[ad_1]

Cybersecurity vendor Sophos is posing as a new ransomware-as-a-service called SophosEncrypt, with threat actors using the company’s name for their operation.
Discovered yesterday by MalwareHunterTeamthe ransomware was initially thought to be part of a red team exercise by Sophos.
However, the Sophos X-Ops team tweeted that they did not create the encryptor and are investigating launching it.
“We found this on VT earlier and investigated. Our preliminary results show that Sophos InterceptX protects against these ransomware samples,” tweeted Sophos.
Additionally, ID Ransomware shows a submission of infected victims, indicating that this Ransomware-as-a-Service operation is active.
Although little is known about the RaaS operation and how it is promoted, a sample of the encryptor was found by MalwareHunterTeam, allowing us to get a quick look at how it works.
SophosEncrypt ransomware
The ransomware encryptor is written in Rust and uses the path ‘C:\Users\Dubinin\’ for its crates. Internally, the ransomware is named “sophos_encrypt”, so it has been dubbed SophosEncrypt, with detections already added to ID Ransomware.
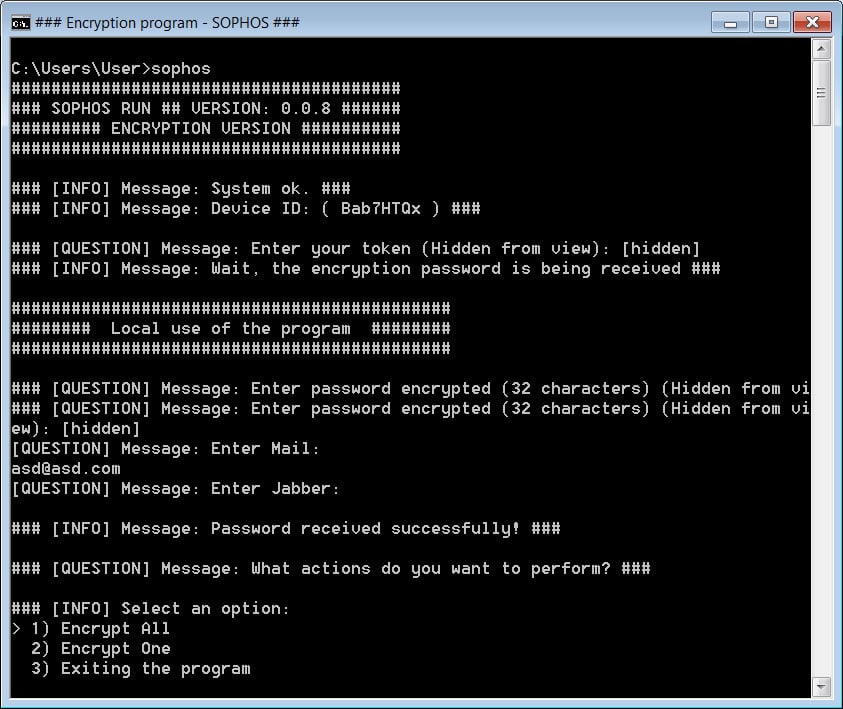
When executed, the encryptor prompts the affiliate to enter a token associated with the victim which is likely retrieved first from the ransomware management panel.
When a token is entered, the encryptor connects to 179.43.154.137:21119 and checks if the token is valid. Ransomware expert Michael Gillespie discovered that it was possible to bypass this check by disabling your network cards, effectively running the encryptor offline.
When a valid token is entered, the encryptor will prompt the ransomware affiliate for additional information to use when encrypting the device.
This information includes a contact email, jabber address and 32-character password, which Gillespie says is used as part of the encryption algorithm.
The encryptor will then ask the affiliate to encrypt a file or encrypt the entire device as shown below.
Source: BleepingComputer
When encrypting files, Gillespie told BleepingComputer that he uses AES256-CBC encryption with PKCS#7 padding.
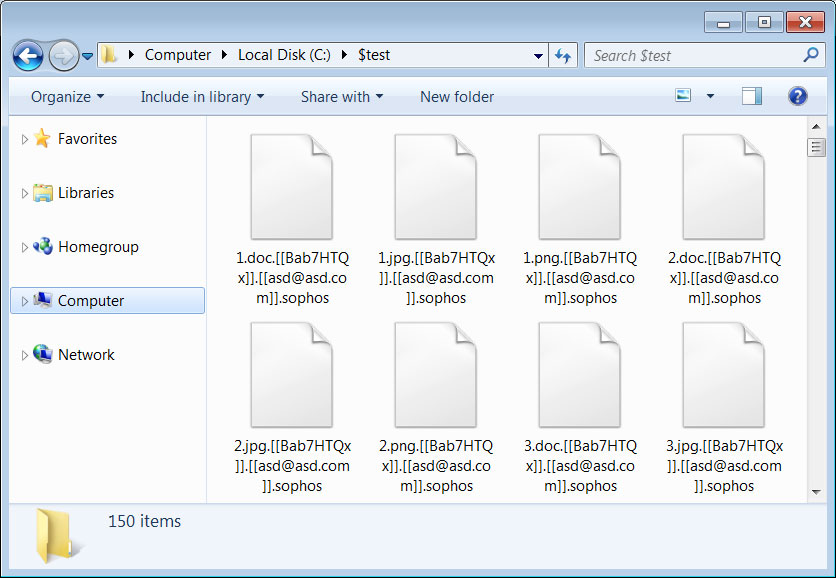
Each encrypted file will have the entered token, entered email and Sophos extension added to the name of a file in the format:.[[]].[[]].sophos. This is shown below in an encryption test by BleepingComputer.
Source: BleepingComputer
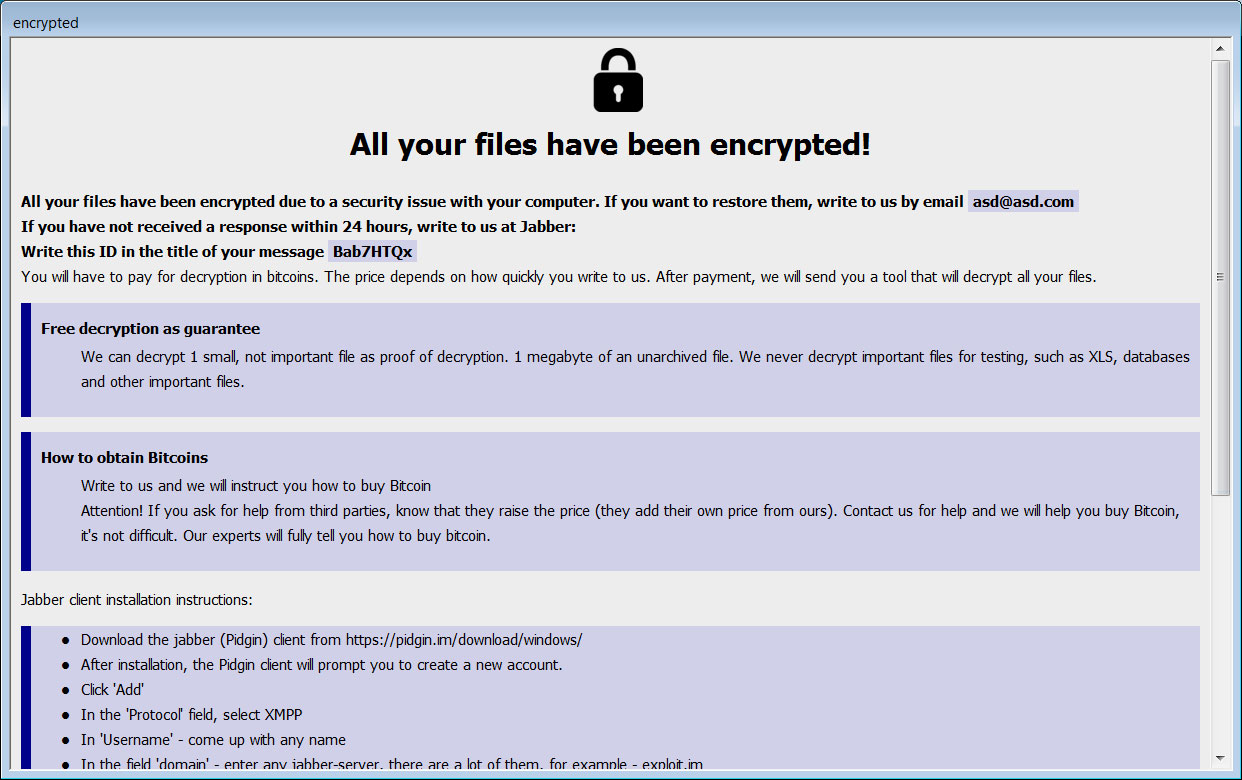
In each folder where a file is encrypted, the ransomware will create a ransom note named information.hta, which is automatically launched when the encryption is complete.
This ransom note contains information about what happened to a victim’s files and the contact information entered by the affiliate before encrypting the device.
Source: BleepingComputer
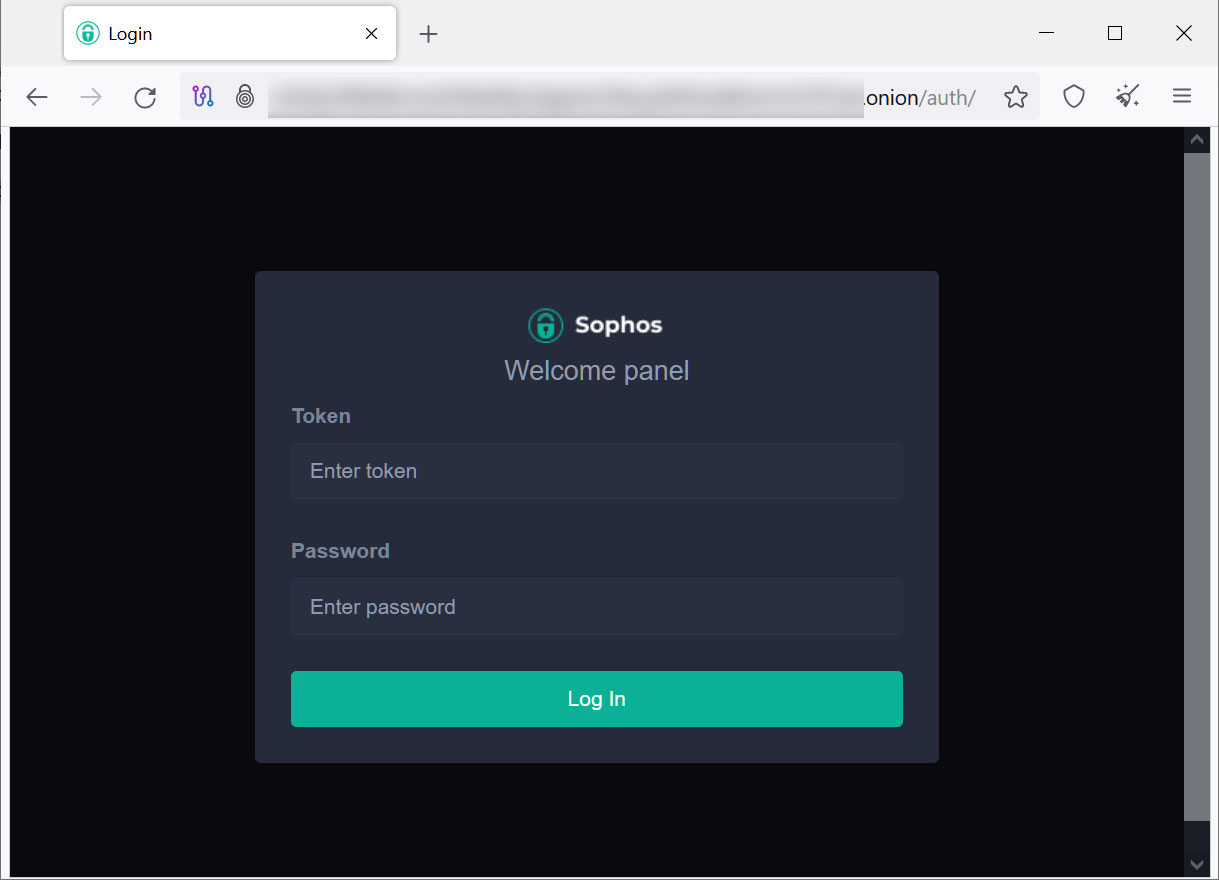
The cipher contains numerous references to a Tor site located at http://xnfz2jv5fk6dbvrsxxf3dloi6by3agwtur2fauydd3hwdk4vmm27k7ad.onion.
This Tor site is not a trading or data leak site, but rather what appears to be the affiliate panel for the ransomware-as-a-service operation.
Source: BleepingComputer
Researchers are still analyzing SophosEncrypt to see if any weaknesses could allow free file recovery.
If any encryption weaknesses or issues are found, we will post an update to this article.
[ad_2]
Source link
