly 17,000 times.
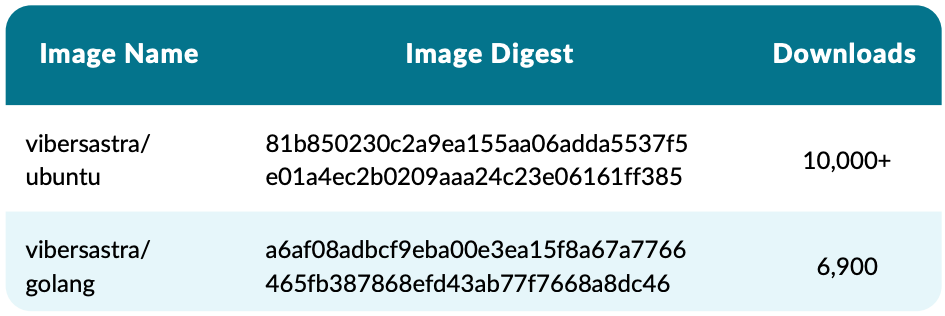
Typosquatting also ensures that users who mistype the name of a popular project will download a malicious image. So, although it does not produce a large number of victims, it still guarantees a constant stream of infections.
.png)
A growing problem
Sysdig says that in 2022, 61% of all images pulled from Docker Hub come from public repositories, a 15% increase from 2021 statistics, so the risk to users is increasing.
Unfortunately, the size of the Docker Hub public library does not allow its operators to review all uploads daily; therefore, many malicious images go unreported.
Sysdig also noticed that most threat actors only upload a few malicious images, so even if a risky image is removed and the uploader is banned, it doesn’t have a significant impact on the threat landscape of the platform.
[ad_2]
Source link
